AWS News Blog
New – AWS Certificate Manager – Deploy SSL/TLS-Based Apps on AWS
I am fascinated by things that are simple on the surface and complex underneath! For example, consider the popular padlock icon that is used to signify that traffic to and from a web site is encrypted:

How does the browser know that it should display the green padlock? Well, that’s quite the story! It all starts with a digital file known as an SSL/TLS certificate. This is an electronic document that is used to establish identity and trust between two parties. In this case, the two parties are the web site and the web browser.
SSL/TLS is a must-have whenever sensitive data is moved back and forth. For example, sites that need to meet compliance requirements such as PCI-DSS, FedRAMP, and HIPAA make extensive use of SSL/TLS.
Certificates are issued to specific domains by Certificate Authorities, also known as CAs. When you want to obtain a certificate for your site, the CA will confirm that you are responsible for the domain. Then it will issue a certificate that is valid for a specific amount of time, and only for the given domain (subdomains are allowed). Traditionally, you were also responsible for installing the certificate on your system, tracking expiration dates, and getting fresh certificates from time to time (typically, certificates are valid for a period of 12 months).
Each certificate is digitally signed; this allows the browser to verify that it was issued by a legitimate CA. To be a bit more specific, browsers start out with a small, predefined list of root certificates and use them to verify that the other certificates can be traced back to the root. You can access this information from your browser:
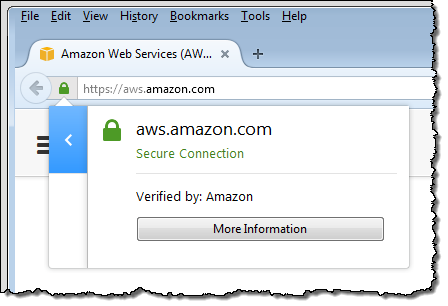
As you can probably see from what I have outlined above (even though I have hand-waved past a lot of interesting details), provisioning and managing SSL/TLS certificates can entail a lot of work, far too much of it manual and not easily automated. In many cases you also need to pay an annual fee for each certificate.
Time to change that!
New AWS Certificate Manager
The new AWS Certificate Manager (ACM) is designed to simplify and automate many of the tasks traditionally associated with management of SSL/TLS certificates. ACM takes care of the complexity surrounding the provisioning, deployment, and renewal of digital certificates! Certificates provided by ACM are verified by Amazon’s certificate authority (CA), Amazon Trust Services (ATS).
Even better, you can do all of this at no extra cost. SSL/TLS certificates provisioned through AWS Certificate Manager are free!
ACM will allow you to start using SSL in a matter of minutes. After your request a certificate, you can deploy it to your Elastic Load Balancers and your Amazon CloudFront distributions with a couple of clicks. After that, ACM can take care of the periodic renewals without any action on your part.
 Provisioning and Deploying a Certificate
Provisioning and Deploying a Certificate
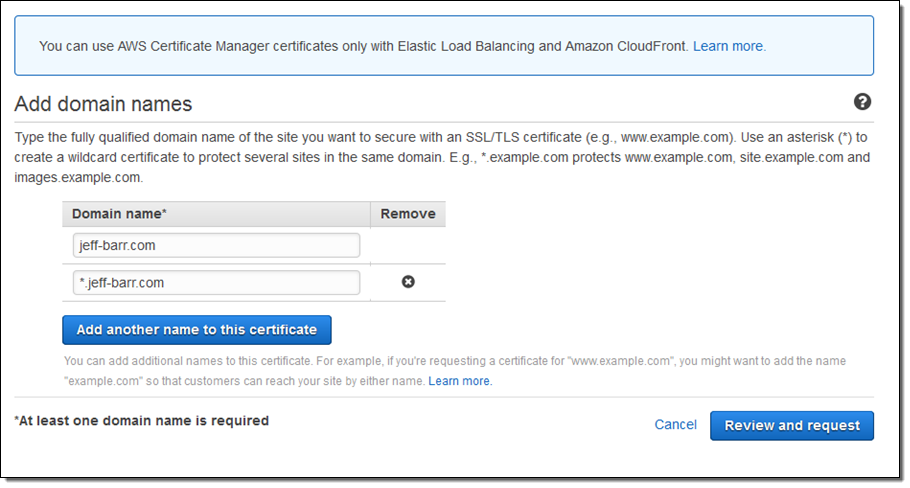
Let’s step through the process of provisioning and deploying a digital certificate using the console (APIs are also available). I’ll use one of my own domains (jeff-barr.com) for this exercise. I start by opening the AWS Certificate Manager Console and clicking on Get started.
