- Products›
- Security, Identity and Compliance›
- Detection and Response on AWS
Detection and Response on AWS
Continuously detect, prioritize, and respond to security risks to help protect your workloads, at scale
What is Detection and Response on AWS?
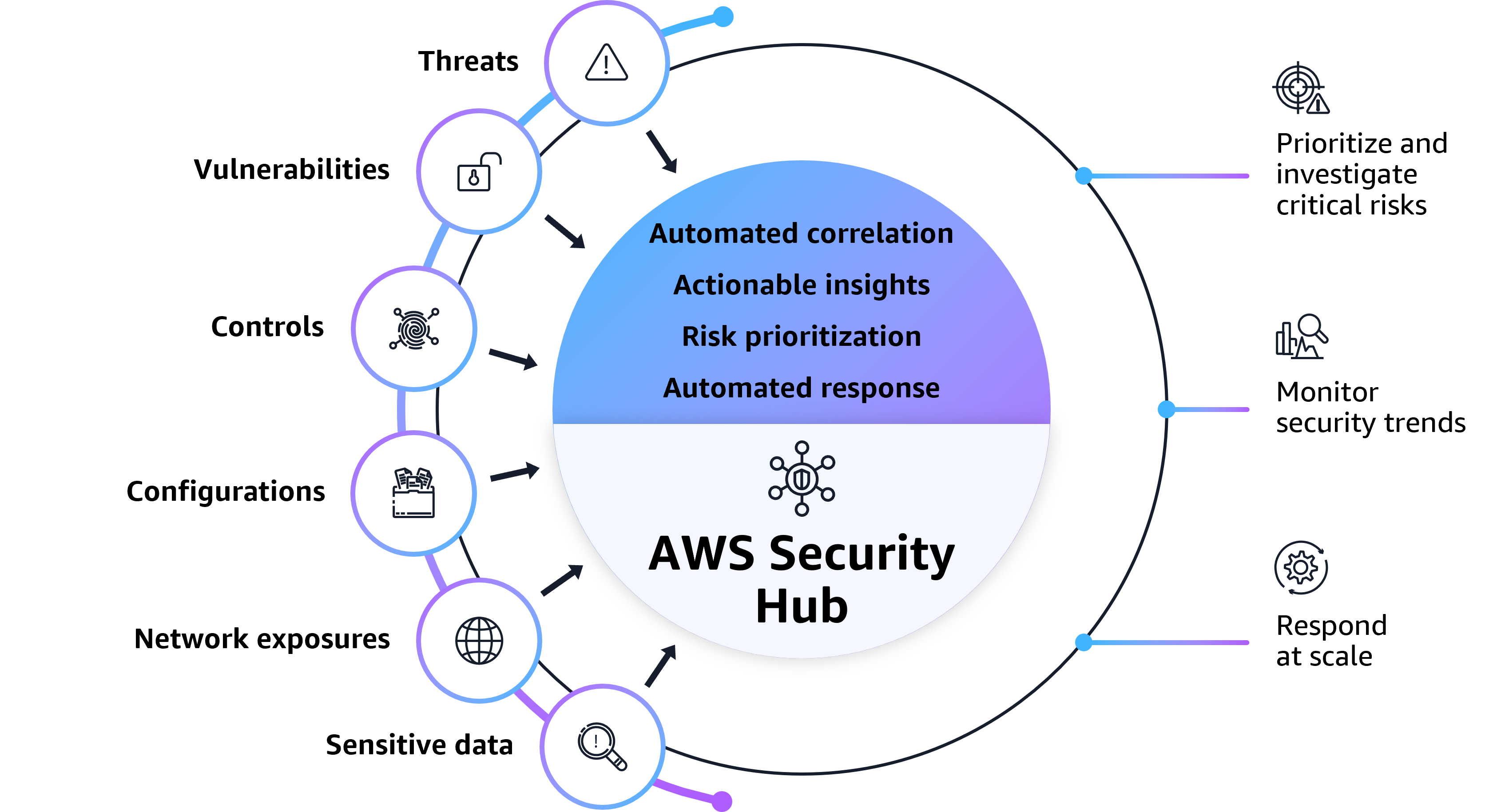
Overview
Continuously detect and prioritize critical issues through automated correlation and enriching of security signals, such as threats and vulnerabilities, to help your organization operate more securely on AWS.
Gain broader security visibility across your cloud environment through centralized management in a unified security solution, aggregating security data from AWS services and partner products across your accounts and Regions.
Get started with detection and response on AWS
Use cases
Surface active risks through unified signals across multiple security services, centralized management, and standardizing controls to reduce operational complexity.
Automatically discover and quickly route vulnerability findings in near real time to the appropriate teams, so they can take immediate action.
Continuously detect and remediate cloud resource misconfigurations and compliance risks to ensure your environment is operating according to security best practices.
Defend your accounts and workloads from potential threats, streamline threat response with automation, and minimize business impact through faster remediation and recovery time.
Discover and protect sensitive data and workloads to increase visibility and automate remediation of your data security risks.
Expedia
"Expedia needs to stay up to date with global and local compliance requirements and the ability to process, analyze, and control the vast amounts of data we generate. The AWS solution we built around Amazon Macie has helped us automate data scanning, tagging, sampling, and identification and implement rule configuration, generation of metrics, and scaling security controls. With Macie at the solution's core, we can reduce the footprint on our sensitive data. By reducing PII data, we can open up data access to our analysts while reducing exposure and, at the same time, resulting in an empowering and enriching experience for our customers."
Aaron Miller, Principal Engineer, Expedia Group
Learn how Expedia uses Macie for data protection at petabyte scale »

Featured videos
Featured content
Top 5 use cases of AWS detection and response services
Explore this infographic for an overview of AWS detection and response services.
Continuously identify and prioritize security risks
Read this ebook to learn how leading global organizations are benefiting from AWS detection and response services.