- Products›
- Security, Identity & Compliance›
- Amazon GuardDuty
Amazon GuardDuty
Protect your AWS accounts, workloads, and data with intelligent threat detection
Benefits of Amazon GuardDuty
Rapidly detect threats using anomaly detection, AI, ML, threat intelligence, and behavioral modeling.
Safeguard your accounts, data, and resources across various AWS compute types, spanning Amazon Elastic Compute Cloud (Amazon EC2), serverless workloads, and container workloads—including those on AWS Fargate.
What is GuardDuty?
Amazon GuardDuty uses AI and ML with integrated threat intelligence from AWS and leading third parties to help protect your AWS accounts, workloads, and data from threats.
How it works
Amazon GuardDuty is a threat detection service that continuously monitors your AWS accounts and workloads for malicious activity and delivers detailed security findings for visibility and remediation.
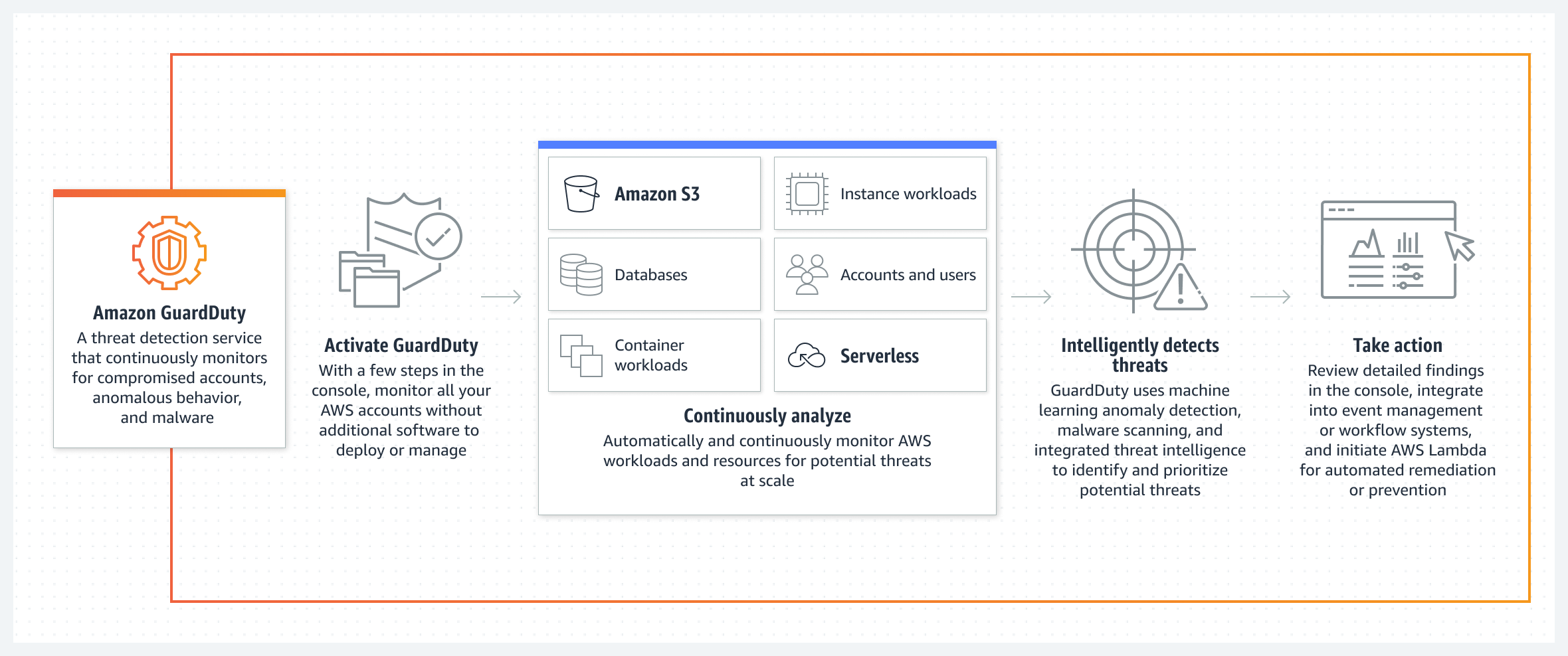
GuardDuty for AWS workload protection
Learn more about how you can apply the broad threat detection coverage in GuardDuty to workloads and resources across your AWS environment.
Compute Protection
Open allScan EBS volumes attached to Amazon EC2 instances for malware when GuardDuty detects that one of your EC2 instances or container workloads running on EC2 is doing something suspicious.
GuardDuty EKS Protection monitors Amazon Elastic Kubernetes Service (Amazon EKS) cluster control plane activity by analyzing Amazon EKS audit logs.
Gain visibility into on-host, operating system-level activity and detect runtime threats from over 30 security findings to help protect your Amazon EKS clusters, Amazon ECS workloads— including serverless workloads on AWS Fargate and Amazon EC2 instances.
Learn more about GuardDuty EKS Runtime Monitoring, ECS Runtime Monitoring, and EC2 Runtime Monitoring.
Continuously monitor network activity, starting with VPC Flow Logs, from your serverless workloads to detect threats such as AWS Lambda functions maliciously repurposed for unauthorized cryptocurrency mining or compromised Lambda functions that are communicating with known threat actor servers.
Learn more »
Storage Protection
Open allGuardDuty is capable of analyzing over a trillion Amazon Simple Storage Service (Amazon S3) events per day. Continuously monitor and profile Amazon S3 data access events and S3 configurations to detect suspicious activities such as requests coming from an unusual geolocation, disabling of preventative controls like S3 block public access, or API call patterns consistent with an attempt to discover misconfigured bucket permissions.
Learn more »
Detect potentially harmful uploads to your Amazon S3 buckets with integrated, scalable, and fully managed malware scanning.
Learn more »
Detect malware in Amazon EC2, Amazon EBS, and Amazon S3 backups without deploying additional security software. Automatically scan backups after creation, run on-demand scans, and verify backup integrity before restoration with cost-effective incremental scanning.
Database Protection
Open allUsing tailored ML models and integrated threat intelligence, GuardDuty can detect potential threats in Amazon Relational Database Service (Amazon RDS), starting with Amazon Aurora, such as high-severity brute force attacks, suspicious logins, and access by known threat actors.
Learn more »
Use cases
Identify multi-stage attack sequences like abnormal removal of artificial intelligence (AI) security guardrails, model usage, or exfiltrated Amazon EC2 credentials being used to call APIs in Amazon Bedrock, Amazon SageMaker, or self-managed AI workloads.
Triage threats more quickly with automated threat signal correlation and prescriptive remediation recommendations. Determine root cause with Amazon Detective. Route findings to AWS Security Hub and Amazon EventBridge or third-party solutions.
Initiate scans of your Amazon Elastic Block Store (Amazon EBS) volumes associated with your Amazon EC2 instances and container workloads. Automatically monitor uploads to Amazon S3 buckets and scan EC2, EBS, and S3 backups stored in AWS Backup to detect malware, including backdoors, cryptocurrency miners, and trojans.
Remove complexity for security and application teams with a single place to identify, profile, and manage threats to your AWS container environments across Amazon EKS and Amazon ECS—including both instance and serverless container workloads
Demonstrate an ability to meet intrusion detection requirements mandated by certain compliance frameworks.
Did you find what you were looking for today?
Let us know so we can improve the quality of the content on our pages