- AWS Solutions Library›
- Guidance for Securing Sensitive Data in RAG Applications Using Amazon Bedrock
Guidance for Securing Sensitive Data in RAG Applications Using Amazon Bedrock
Overview
This Guidance demonstrates two security patterns for protecting sensitive data in retrieval augmented generation (RAG) applications built with Amazon Bedrock. It shows how to implement both a zero-trust architecture with pre-ingestion data redaction and a role-based access control system for precise data access management. The Guidance helps organizations maintain data privacy, regulatory compliance, and security by leveraging AWS AI services and integrated encryption. This approach helps ensure sensitive information remains protected throughout the RAG workflow, from initial data ingestion through final presentation, while maintaining system functionality and data integrity.
Benefits
Deploy an intelligent pipeline that automatically detects and redacts PII while providing secondary verification through Amazon Macie. Reduce risk exposure while maintaining operational efficiency.
Implement role-based access controls and guardrails to ensure users access only appropriate information. Confidently share organizational knowledge while protecting sensitive content.
Establish automated security controls with multi-layer verification and comprehensive audit trails. Maintain regulatory compliance while accelerating document processing for RAG applications.
How it works
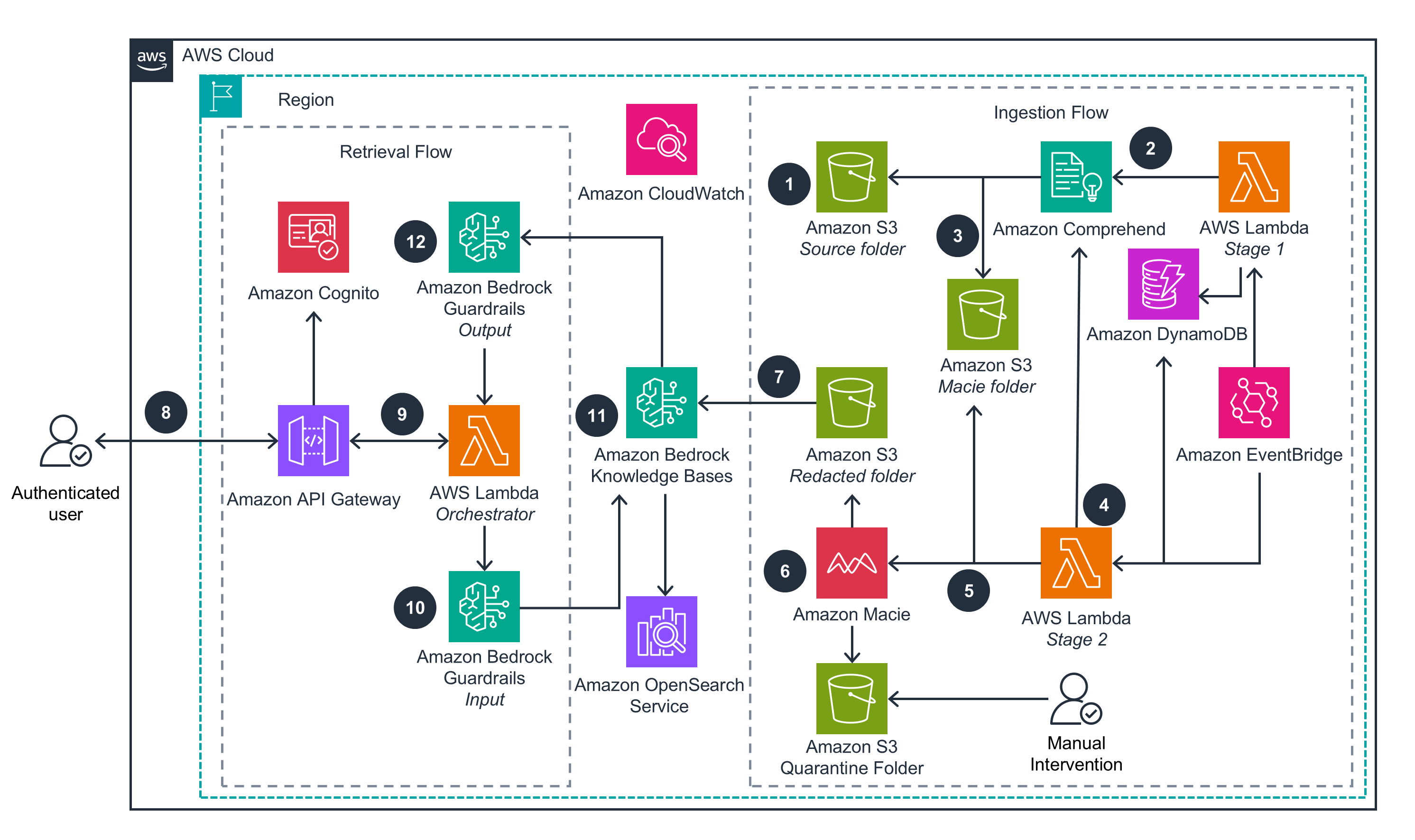
Data redaction at storage level
This architecture diagram shows how customers can safely ingest sensitive documents through automated redaction and verification processes while enabling secure, guardrail-protected access to their knowledge base without compromising sensitive information.
