AWS News Blog
DNS30 – A Visual Tool for Amazon Route 53
|
|
I became cognizant of DNS30 during the private beta test of Amazon Route 53.I own quite a few personal domains for use by me and my family and I was looking forward to managing all of the DNS entries from one location.
I tried it out and it worked just fine. In order to use DNS30 you must supply it with a set of AWS credentials. I am generally reluctant to advise others to do this because the AWS Account credentials have complete access to all of the AWS resources and API calls.
After a recent hallway conversation with the manager responsible for AWS Identify and Access Management (IAM) I decided to see if I could use IAM to enable DNS30 to use Route 53 but nothing else. It turned out to be really easy. IAM gives me the ability to create users under my AWS Account and to manage the permissions for each of these users. It turned out to be really easy.
I installed the IAM command line toolkit and used the iam-usercreate command to create a new user (dns30) and a set of keys (which I copied into a local file for safekeeping):
AKIAJQM54HFB4VGZMD3A
4J1dmFCqljhhmIh7Q0A866kmNn0ktarO7e25n5Zp
Then I gave the new user permission to access all of the Route 53 APIs and all of my Route 53 resources:
Because IAM users have no permissions by default, the dns30 user can use its credentials to access Route 53, and nothing else. My policy is called DNS_ACCESS. It Allows access to all of the Route 53 APIs (route53:*) and all of my Route 53 resources (*).
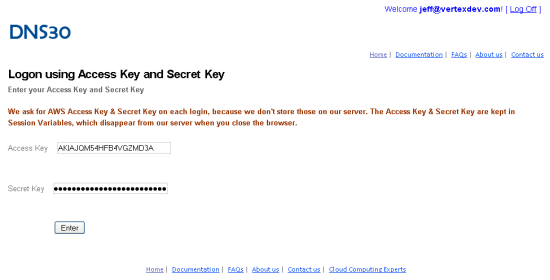
I then created an account on DNS30 and entered my IAM user credentials (not my AWS Account credentials) when the site asked for them:
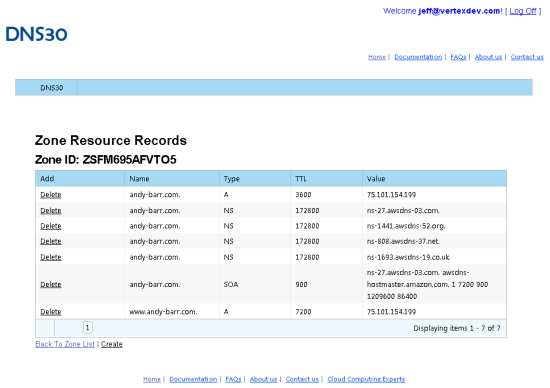
I was then able to create a Hosted Zone and populate it with the records needed to host a domain:
I could easily use IAM to create additional users for other applications. I could also create multiple users for the same application, with varied permissions.
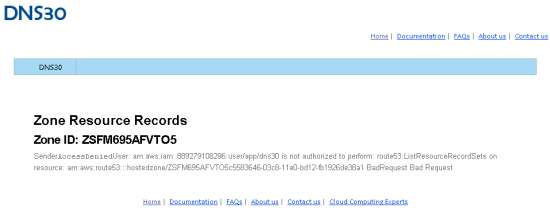
To prove to myself that nothing funny was going on behind the scenes, I deleted the DNS_ACCESS policy like this:
Then I refreshed the page on DNS30 and received (as expected) an error message:
I also tried to use my dns30 credentials to access my S3 resources using S3Fox and was (as expected), unable to do so.
I hope that you enjoy this brief introduction to IAM (I’ve got a more detailed post in works) and that you can put it to use in interesting ways. What do you think?
— Jeff;
PS – Since I wrote this post I have become aware of several other visual tools designed for use with Route 53. So far I know of tools from Ylastic and @Flagthis, the bindtoroute53.py script, and library support from Sprightlysoft, Boto, and the Route 53 Gem. I will cover these in depth sometime soon.