Then I enter the domain name of the site that I want to secure. In this case I want to secure the “naked” domain and all of the first-level sub-domains within it:
Then I review my request and confirm my intent:
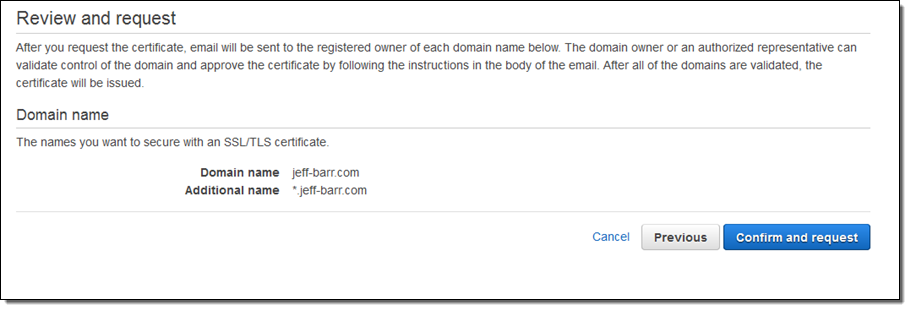
I flip over to my inbox, find the email or emails (one per domain) from Amazon (certificates.amazon.com), and click on Amazon Certificate Approvals:
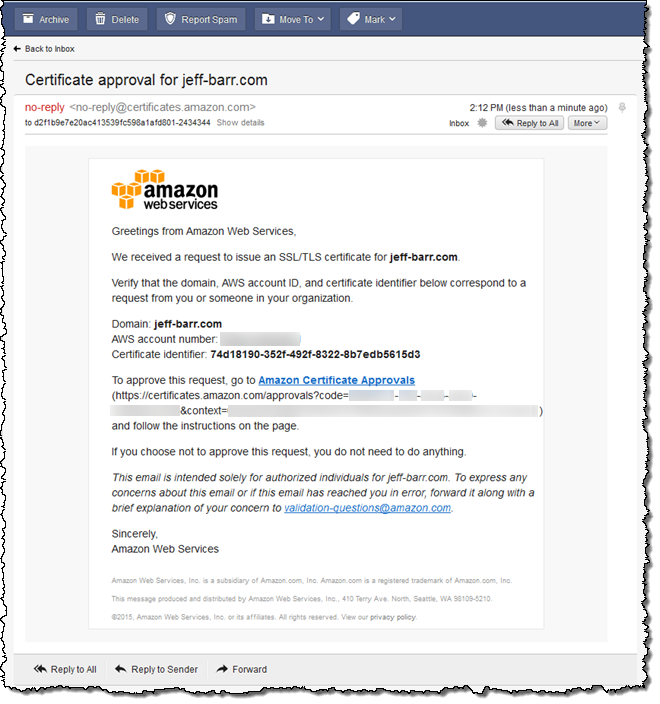
I visit the site and click on I Approve:
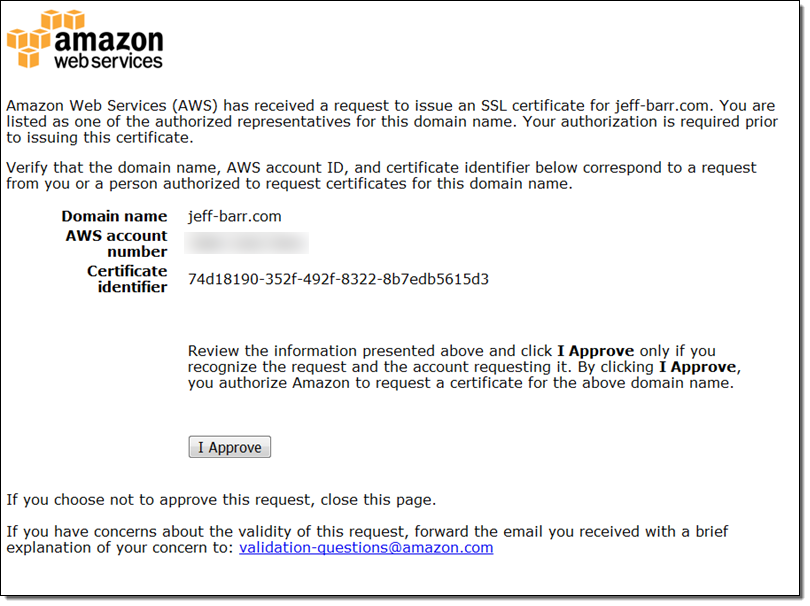
And that’s all it takes! The certificate is now visible in the console:
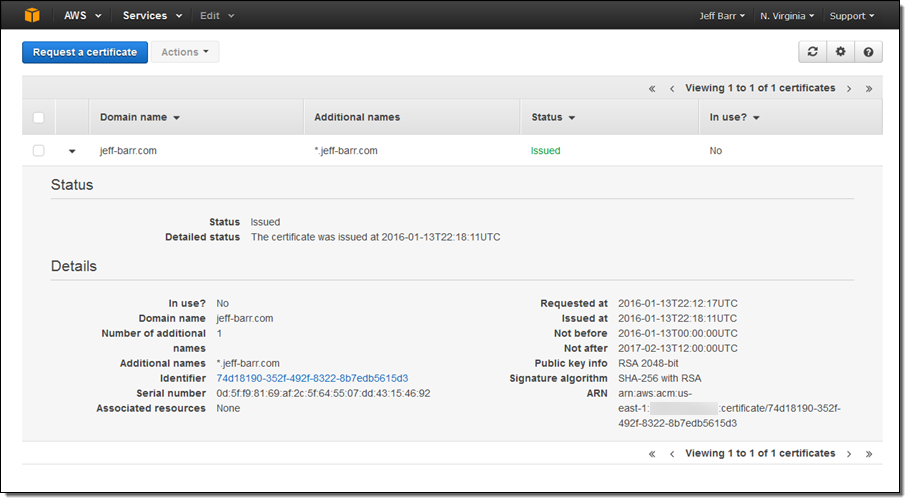
Deploying the Certificate
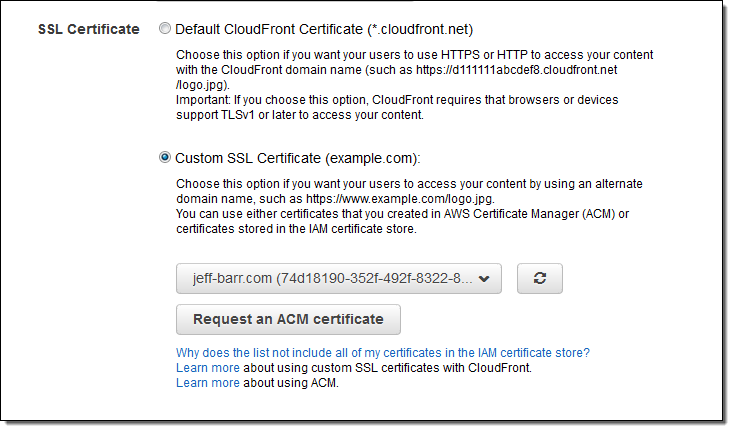
After the certificate is issued, I can deploy it to my Elastic Load Balancers and/or CloudFront distributions.
