AWS News Blog
Useful New IAM Feature – Access Key Last Use Info
Best practices for IT security are often easier to define than to implement. We are doing our best to define best practices at the AWS Security Center, backed up with services and security features that are as easy to implement as possible.
In this vein, I want to make sure that you are fully aware of a useful new AWS Identity and Access Management (IAM) feature. We launched it last month with a detailed post on the AWS Security Blog. I am following up with this post just in case you missed the first one!
As you probably know, you need to use an access key when you make a call to the AWS API. You also need to use the key when you drive AWS through the AWS Command Line Interface (AWS CLI) or the AWS Tools for Windows PowerShell. You can have two access keys for each AWS account and for each IAM user within the account. Each key can be active or inactive (if you call an AWS API using inactive key, the call will fail).
In order to maintain proper security hygiene, we strongly recommend that you rotate your keys on a regular basis. This is a simple matter of exposure: older keys are more likely to have been mishandled. Although we advise against the use of account keys, the recommendation to rotate them still applies!
While the specifics will vary based on your application, you will generally follow these general steps to rotate a set of account or user keys:
- Delete the inactive key, if any.
- Create a new key.
- Update all code and configuration files to use the new key.
- Make sure that no applications or scripts are still using the previous key.
- Deactivate the previous key.
The feature described in the post on the Security Blog was designed to help you with step 4, by telling you when a particular access key was last used. This will allow you to deactivate the previous key (step 5) with the confidence that it is no longer in use. It also allows you to identify the IAM users who have access but are no longer using it.
You can access this feature through the IAM API (GetAccessKeyLastUsed) or from the IAM Console:
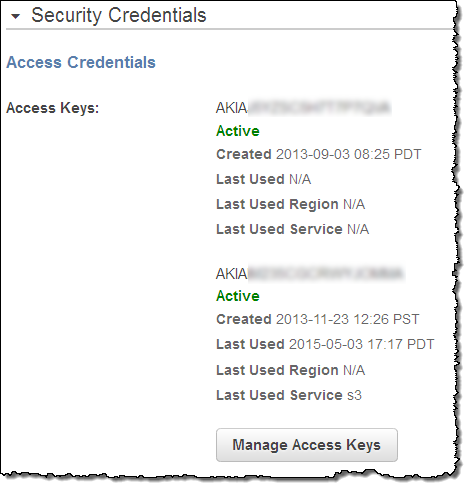 As you can see, it is time for me to follow my own advice and to rotate my keys! It also looks like I have never bothered to use one of my keys. The information provided by the API and the Console also includes the last service and the last region; this will help you to locate any legacy code that is still using outdated keys.
As you can see, it is time for me to follow my own advice and to rotate my keys! It also looks like I have never bothered to use one of my keys. The information provided by the API and the Console also includes the last service and the last region; this will help you to locate any legacy code that is still using outdated keys.
To learn more about this feature, read New in IAM: Quickly Identify When an Access Key Was Last Used in the AWS Security Blog.
— Jeff;