- Home›
- AWS Identity›
- Data perimeters on AWS
Data perimeters on AWS
What is a data perimeter?
A data perimeter is a set of permissions guardrails in your AWS environment you use to help ensure that only your trusted identities are accessing trusted resources from expected networks. Data perimeter guardrails are meant to serve as always-on boundaries to help protect your data across a broad set of AWS accounts and resources. These organization-wide guardrails do not replace your existing fine grained access controls. Instead, they help improve your security strategy by ensuring that all AWS Identity and Access Management (IAM) users, roles, and resources adhere to a set of defined security standards. Data perimeter guardrails work alongside AWS Well-Architected Framework security design principles and other security best practices to strengthen your overall security posture.
- Explore data perimeters in AWS Identity and Access Management (IAM) documentation.
- Consult the Data perimeter policy examples GitHub repo for service specific considerations when implementing data perimeters in your environment.
- Learn from customers implementations of data perimeter controls for specific use cases.
How it works
To establish data perimeters, define your control objectives first and implement those objectives by using service control policies (SCPs), resource control policies (RCPs), and VPC endpoint policies. Then, apply these policies as data perimeter guardrails in your AWS organization.
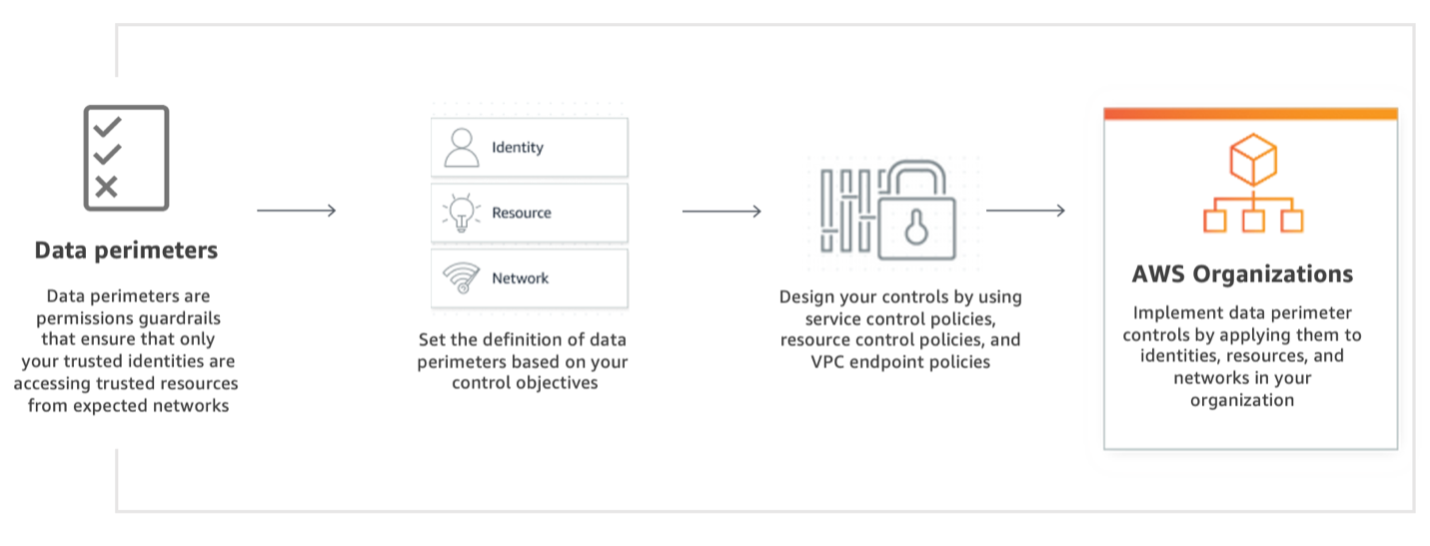
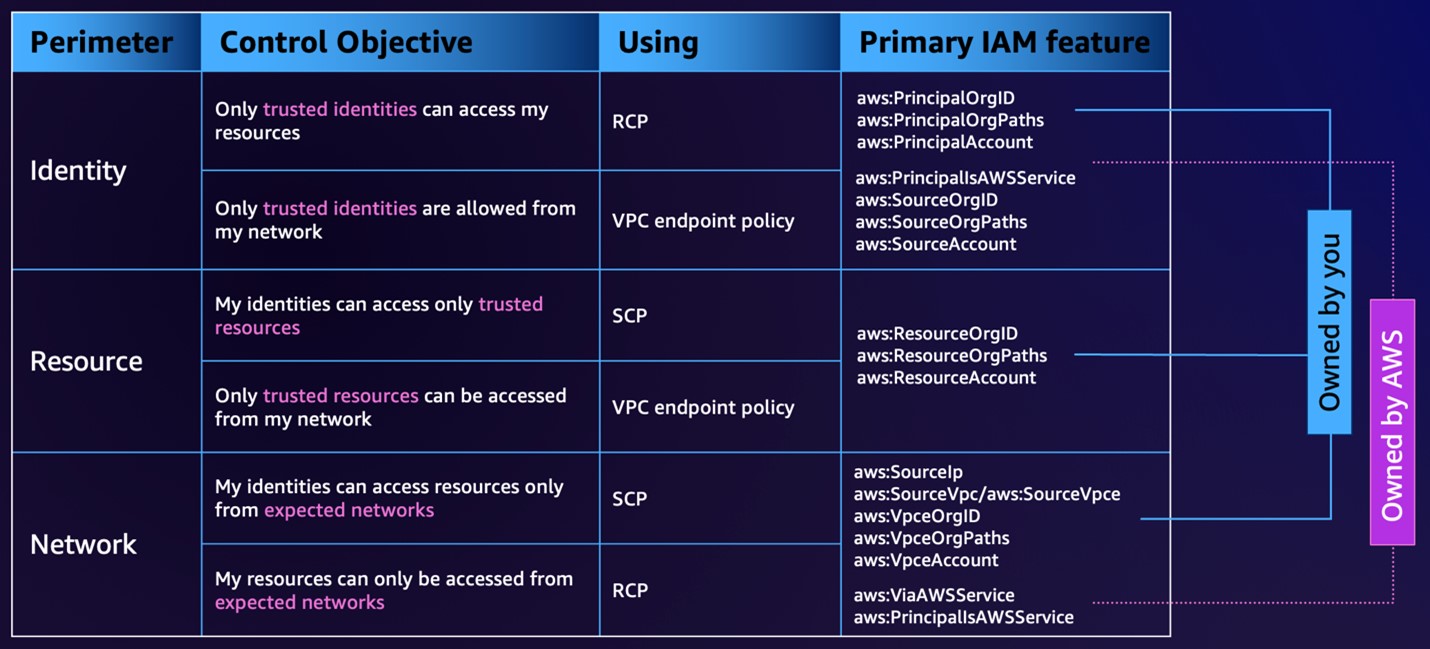
Data perimeter control objectives and capabilities
Data perimeter coarse-grained controls help you achieve six distinct security objectives through the implementation of different combinations of IAM policy types and condition keys.
