AWS News Blog
Elastic Load Balancing Update – More Ports & Additional Fields in Access Logs
Many AWS applications use Elastic Load Balancing to distribute traffic to a farm of EC2 instances. An architecture of this type is highly scalable since instances can be added, removed, or replaced in a non-disruptive way. Using a load balancer also gives the application the ability to keep on running if an instance encounters an application or system problem of some sort.
Today we are making Elastic Load Balancing even more useful with the addition of two new features: support for all ports and additional fields in access logs.
Support for All Ports
When you create a new load balancer, you need to configure one or more listeners for it. Each listener accepts connection requests on a specific port. Until now, you had the ability to configure listeners for a small set of low-numbered, well-known ports (25, 80, 443, 465, and 587) and to a much larger set of ephemeral ports (1024-65535).
Effective today, load balancers that run within a Virtual Private Cloud (VPC) can have listeners for any port (1-65535). This will give you the flexibility to create load balancers in front of services that must run on a specific, low-numbered port.
You can set this up in all of the usual ways: the ELB API, AWS Command Line Interface (AWS CLI) / AWS Tools for Windows PowerShell, a CloudFormation template, or the AWS Management Console. Here’s how you would define a load balancer for port 143 (the IMAP protocol):
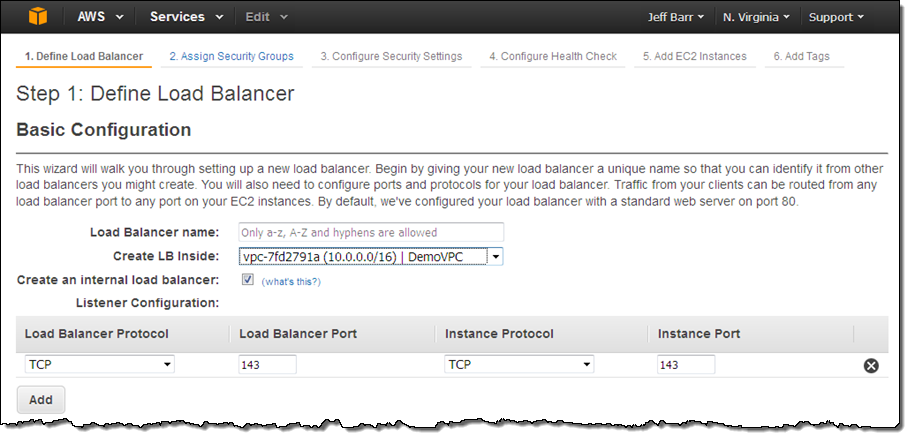
To learn more, read about Listeners for Your Load Balancer in the Elastic Load Balancing Documentation.
Additional Fields in Access Logs
You already have the ability to log the traffic flowing through your load balancers to a location in S3:
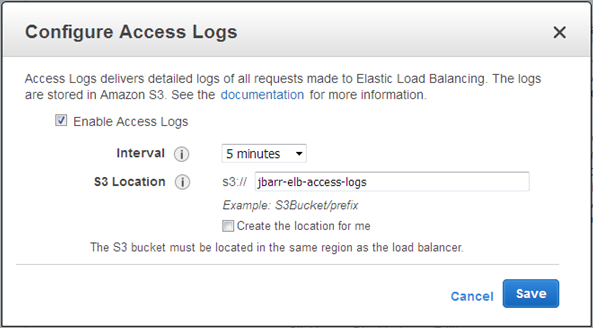
In order to allow you to know more about this traffic, and to give you some information that will be helpful as you contemplate possible configuration changes, the access logs now include some additional information that is specific to a particular protocol. Here’s the scoop:
- User Agent – This value is logged for TCP requests that arrive via the HTTP and HTTPS ports.
- SSL Cipher and Protocol – These values are logged for TCP requests that arrive via the HTTPS and SSL ports.
You can use this information to make informed decisions when you think about adding or removing support for particular web browsers, ciphers, or SSL protocols. Here’s a sample log entry:
2015-05-13T23:39:43.945958Z my-loadbalancer 192.168.131.39:2817 10.0.0.1:80 0.000086 0.001048 0.001337 200 200 0 57 "GET https://www.example.com:443/ HTTP/1.1" "curl/7.38.0" DHE-RSA-AES128-SHA TLSv1.2
You can also use tools from AWS Partners to view and analyze this information. For example, Splunk shows it like this:
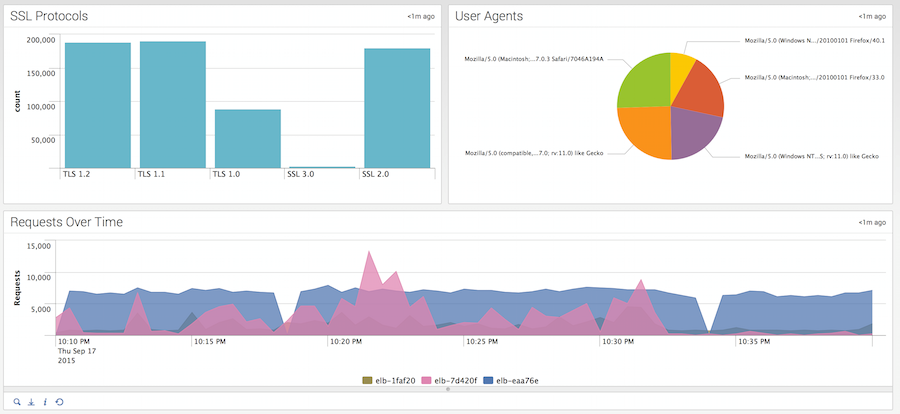
And Sumo Logic shows it like this:
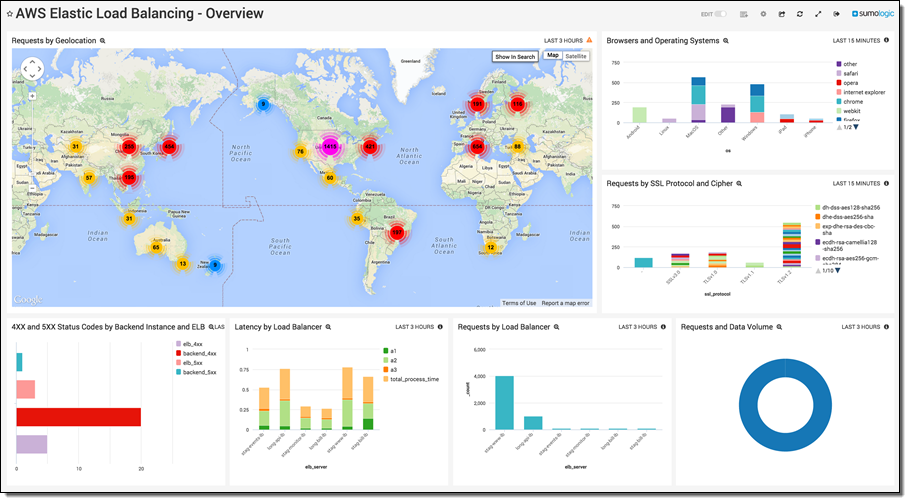
To learn more about access logging, read Monitor Your Load Balancer Using Elastic Load Balancing Access Logs.
Both of these features are available now and you can start using them today!
— Jeff;