AWS News Blog
New AWS Feature – MFA-Protected API Access
Today’s guest blogger is Kai Zhao, a Product Manager on the AWS Identity and Access Management team. Kai brings word of a powerful new IAM feature.
— Jeff;
Introduction
In 2009, we introduced AWS Multi-Factor Authentication (MFA), a security feature that requires users to prove physical possession of an MFA device by providing a valid MFA code in addition to their username and password when signing in to AWS websites.
Last November, we introduced AWS virtual MFA, which enabled MFA functionality on your smartphone, tablet, or computer running any application that supports the open OATH TOTP standard.
Today, we’re announcing MFA-protected API access, which extends AWS MFA protection to AWS service APIs. You can now enforce MFA authentication for AWS service APIs via AWS Identity and Access Management (IAM) policies. This provides an extra layer of security over powerful operations that you designate, such as terminating Amazon EC2 instances or reading sensitive data stored in Amazon S3.
How do I Get Started with MFA-Protected API Access?
You can get started in two simple steps:
- Assign an MFA device to your IAM users. You can get AWS Virtual MFA for no additional cost, which enables you to use any OATH TOTP-compatible application on your smartphone, tablet, or computer. Alternatively, you can purchase a hardware MFA key fob from Gemalto, a third-party provider.
- Add an MFA-authentication requirement to an IAM access policy. You can attach these access policies to IAM users, IAM groups, or resources that support Access Control Lists (ACLs): Amazon S3 buckets, SQS queues, and SNS topics.
How do I write an IAM policy to require MFA?
The policy below is a basic example of how to enforce MFA authentication on users attempting to call the Amazon EC2 API. Specifically, it grants access only if the user authenticated with MFA within the last 300 seconds.
“Statement” : [ {
“Action” : [ “ec2:*” ] ,
“Effect” : “Allow” ,
“Resource” : [ “*” ] ,
“Condition”:{
“NumericLessThan”:{“aws:MultiFactorAuthAge”:“300”}
}
}
]
}
This policy utilizes a new condition key, aws:MultiFactorAuthAge, whose value indicates the number of seconds since MFA authentication. If the condition matches, i.e. the value of aws:MultiFactorAuthAge is less than 300 seconds at the time of the API call, then access is granted.
For more information on writing such policies (including Deny examples, which can be slightly more tricky, or how to set policies that check for MFA authentication irrespective of freshness), see the IAM documentation.
How MFA-Protected API Access Works
MFA-protected API access simply requires users to enter a valid MFA code before using certain functions designated by account administrators. The diagram below details how the process works in the programmatic use case. Because the AWS Management Console calls AWS service APIs, you can enforce MFA on APIs regardless of access path, either from programmatic API calls or via the console user interface.
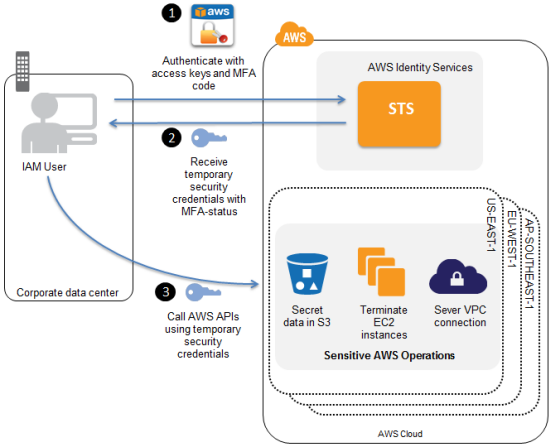
Step 1: MFA-protected API access utilizes temporary security credentials, which can be used just like long-term access keys to sign requests to AWS APIs. The process to request temporary security credentials is largely unchanged, except the user enters an MFA code into your application that requests temporary security credentials on behalf of the user.
Step 2: If the MFA authentication succeeds, the application receives temporary security credentials that include MFA-authenticated status.
Step 3: The application calls APIs on behalf of the user using the temporary security credentials acquired in Step 2. As part of the authorization process, AWS will validate the credentials and the MFA authentication.
Price = No Additional Cost
MFA-protected API access is a feature of IAM available at no extra cost. Only pay for other AWS services that you or your IAM users use.
Once again, you can Visit the IAM documentation to learn more. Were always interested in hearing about your use case, so please let us know what you think!
Kai Zhao
Product Manager AWS Identity and Access Management