AWS News Blog
AWS Config Rules Update: Aggregate Compliance Data Across Accounts and Regions
As I have discussed in the past, sophisticated AWS customers invariably control multiple AWS accounts. Some of these are the results of acquisitions or a holdover from bottom-up, departmental adoption of cloud computing. Others create multiple accounts in order to isolate developers, projects, or departments from each other. We strongly endorse this as a best practice, and back it up with cross-account features in many AWS services, as well as AWS Organizations for policy-based management that spans accounts. Many of these customers also make great use of AWS Config and use Config Rules (both their own and those supplied by Config) to check their AWS resources for compliance.
Aggregate Across Accounts and Regions
Today we are making Config Rules even more useful by adding the ability to aggregate the compliance data produced by their rules across multiple AWS accounts and/or Regions. The aggregated data can then be viewed in a single dashboard, making this a great way to improve governance and compliance. Even better, the aggregation and dashboard are available at no charge to all AWS Config users!
I’ll show you how to set this up in a moment. First, let’s define a couple of terms:
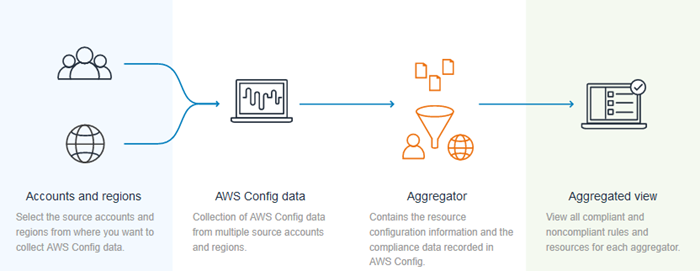
Aggregator – This is a new Config resource. It identifies the sources (accounts and regions) of the compliance data to be aggregated. Multiple aggregators can be used simultaneously, giving you the ability to fine-tune your governance and compliance model.
Aggregator account – This is an AWS account that owns one or more aggregators.
Source account – This is an AWS account that has compliance data to be aggregated.
Aggregated view – A dashboard that shows compliant and non-compliant rules for an aggregator.
Here’s how it all fits together:
Setting up Aggregation
Let’s set up aggregation for some AWS Config data! The first steps take place in the aggregator account. I open the Config Console, find the Aggregated View section and click Aggregators:
I review the list of Aggregators, and click Add aggregator to make a new one:
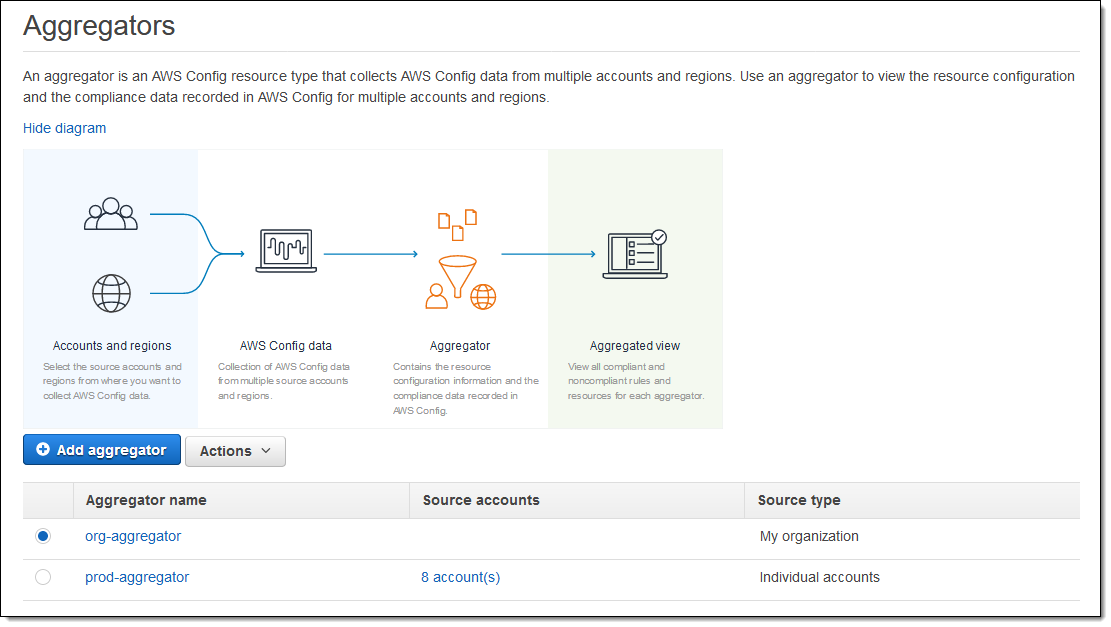
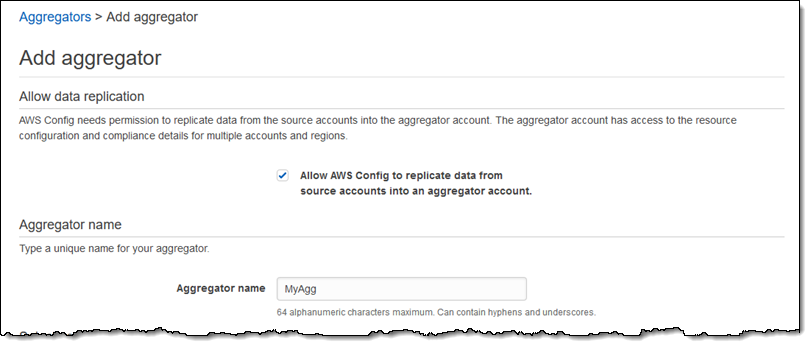
I grant AWS Config permission to replicate data from the source accounts and enter a name for my aggregator (MyAgg):
