AWS News Blog
Fine-Grained Access Control for Amazon DynamoDB
I truly enjoy the process of putting blog posts together for new AWS services and features. Many features started out as specific requests from one of the hundreds of thousands of AWS users. With “customer obsession” as one of our core values, all of us on the AWS team do everything that we can to listen to our customers and to make sure that their feedback ends up in the Inbox of the right service team.
Amazon DynamoDB has become very popular with developers in a very short time. Many developers are using building mobile apps and online games using DynamoDB. Apps of this type can benefit from DynamoDB’s scalability, flexibility, and efficiency. These apps generally use a single table to store information for the entire user base, which can easily grow to the millions or tens of millions of users. This scenario requires the use of a proxy tier between the app and DynamoDB in order to handle authentication and authorization.
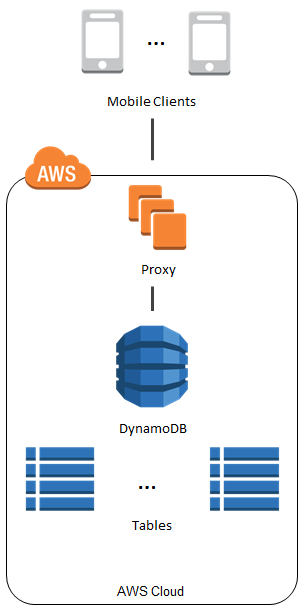
The proxy introduces additional latency and complexity, not to mention the added expense. We saw this proxy-based architecture frequently. In most cases the proxy did nothing more than regulate access to particular items and (occasionally) attributes.
Fine-Grained Access Control for DynamoDB
To make it easier for you to implement the use case that I described above, we are launching Fine-Grained Access Control for DynamoDB today. You can now use AWS Identity and Access Management (IAM) policies to regulate access to items and attributes stored in DynamoDB tables, without the need for a middle-tier proxy as illustrated above.
Here are some of the things that you can build using fine-grained access control:
- A mobile app that displays information for nearby airports, based on the user’s location. The app can access and display attributes such airline names, arrival times, and flight numbers. However, it cannot access or display pilot names or passenger counts.
- A mobile game which stores high scores for all users in a single table. Each user can update their own scores, but has no access to the other ones.
The IAM Condition element is used to implement fine-grained access control. You can use this element to allow or deny access to items and attributes based on the needs of your application. Here are your options:
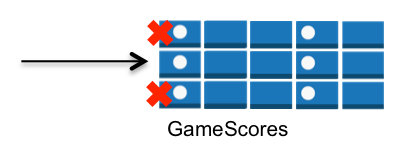
Horizontal – You can selectively hide or expose specific DynamoDB items in a particular table by matching on hash key values:
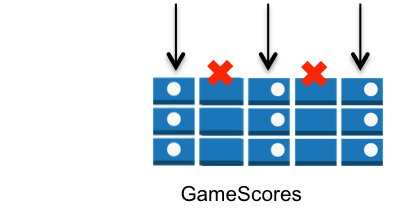
Vertical – You can selectively hide or expose specific attributes of all of the DynamoDB items in a particular table by matching on attribute names:
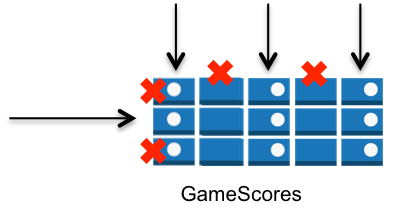
Combined – You can exercise horizontal and vertical control in the same policy:
You can combine these options with the IAM Action element to exercise even more control. For example, you can create read-only variants of the options described above by allowing only GetItem and Query in your policy.
Using Fine-Grained Access Control
Visit the Fine-Grained Access Control section of the DynamoDB Developer Guide to learn how to create an access policy, create an IAM role, and assign your access policy to the role. We also have a collection of sample policies.
The trust policy of the role determines which identity providers are accepted (e.g. Login with Amazon, Facebook, or Google) and the access policy determines which AWS resources (e.g. the DynamoDB tables, items, and attributes) can be accessed.
