Taking the first step
Introduction
Security, identity, and compliance in the cloud are pivotal components in achieving and maintaining the integrity and safety for your data and services. This is especially relevant as more businesses migrate to cloud providers like Amazon Web Services (AWS).
Cloud security refers to using measures and practices to protect digital assets from threats. This encompasses both the physical security of data centers and the cybersecurity measures to guard against online threats. AWS prioritizes security through encrypted data storage, network security, and continuous monitoring of potential threats.
Identity services help you securely manage identities, resources, and permissions at scale. AWS provides identity services designed for workforce and customer-facing applications, and for managing access to your workloads and applications.
Compliance in the cloud refers to adhering to laws and regulations governing data protection and privacy. AWS Compliance Programs provide information about the certifications, regulations, and frameworks that AWS aligns with. AWS Compliance explains the robust controls in place at AWS to maintain security and data protection in the AWS Cloud.
This guide helps you select the AWS security, identity, and compliance services and tools that are the best fit for your needs and your organization.
Purpose
Help determine which AWS security, compliance, and identity services are the best fit for your organization.
Last updated
March 20, 2024
Covered services
AWS Artifact
AWS Audit Manager
AWS Certificate Manager
AWS CloudHSM
Amazon Cognito
Amazon Detective
AWS Firewall Manager
Amazon GuardDuty
AWS Identity and Access Management (IAM)
AWS IAM Identity Center
Amazon Inspector
AWS Key Management Service (AWS KMS)
Amazon Macie
AWS Network Firewall
AWS Private Certificate Authority (AWS Private CA)
AWS Resource Access Manager (AWS RAM)
AWS Secrets Manager
AWS Security Hub
Amazon Security Lake
AWS Shield
AWS WAF
Understand
Security and compliance are shared responsibilities
Before choosing your AWS security, identity, and compliance services, it’s important to understand that security and compliance are shared responsibilities between you and AWS.
The nature of this shared responsibility helps relieve your operational burden, and it provides you with flexibility and control over your deployment. This differentiation of responsibility is commonly referred to as security “of” the cloud versus security “in” the cloud.
-
AWS responsibility: Security "of" the cloud
AWS is responsible for protecting the infrastructure that runs all of the services offered in the AWS Cloud. This infrastructure is composed of the hardware, software, networking, and facilities that run AWS Cloud services.
-
Your responsibility: Security "in" the cloud
Your responsibility is determined by the AWS Cloud services you select. This determines the amount of configuration work that you need to do as part of your security responsibilities. For example, a service such as Amazon Elastic Compute Cloud (Amazon EC2) is categorized as Infrastructure as a Service (IaaS). As such, you must perform all of the necessary security configuration and management tasks. If you then deploy an Amazon EC2 instance, you are responsible for management of the guest operating system (including updates and security patches), any application software or utilities you install on the instances, and the configuration of the AWS provided firewall (called a security group) on each instance. For abstracted services, such as Amazon Simple Storage Service (Amazon S3) and Amazon DynamoDB, AWS operates the infrastructure layer, the operating system, and platforms, and you access the endpoints to store and retrieve data. You are responsible for managing your data (including encryption options), classifying your assets, and using IAM tools to apply the appropriate permissions.
Carefully consider the services that you choose, as your responsibilities vary depending on:- The services used
- The integration of those services into your existing environment
- Applicable laws and regulations
With an understanding of this model, you can next understand the range of options available to you, and how the applicable AWS services fit together.
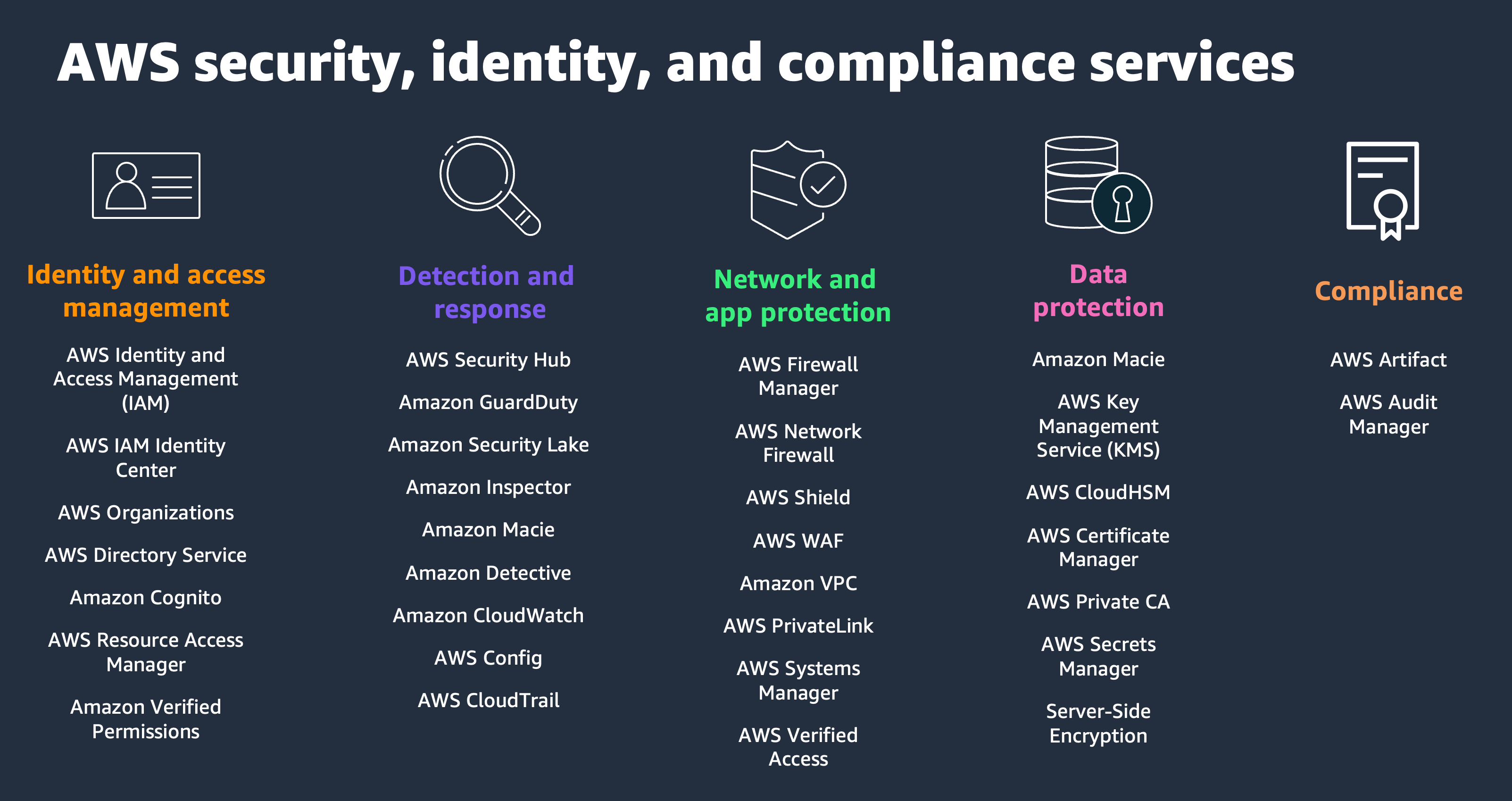
AWS offers 30+ tools and services for security, identity, and compliance
