Manage IAM Roles
AWS Identity and Access Management (IAM) roles are entities you create and assign specific permissions to that allow trusted identities such as workforce identities and applications to perform actions in AWS. When your trusted identities assume IAM roles, they are granted only the permissions scoped by those IAM roles. Using IAM roles is a security best practice because roles provide temporary credentials that do not need to be rotated.
Common scenarios in which IAM roles are used
Federate workforce identities into AWS: By using IAM Identity Center, your users can use their existing corporate credentials to federate into AWS accounts. With IAM roles, you can specify the permissions users should have when accessing AWS accounts.
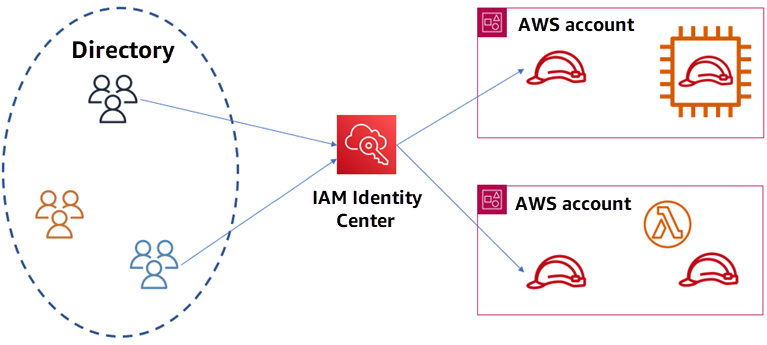
Access workloads within AWS: A workload is a collection of resources and code, such as an application, that requires an identity to make requests to AWS services. By using IAM roles, your application running in any AWS compute environment, such as Amazon EC2 instances, can access AWS resources with temporary credentials, removing the need to manage long-term credentials.
Access workloads that run outside of AWS: You might have workloads running outside of AWS, such as on-premises, hybrid, and multicloud environments, that need access to your AWS resources. By using IAM Roles Anywhere, your applications outside of AWS can obtain temporary access to resources in your AWS environment.
Enable cross-account access: We recommend that you use multiple AWS accounts to isolate and manage your business applications and data. To allow your identities in one AWS account to access resources in another AWS account, you can use IAM roles to provide access.
Grant access to AWS services: AWS services need to be given permission to perform actions in your AWS account on your behalf. When you set up an AWS service environment, you define a role for the service to assume. The service can then assume the service role and perform only the actions you have specified.
For more information about roles, see IAM roles in the IAM User Guide.
Learn how to manage permissions with IAM