Here is a very simple policy. Each authenticated user has read-only access to their own items in the GameScores table:
{ "Version": "2012-10-17", "Statement": [{ "Effect": "Allow", "Action": [ "dynamodb:GetItem", "dynamodb:BatchGetItem", "dynamodb:Query" ], "Resource": ["arn:aws:dynamodb:us-west-2:123456789012:dynamodb:table/GameScores"], "Condition": { "ForAllValues:StringEquals": { "dynamodb:LeadingKeys": ["${www.amazon.com:user_id}"] } } }] }
Your code will use the role to obtain temporary security credentials for DynamoDB by calling the AssumeRoleWithWebIdentity function of the AWS Security Token Service.
You can use the new DynamoDB Policy Generator to create your first policy. Go to the DynamoDB Console, select the table, and click the Access Control button:
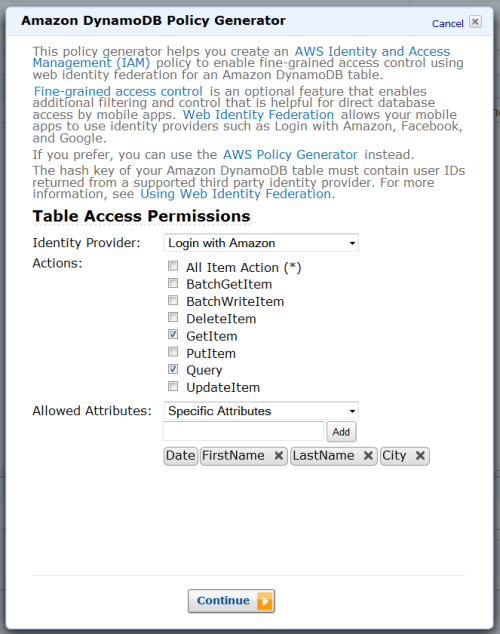
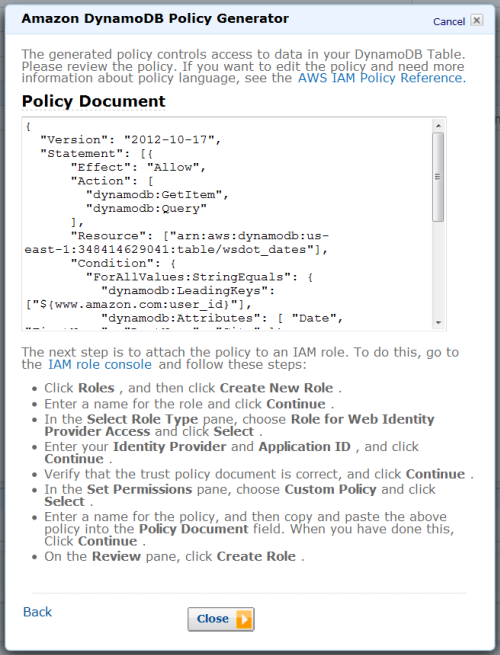
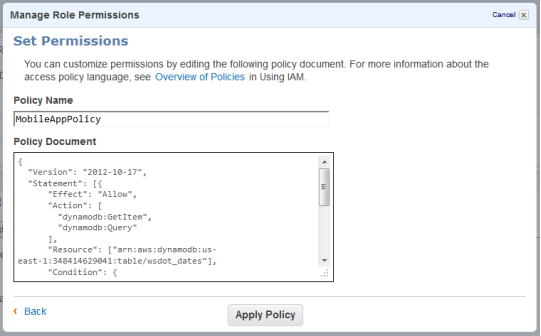
After you create it, head over to the IAM Console, create a role for Web Identity Provider access with no permissions, and then paste the policy into the role.
Watch and Learn
We have created a video tutorial to help you to get started with Fine-Grained Access Control for DynamoDB:
I hope that you find this powerful new access control feature to be of value. Leave me a comment and let me know what you think!
— Jeff;