AWS offers more than 30 tools and services across five domains to help you achieve and maintain robust security, identity management, and compliance in the cloud. Those domains are:
-
Identity and access management
At the heart of AWS security is the principle of least privilege, so that individuals and services have only the access they need. You can use AWS IAM Identity Center to manage access to your accounts and permissions within those accounts—including identities from external identity providers. With AWS Organizations, you can set up policy-based management for multiple accounts within your organization.
-
Detection and response
AWS provides tools to help you streamline security operations across your AWS environment. For example, Amazon GuardDuty offers intelligent threat detection, while Amazon Detective makes it easy to identify and analyze security findings by collecting log data. AWS Security Hub supports multiple security standards and provides an overview of security alerts and compliance status across AWS accounts. AWS CloudTrail tracks user activity and application programming interface (API) usage, which is crucial for understanding and responding to incidents.
-
Network and application protection
AWS offers several services to protect your networks and applications. Amazon Virtual Private Cloud (Amazon VPC) helps you launch AWS resources in a virtual network, offering control over the network environment. AWS Shield provides protection against Distributed Denial of Service (DDoS) attacks, and AWS WAF helps protect web applications from common web exploits.
-
Data protection
Data protection is vital in the cloud, and AWS provides services that help you protect your data, accounts, and workloads. AWS Key Management Service (AWS KMS) and AWS CloudHSM allow you to create and control the cryptographic keys you use to protect your data.
-
Compliance
AWS supports a range of compliance certifications and controls, helping customers meet their regulatory requirements. For example, AWS Artifact provides on-demand access to compliance reports, and AWS Config helps track compliance of AWS resources with auditing and governance needs.
In summary, the AWS services across these five domains can help you form a multi-layered approach to keeping your data and environments safe. You can use these services to help you fortify your cloud infrastructure against evolving threats—while helping you adhere to stringent regulatory standards.
To learn more about AWS security, including security documentation for our services, see AWS Security Documentation.
Consider
Choosing the right security, identity, and compliance services on AWS depends on your specific requirements and use cases. Here are some criteria to consider when making your decision.
-
Conduct a comprehensive assessment of your organization's specific vulnerabilities and threats. This involves identifying the types of data you handle, such as personal customer information, financial records, or proprietary business data. Understand the potential risks associated with each.
Assess your application and infrastructure architecture. Determine whether your applications are public-facing and what kind of web traffic they handle. This influences the need for services like AWS WAF to protect against web exploits. For internal applications, consider the importance of internal threat detection and continuous monitoring with Amazon GuardDuty, which can identify unusual access patterns or unauthorized deployments.
Finally, consider the sophistication of your existing security posture and the expertise of your security team. If your team has limited resources, opting for services that offer more automation and integration can provide effective security enhancements without overwhelming your team. Example services include AWS Shield for DDoS protection and AWS Security Hub for centralized security monitoring.
-
Compliance is about protecting your customer data and maintaining trust. Identify the relevant laws and standards for your industry or geographic region, such as General Data Protection Regulation (GDPR), the U.S. Health Insurance Portability and Accountability Act of 1996 (HIPAA), or Payment Card Industry Data Security Standard (PCI DSS).
AWS offers services such as AWS Config and AWS Artifact to help manage compliance with various standards. AWS Config allows you to assess, audit, and evaluate the configurations of your AWS resources, making it easier to ensure compliance with internal policies and regulatory requirements. AWS Artifact provides on-demand access to AWS compliance documentation, aiding in audits and compliance reporting.