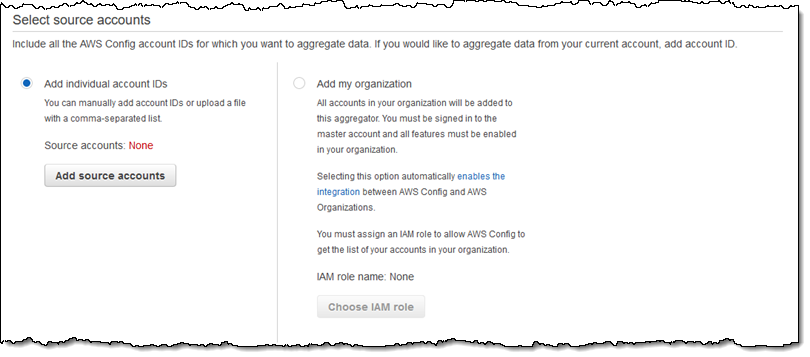
Next, I select the source accounts. I have three options here: I can manually add the account IDs, upload a file that contains a comma-separated list, or add all of the accounts in my AWS Organization:
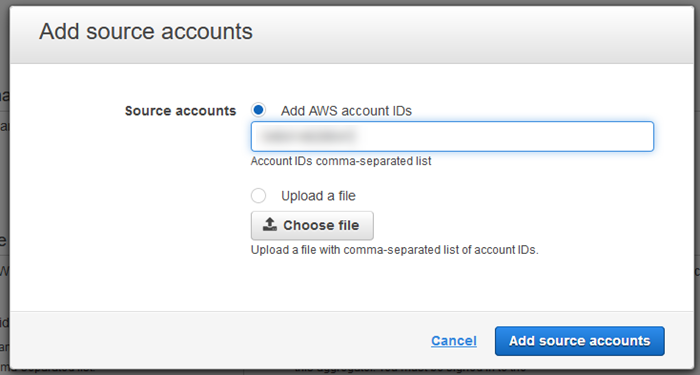
I click on Add source accounts to manually add one account, enter the ID, and click Add source accounts:
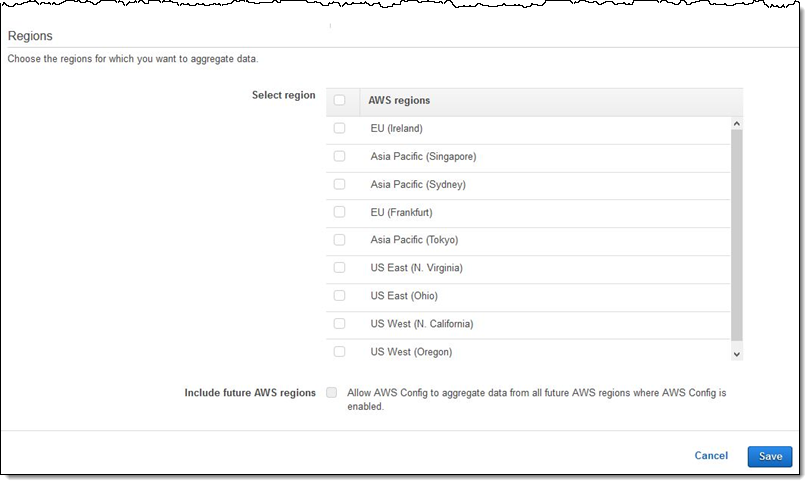
Next, I choose the regions of interest, with the option to select current regions as well as future ones, then click Save to move ahead:
The next step takes place in the source account, within the Config Console. An Authorization request appears:
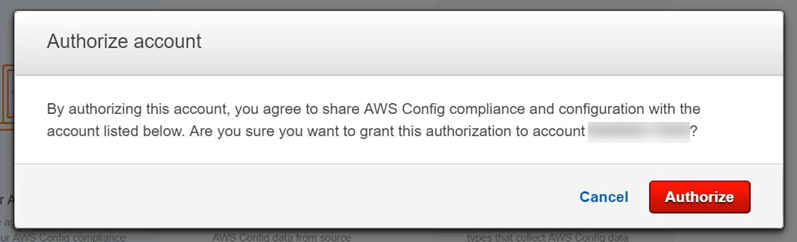
And I confirm it:
You can use CloudFormation StackSets to enable authorization programmatically across all source accounts. Also note that the authorization step is not needed if you choose to aggregate all accounts in your AWS Organization.
Compliance data from the source account begins to flow to the aggregator account and becomes visible in the Console, generally within 2-5 minutes:
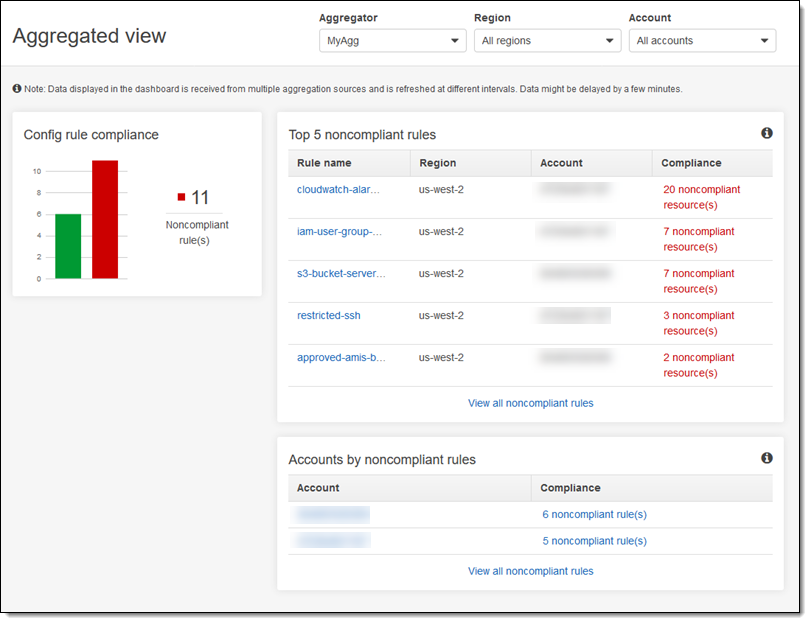
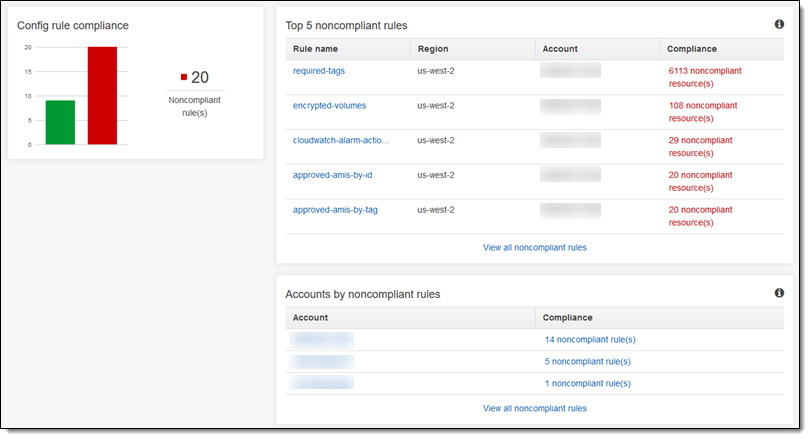