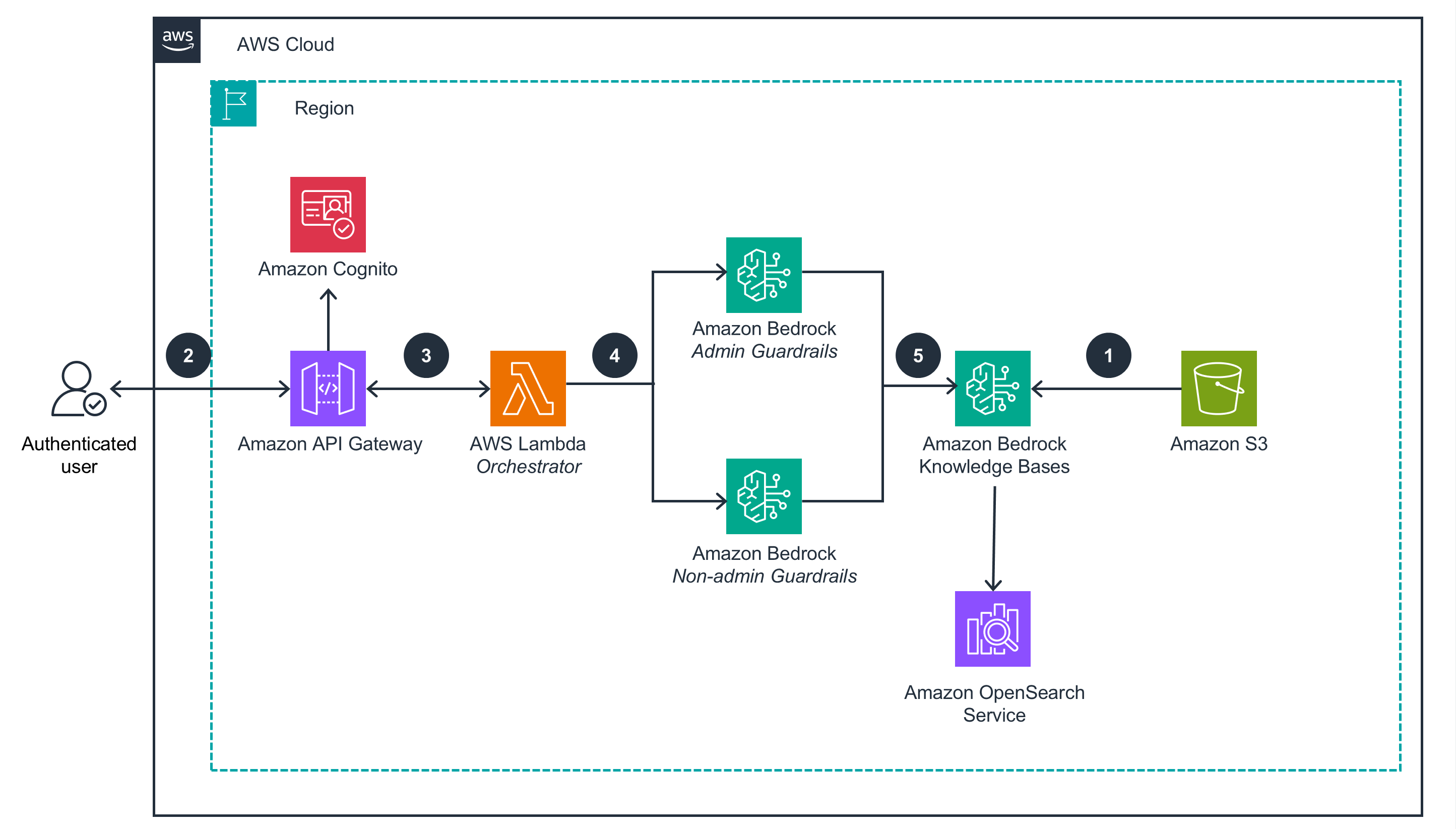
Role based access to sensitive data
This architecture diagram shows how customers can implement role-based access control for sensitive data in RAG applications using metadata filtering and personalized guardrails, ensuring users only access information appropriate for their authorization level while maintaining the security of sensitive content.
Deploy with confidence
Everything you need to launch this Guidance in your account is right here
We'll walk you through it
Dive deep into the implementation guide for additional customization options and service configurations to tailor to your specific needs.
Let's make it happen
Ready to deploy? Review the sample code on GitHub for detailed deployment instructions to deploy as-is or customize to fit your needs.
Disclaimer
The sample code; software libraries; command line tools; proofs of concept; templates; or other related technology (including any of the foregoing that are provided by our personnel) is provided to you as AWS Content under the AWS Customer Agreement, or the relevant written agreement between you and AWS (whichever applies). You should not use this AWS Content in your production accounts, or on production or other critical data. You are responsible for testing, securing, and optimizing the AWS Content, such as sample code, as appropriate for production grade use based on your specific quality control practices and standards. Deploying AWS Content may incur AWS charges for creating or using AWS chargeable resources, such as running Amazon EC2 instances or using Amazon S3 storage.
References to third-party services or organizations in this Guidance do not imply an endorsement, sponsorship, or affiliation between Amazon or AWS and the third party. Guidance from AWS is a technical starting point, and you can customize your integration with third-party services when you deploy the architecture.
Did you find what you were looking for today?
Let us know so we can improve the quality of the content on our pages