- AWS›
- AWS Blogs
AWS Blogs
Top announcements of AWS re:Invent 2025: Key breakthrough cloud innovations
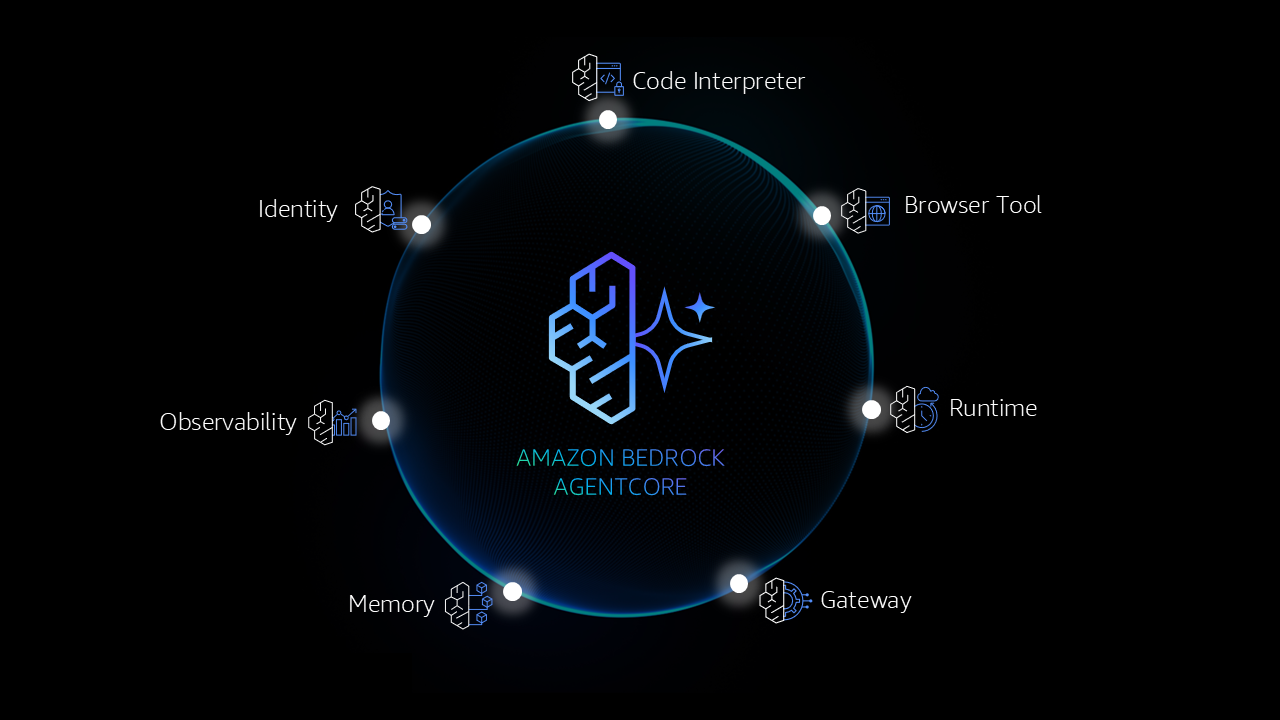
Explore major AWS innovations across AI, compute, infrastructure, security, analytics, and more.. From frontier AI models and intelligent agents to enhanced infrastructure solutions, learn how these key announcements can help you build, operate, and transform your business in the cloud.

Newest posts
Loading
Loading
Loading
Loading
Loading
Loading
Loading
Loading
Loading
Loading
Loading
Loading
Loading