Choosing services that align with specific compliance needs can help your organization meet legal requirements and build a secure and trustworthy environment for your data. Explore AWS Compliance Programs to learn more.
-
When considering cost and budget implications of AWS security services, it’s essential to start with a clear understanding of the pricing models for each service that you’re considering. AWS often charges based on usage, such as the number of API calls, the volume of data processed, or the amount of data stored. For example, Amazon GuardDuty charges based on the amount of log data analyzed for threat detection, while AWS WAF bills are based on the number of rules deployed and the number of web requests received.
Estimate your expected usage to forecast costs accurately. Consider both current needs and potential growth or spikes in demand. Scalability is a key feature of AWS services but can also lead to increased costs if not managed carefully. Use the AWS Pricing Calculator to model different scenarios and assess their financial impact.
Evaluate the total cost of ownership (TCO), which includes both direct costs and indirect costs such as the time and resources needed for management and maintenance. Opting for managed services can reduce operational overhead but might come at a higher price point.
Lastly, prioritize your security investments based on risk assessment. Not all security services will be equally critical to your infrastructure, so focus your budget on the areas that will have the most significant impact on reducing risk and ensuring compliance. Balancing cost-effectiveness with the level of security needed is key to a successful AWS security strategy.
-
Evaluate how you will manage and authenticate user identities, assign roles, and enforce access controls across your AWS environment. Adopt the principle of least privilege—ensuring that users have only the access necessary to perform their roles.
Think about your organization’s structure and how access needs might vary by team, project, or location. IAM helps you create granular policies that reflect these needs. Also, consider the integration of multi-factor authentication (MFA) to add an extra layer of security for accessing sensitive resources.
Another aspect is the management of credentials and access keys. Consider using IAM Identity Center for centralizing access management across multiple AWS accounts and business applications, enhancing both security and user convenience.
Lastly, evaluate how these identity and access management services integrate with your existing directory services. If you have an existing identity provider, you can integrate it with IAM using SAML 2.0 or OpenID Connect (OIDC). IAM Identity Center has support for System for Cross-domain Identity Management (SCIM) provisioning to help keep your directories synchronized. This helps you ensure a seamless and secure user experience while accessing AWS resources.
-
In the context of AWS security-related services, scalability and flexibility are critical considerations to ensure that security measures grow seamlessly with your infrastructure and adapt to evolving threats.
AWS security services, such as Amazon GuardDuty for threat detection and AWS WAF for protecting web applications, are designed to automatically scale with your application's traffic and usage patterns. This ensures that as your business scales up, your security measures do too, without requiring manual adjustments or causing bottlenecks.
Flexibility is equally important, as it allows for the customization of security controls to match specific business requirements and threat landscapes. For instance, you can use some security, identity, and compliance services with AWS Organizations, which allows you to manage those services’ resources across multiple accounts. This gives individual application teams the flexibility and visibility to manage security needs that are specific to their workload, while also allowing governance and visibility to centralized security teams.
Considering scalability and flexibility helps you ensure that your security posture is robust, responsive, and capable of supporting dynamic business environments.
-
Ensure that new security measures enhance, rather than disrupt, your current operations. Effective integration facilitates streamlined workflows, allowing security data and alerts from AWS services to be aggregated and analyzed alongside existing security information and event management (SIEM) systems.
