Posted On: Oct 26, 2016
Starting today, customers using AWS Directory Service for Microsoft Active Directory (Enterprise Edition), also called Microsoft AD, now have the added permissions to install and use Microsoft Network Policy Server (NPS). The new permissions grant you the rights required to register NPS in the RAS and IAS Servers security group. Once NPS is installed and registered, you can use it to enforce network access policies for client health, network connection authentication, and network access authorization by using account information stored in Microsoft AD.
In order to use NPS with Microsoft AD, you will need NPS running on an Amazon EC2 for Windows Server instance or on a Windows server in your on-premises network. You must join that server to your Microsoft AD domain. See Install Network Policy Server (NPS) for how to add the NPS role to a Windows server. Also see Joining a Windows Instance to an AWS Directory Service Domain.
The following diagram illustrates the process of setting up NPS with Microsoft AD.
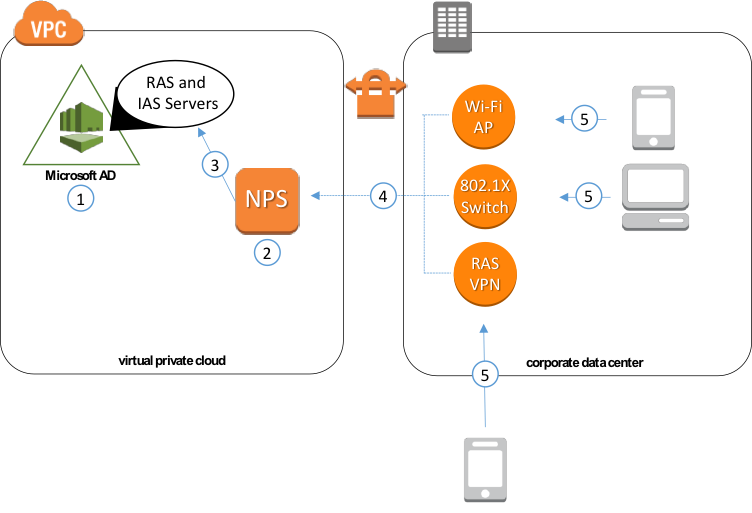
1. Create Microsoft AD
2. Domain join EC2 Windows Server
3. Install NPS (add to RAS and IAS Server group)
4. Point on-premises RADIUS clients to NPS (Wi-Fi AP, 802.1x switch, RAS VPN, etc.)
5. Devices connecting on-premises authenticate to NPS using Microsoft AD credentials
You can configure NPS as a Remote Authentication Dial-In User Service (RADIUS) server, a RADIUS proxy, and a Network Access Protection (NAP) policy server. NPS enables you to configure policies that control Remote Virtual Private Network (VPN) access, Wi-Fi access, and other access types that utilize the RADIUS protocol. For example, using NPS you can establish time of day access policies for Wi-Fi, or enable the use of two-factor authentication tokens for VPN access through NPS plug-ins. In order for NPS to enforce policies for accounts stored in Active Directory, you must register NPS in the preconfigured RAS and IAS Servers security group. Microsoft AD now delegates management control of the RAS and IAS Servers security group to the administrator’s account for your Microsoft AD organizational unit. This enables you to install and register NPS to control access by user, group, and computer stored in your Microsoft AD domain.
This new capability is available to all existing and future Microsoft AD customers. To learn more about Microsoft AD, see the Directory Service website.