Overview
How it works
Amazon QuickSight template
There are two deployment modes for this Guidance, the first one uses an Amazon QuickSight template, the second uses an asset bundle API. This architecture diagram displays the configuration of deploying a QuickSight template. For details on the asset bundle API deployment mode, refer to the next tab.
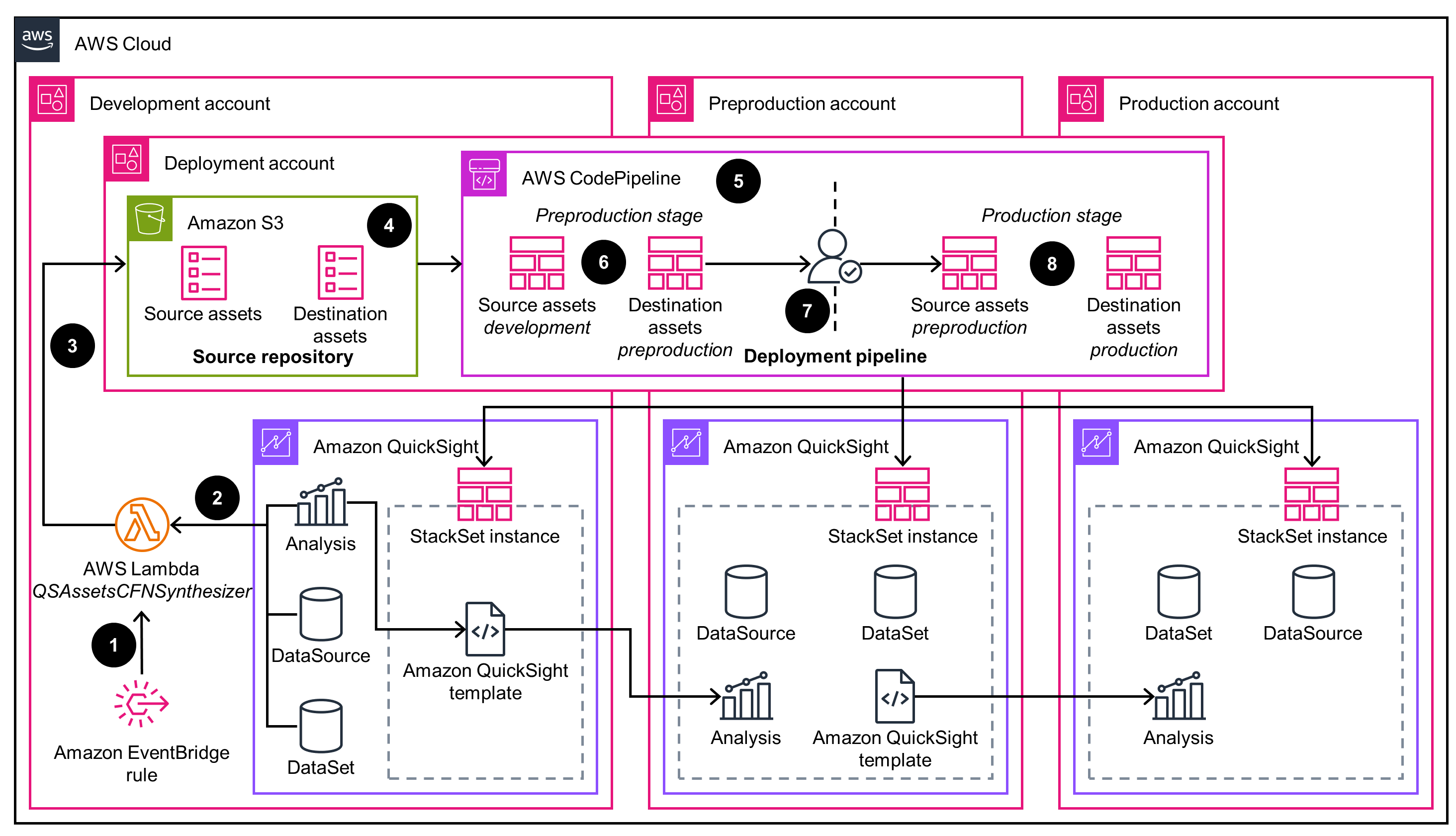
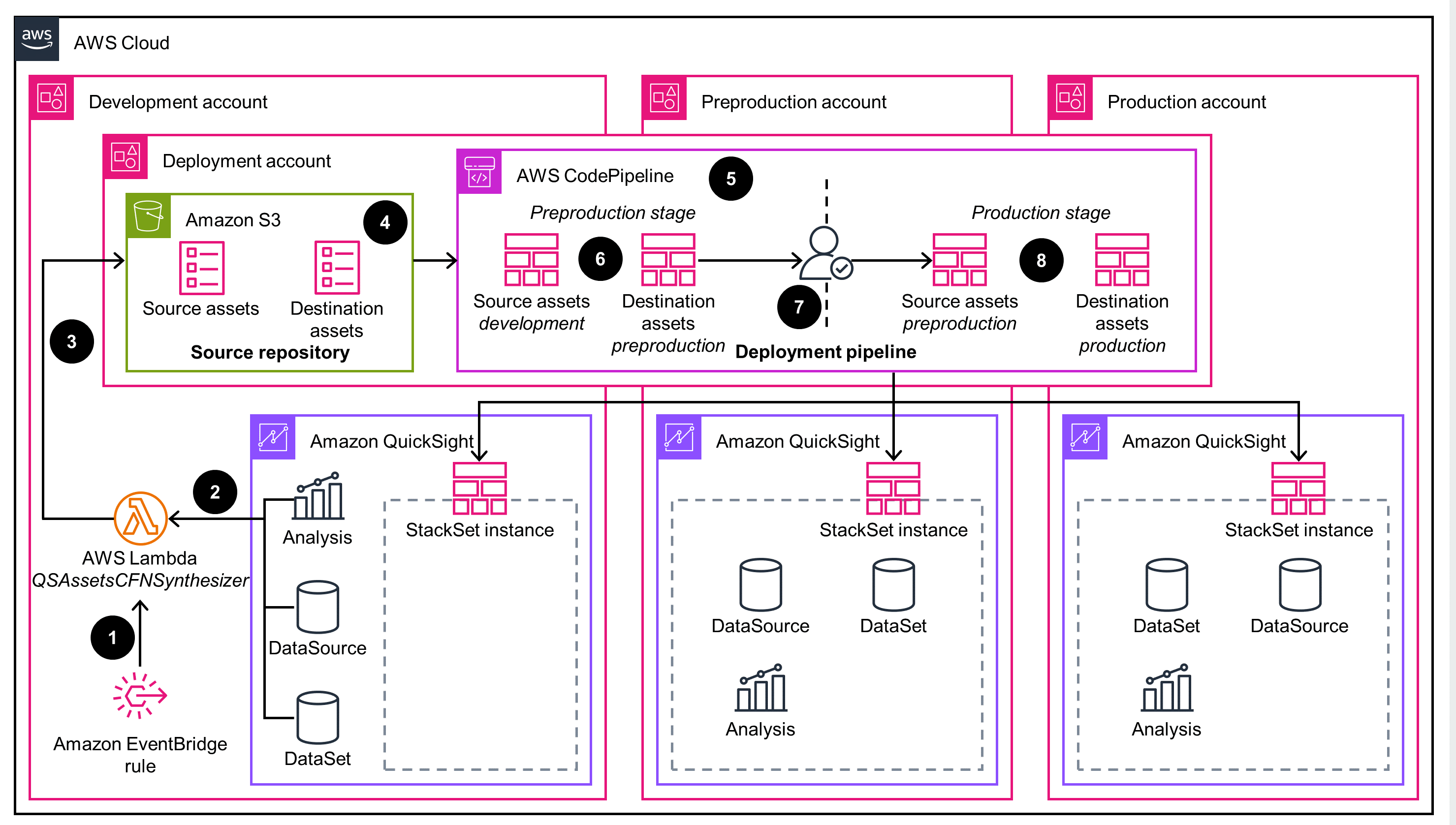
Asset Bundle API
This architecture diagram displays the asset bundle API deployment mode.
Well-Architected Pillars
The architecture diagram above is an example of a Solution created with Well-Architected best practices in mind. To be fully Well-Architected, you should follow as many Well-Architected best practices as possible.
Deploy with confidence
Ready to deploy? Review the sample code on GitHub for detailed deployment instructions to deploy as-is or customize to fit your needs.
Disclaimer
Did you find what you were looking for today?
Let us know so we can improve the quality of the content on our pages