Aim to improve your overall security posture by allowing for a unified view of security threats and vulnerabilities across both AWS and on-premises environments.
For instance, integrating AWS CloudTrail with existing log management solutions allows for comprehensive monitoring of user activities and API usage across your AWS infrastructure and existing applications. Integration optimizes resource utilization and ensures that security policies are applied consistently across environments. This helps reduce the risk of gaps in security coverage. Ultimately, well-integrated security solutions support more efficient and effective security operations. This is critical for maintaining the integrity and resilience of business operations in the cloud.
Choose
Now that you know the criteria for evaluating your security options, you're ready to choose which AWS security services might be a good fit for your organizational requirements.
The following table highlights which services are optimized for which circumstances. Use the table to help determine the service that is the best fit for your organization and use case.
Grant appropriate individuals the right level of access to systems, applications, and data.
Create or connect users and centrally manage access across AWS accounts and applications.
Amazon Cognito
Provides an identity tool for web and mobile apps to authenticate and authorize users from the built-in user directory, from your enterprise directory, and consumer identity providers.
Continuously identify and prioritize security risks, while integrating security best practices early.
Get a detailed view of the configuration of AWS resources in your AWS account.
Provides a comprehensive view of your security state in AWS.
Analyzes and processes CloudTrail management events, CloudTrail event logs, VPC flow logs, and DNS logs.
Scans your AWS workloads for software vulnerabilities and unintended network exposure.
Amazon Security Lake
Automatically centralizes security data from AWS environments, SaaS providers, on-premises environments, cloud sources, and third-party sources into a data lake.
Helps you analyze, investigate, and quickly identify the root cause of security findings or suspicious activities.
Protect your internet-facing resources centrally against common DDoS and application attacks.
Simplifies your administration and maintenance tasks across multiple accounts and resources for protections.
Provides a stateful, managed, network firewall and intrusion detection and prevention service with your VPC.
Provides protections against DDoS attacks for AWS resources at the network, transport, and application layers.
Automate and simplify data protection and security tasks—ranging from key management and sensitive data discovery to credential management.
Discovers sensitive data by using machine learning and pattern matching, and enables automated protection against associated risks.
Provides highly available, cloud-based hardware security modules (HSMs).
Handles the complexity of creating, storing, and renewing public and private SSL/TLS X.509 certificates and keys.
AWS Private CA
Helps you create private certificate authority hierarchies, including root and subordinate certificate authorities (CA)s.
Manage, retrieve, and rotate database credentials, application credentials, OAuth tokens, API keys, and other secrets.
Automate your compliance and auditing processes.
AWS Artifact
Provides on-demand downloads of AWS security and compliance documents.
AWS Audit Manager
Helps you continuously audit your AWS usage to simplify how you assess risk and compliance.
Use
You should now have a clear understanding of what each AWS security service (and the supporting AWS tools and services) does - and which might be right for you.
To explore how to use and learn more about each of the available AWS security services, we have provided a pathway to explore how each of the services work. The following sections provide links to in-depth documentation, hands-on tutorials, and resources to get you started.
Here are some useful identity and access management resources, organized by service, to help you get started.
-
AWS Identity and Access Management (IAM)
-
AWS IAM Identity Center
-
Amazon Cognito
-
AWS Resource Access Manager (AWS RAM)
-
AWS Identity and Access Management (IAM)
-