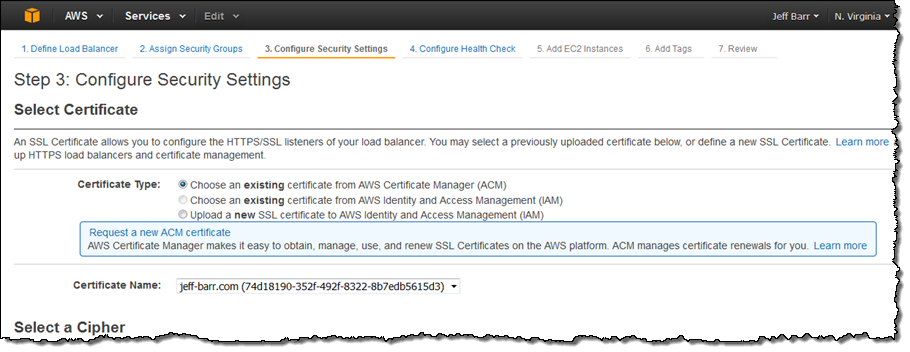
Because ELB supports SSL offload, deploying a certificate to a load balancer (rather than to the EC2 instances behind it) will reduce the amount of encryption and decryption work that the instances need to handle.
And for a CloudFront distribution:
Available Now
AWS Certificate Manager (ACM) is available now in the US East (N. Virginia) region, with additional regions in the works. You can provision, deploy, and renew certificates at no charge.
We plan to add support for other AWS services and for other types of domain validation. As always, your suggestions and feedback are more than welcome and will help us to prioritize our work.
If you are using AWS Elastic Beanstalk, take a look at Enabling SSL/TLS (for free) via AWS Certificate Manager.
— Jeff;