Guidance for Tactical Edge Application Deployment on AWS
Overview
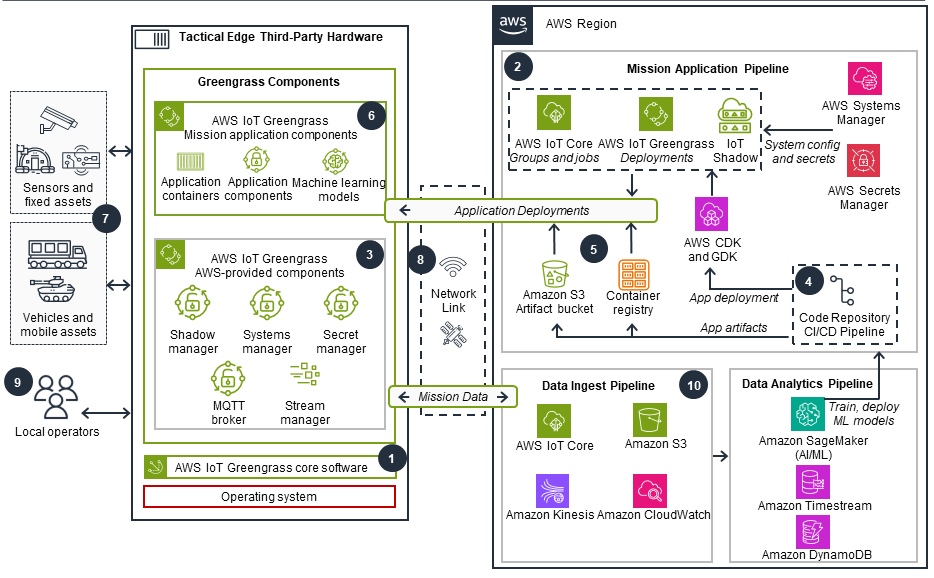
This Guidance shows two architectural patterns for deploying applications in tactical edge environments on AWS using third-party hardware devices and platforms. The term "edge" refers to compute, network, and storage capabilities that operate outside AWS Regions, often in scenarios where communication with the cloud may be limited by low bandwidth, intermittent connectivity, or extended periods of disconnection. In addition to establishing a foundational tactical edge architecture, this Guidance offers deployment patterns that use both native AWS Internet of Things (IoT) services and Kubernetes, an open-source container orchestration system. AWS customers can use this to reliably deploy mission-critical applications in tactical edge environments with limited or intermittent network connectivity like mobile command centers, tactical vehicles, and operating bases.
How it works
Deploy applications onto third-party hardware
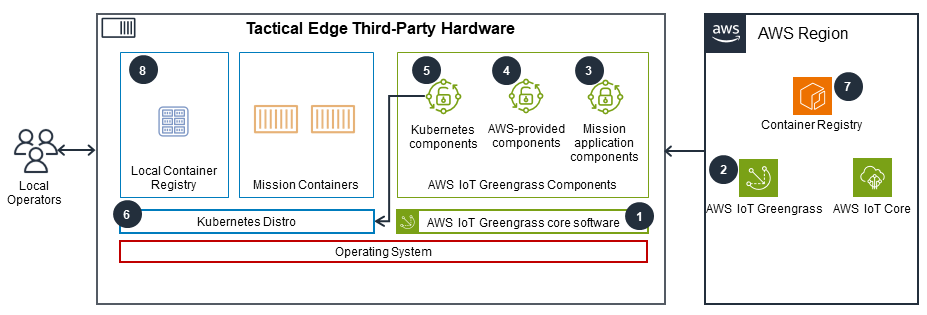
This architecture extends the deployment onto third-party hardware to a single-node Kubernetes cluster on the third-party hardware.
Kubernetes-based deployment
This architecture extends the deployment onto third-party hardware to a single-node Kubernetes cluster on the third-party hardware.
Well-Architected Pillars
The architecture diagram above is an example of a Solution created with Well-Architected best practices in mind. To be fully Well-Architected, you should follow as many Well-Architected best practices as possible.
Disclaimer
Did you find what you were looking for today?
Let us know so we can improve the quality of the content on our pages