AWS News Blog
New Features for Amazon CloudFront: Server Name Indication (SNI) and HTTP Redirection
Amazon CloudFront is a web service for content delivery. You can use CloudFront to deliver content to your end users with low latency, high data transfer speed, and no commitments.
I am happy to announce that CloudFront now supports Server Name Indication (SNI) for custom SSL certificates, along with the ability to take incoming HTTP requests and redirect them to secure HTTPS requests. Both of these features are available at no additional cost to all users of CloudFront.
Let’s take a look at both of these useful new features…
Server Name Indication for Custom SSL Certificates
We launched support for custom SSL certificates last year, giving you the ability to upload your own certificate to your AWS account, and to select it for use with your CloudFront distribution. This model works with any browser because we dedicate IP addresses to your SSL certificate at each CloudFront edge location. The dedicated IP addresses are necessary so that CloudFront can associate the incoming requests with the proper SSL certificate.
Today’s launch of SNI support for CloudFront gives you a second way to use your own SSL certificates with CloudFront. With the SNI extension of TLS, dedicated IP addresses are no longer necessary. This is because modern web browsers and HTTP client libraries transmit the destination host name at the beginning of the SSL handshaking process.
While most modern browsers include the SNI extension, some older ones may not. These older browsers, including Internet Explorer on Windows XP, the default browser on devices that are running Android 2.2, and Java web browsers earlier than version 1.7 running on any operating system, will not be able to load your HTTPS content. If you want to take advantage of SNI and need to support legacy browsers, you can detect them in your client code and route the HTTPS requests directly to the origin server.
You can set up SNI when you create a new distribution. You can also modify an existing distribution so that it will use SNI instead of the default CloudFront certificate or the dedicated IP addresses. The creation and modification operations can be taken care of with a couple of clicks in the AWS Management Console:
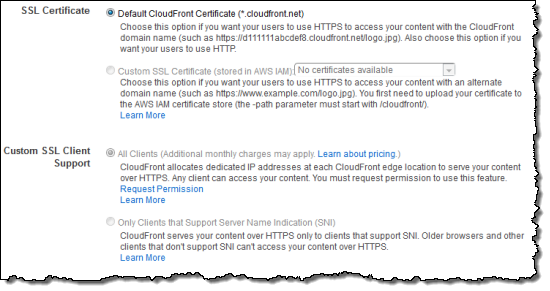
There is no extra cost for using the SNI Custom SSL feature beyond the usual data transfer and request prices for Amazon CloudFront.
If you modify a distribution that you’ve previously set up using dedicated IP addresses (the All Clients option in the console) so that it uses SNI (the Only Clients… option), the monthly charge for the dedicated IP option will be pro-rated and stop as of the date of the modification.
To learn more about this new feature and how to use it, visit the documentation on [Using Alternate Domain Names and HTTPS].
HTTP Redirection at the Edge
In many cases it is best to serve an entire web site through HTTPS. If you are moving an existing HTTP-based site to a full or partial HTTPS-based model, you can now use a CloudFront behavior to configure CloudFront to redirect HTTP requests to HTTPS:
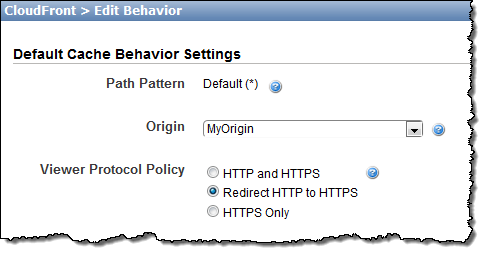
When yours users make an HTTP request for an object that’s in a distribution configured for redirection, the CloudFront edge location will return an HTTP 301 (moved permanently) status code, along with the HTTPS URL for the object. Your Viewer will then make a second request for the object, this time via HTTPS.
Both of these features are available now and you can start using them today.
— Jeff;
PS – I would like to thank everyone who has asked us to support SNI. Your feedback means a lot to us. We read it, analyze it, and use the results to prioritize our work. Please continue to send feedback on every AWS service our way!