AWS News Blog
Amazon VPC – Additional VPN Features
The Amazon Virtual Private Cloud (VPC) gives you the power to create a private, isolated section of the AWS Cloud. You have full control of network addressing. Each of your VPCs can include subnets (with access control lists), route tables, and gateways to your existing network and to the Internet.
You can connect your VPC to the Internet via an Internet Gateway and enjoy all the flexibility of Amazon EC2 with the added benefits of Amazon VPC. You can also setup an IPsec VPN connection to your VPC, extending your corporate data center into the AWS Cloud. Today we are adding two options to give you additional VPN connection flexibility:
- You can now create Hardware VPN connections to your VPC using static routing. This means that you can establish connectivity using VPN devices that do not support BGP such as Cisco ASA and Microsoft Windows Server 2008 R2. You can also use Linux to establish a Hardware VPN connection to your VPC. In fact, any IPSec VPN implementation should work.
- You can now configure automatic propagation of routes from your VPN and Direct Connect links (gateways) to your VPC’s routing tables. This will make your life easier as you wont need to create static route entries in your VPC route table for your VPN connections. For instance, if youre using dynamically routed (BGP) VPN connections, your BGP route advertisements from your home network can be automatically propagated into your VPC routing table.
If your VPN hardware is capable of supporting BGP, this is still the preferred way to go as BGP performs a robust liveness check on the IPSec tunnel. Each VPN connection uses two tunnels for redundancy; BGP simplifies the failover procedure that is invoked when one VPN tunnel goes down.
Static Routing
We added the static routing option for a number of reasons. First, BGP can be difficult to set up and to manage, and we don’t want to ask you to go to all of that trouble if all you want to do is set up a VPN connection to a VPC. Second, some firewalls and entry-level routers support IPSec but not BGP. These devices are very popular in corporate branch offices. As I mentioned above, this change dramatically increases the number of VPN devices that can be used to connect to a VPC. We have tested the static routing “No BGP” option with devices from Cisco, Juniper, Yamaha, Netgear, and Microsoft. We’ve assembled a list of VPN devices that weve tested for dynamic and statically routed VPN connections
You can select this option when you create the VPN connection between a VPN and one of your customer gateways:
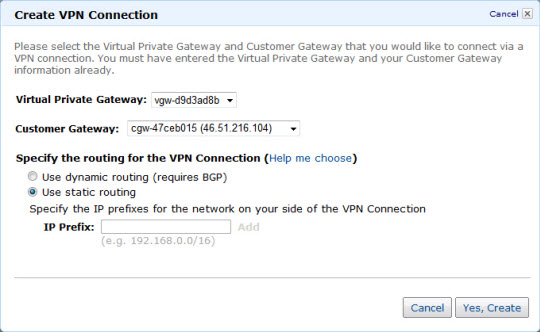
If you choose this option you must also enter one or more routes (CIDR addresses) to indicate which traffic is to be routed back to your customer gateways (your home network).
For client-side redundancy, you can use two customer gateway devices (two VPN connections). That way, if your gateway device goes down, or needs maintenance, the other one can continue to carry your traffic into the VPC. On the AWS side, we have multiple redundant VPN concentrators to handle failover in case of device failure.
Route Propagation
You can automatically propagate your VPN Connection routes (whether statically entered or advertised via BGP) to your VPC route table:
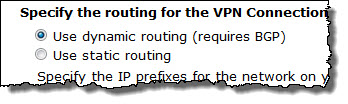
In order to enable this option for a particular routing table, you must establish an association between the table and a gateway like this:
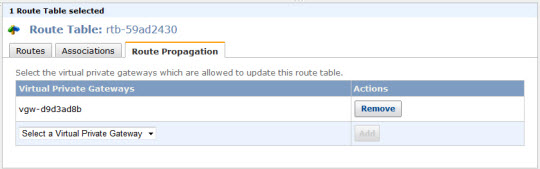
You can also arrange to update multiple routing tables from the same virtual private gateway.
As you can see, you can access these new VPN features from the AWS Management Console. They are also accessible through the VPC APIs and the command line tools.
— Jeff;
- You can now create Hardware VPN connections to your VPC using static routing. This means that you can establish connectivity using VPN devices that do not support BGP such as Cisco ASA and Microsoft Windows Server 2008 R2. You can also use [ews1] Linux to establish a Hardware VPN connection to your VPC. In fact, any IPSec VPN implementation should work.
[ews1]We use the terms hardware and software VPNs to refer to the termination point in the VPC. hardware VPN means it terminates on hardware in the VPC, software means it terminates on an instance in VPC. I dont want to confuse people by using the term software here to refer to the customer side initiation point.