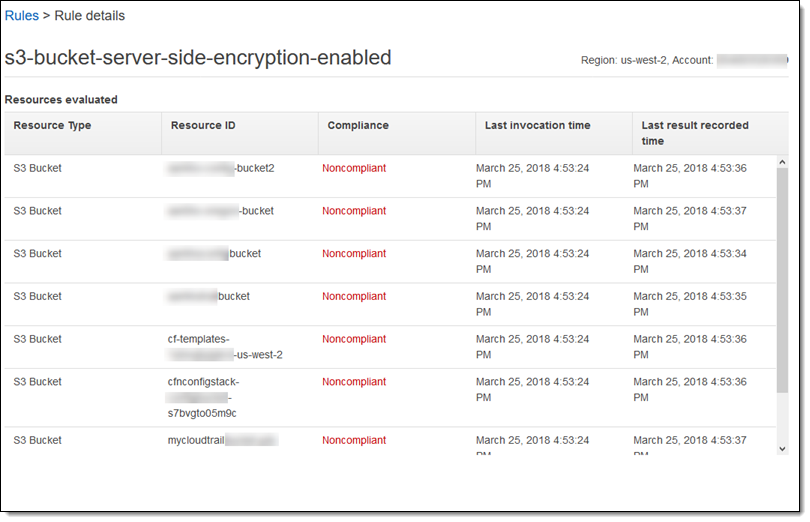
As you can see, I have a multitude of filtering options! I can focus the view on a particular region or account, and I can see which rules or accounts have the most issues to address. For example, I can see all of the buckets that do not have server-side encryption enabled:
I can also look at the overall compliance situation for an account, seeing both compliant and non-compliant resources:
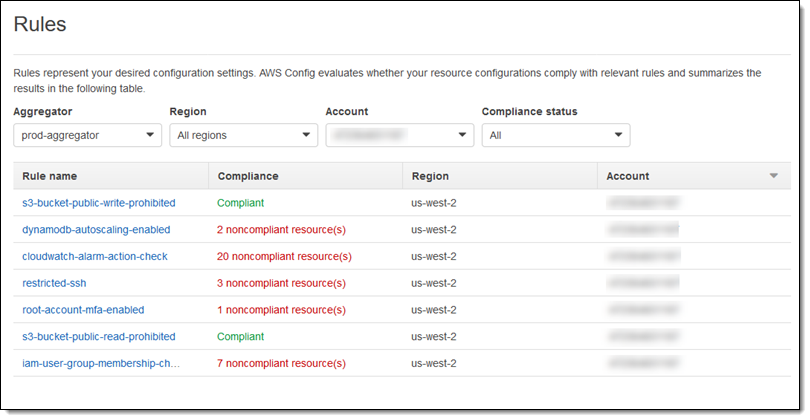
Things to Know
This new feature is available today in the US East (N. Virginia), US East (Ohio), US West (Oregon), US West (N. California), Europe (Ireland), Europe (Frankfurt), Asia Pacific (Tokyo), Asia Pacific (Sydney), and Asia Pacific (Singapore) regions at no charge and you can start using it today. You pay for the use of Config and Config Rules as usual.
The multi-account, multi-region data aggregation capability in AWS Config allows you to view the compliance status of your accounts from a central account. It assumes that you have already enabled Config and Config Rules across your accounts (you can use CloudFormation StackSets to distribute and deploy your Config Rules across multiple accounts).
— Jeff;