Benefits
Meet security and compliance requirements
Improve your data loss prevention strategies
Establish an organization-wide data perimeter
Use cases
Allow data access to only those you want to have access
Help protect sensitive information
Help protect sensitive information with organization-wide data perimeters. Also help prevent employees from using non-corporate credentials to access non-corporate resources, which could lead to intentional or unintentional data loss. Help ensure that your employees can access only company-approved data stores.
Help prevent credential use outside of your corporate environment
Resources
Technical documentation
Tech talk
Building a data perimeter on AWS
Whitepaper
Building a data perimeter on AWS
GitHub repo
Data perimeter policy examples
Blogs
Blog Post Series: Establishing a Data Perimeter on AWS
The purpose of the Data Perimeters Blog Post Series is to provide prescriptive guidance about establishing your data perimeter at scale, including key security and implementation considerations. These blog posts cover in depth the objectives and foundational elements needed to enforce identity, resource, and network data perimeters and how to use a risk-based approach to apply the relevant controls.
Customer use cases
Video
AWS re:Inforce 2025 - Establishing a data perimeter on AWS, featuring Block, Inc. (IAM305)
Video
AWS re:Inforce 2024 - Establishing a data perimeter on AWS, featuring Capital One (IAM305)
Video
AWS re:Inforce 2023 - Establishing a data perimeter on AWS, featuring USAA (IAM301)
Document
AWS re:Invent 2022 - Establishing a data perimeter on AWS, featuring Goldman Sachs (SEC326)
Video
AWS re:Inforce 2022 - Establishing a data perimeter on AWS, featuring Vanguard (IAM304)