Create a customer managed policy
Use the AWS Management Console to create a customer managed policy and then attach that policy to an IAM user in your AWS account.
-
AWS IAM Identity Center
-
-
Amazon Cognito
-
-
AWS Resource Access Manager (AWS RAM)
-
The following section offers links to detailed resources covering AWS detection and response services.
-
AWS Config
-
AWS Security Hub
-
Amazon GuardDuty
-
Amazon Inspector
-
Amazon Security Lake
-
Amazon Detective
-
AWS Config
-

Getting started with AWS Config
Follow this guide to get started with AWS Config.

Risk and Compliance workshop
Learn how to automate controls using AWS Config and AWS Managed Config Rules.

AWS Config Rule Development Kit library: Build and operate rules at scale
Learn how to use the Rule Development Kit (RDK) to build a custom AWS Config rule and deploy it with the RDKLib.
-
AWS Security Hub
-

Getting started with AWS Security Hub
Get a comprehensive view of your security state in AWS and get help assessing your AWS environment in alignment with security industry standards and best practices.
-
Amazon GuardDuty
-
-
Amazon Inspector
-
-
Amazon Security Lake
-
-
Amazon Detective
-
The following section offers links to detailed resources covering AWS network and application protection.
-
AWS Firewall Manager
-
AWS Network Firewall
-
AWS Shield
-
AWS WAF
-
AWS Firewall Manager
-
-
AWS Network Firewall
-
-
AWS Shield
-
-
AWS WAF
-
The following section offers links to detailed resources covering AWS data protection.
-
Amazon Macie
-
AWS KMS
-
AWS CloudHSM
-
AWS Certificate Manager
-
AWS Private CA
-
AWS Secrets Manager
-
Amazon Macie
-

Discovering sensitive data with Amazon Macie
Automate discovery, logging, and reporting of sensitive data in your Amazon S3 data estate.
-
AWS KMS
-
AWS CloudHSM
-

-
AWS Certificate Manager
-

Getting started with AWS Certificate Manager
Learn how to use this service to handle the complexity of creating, storing, and renewing public and private SSL/TLS X.509 certificates and keys that protect your AWS websites and applications.
Explore the guide » -
AWS Private CA
-

Getting started with AWS Private CA
Learn how this service can be used to enable creation of private certificate authority (CA) hierarchies, including root and subordinate CAs, without the investment and maintenance costs of operating an on-premises CA.
-
AWS Secrets Manager
-
The following section offers links to detailed resources covering compliance.
-
AWS Artifact
-
AWS Audit Manager
-
AWS Artifact
-
-
AWS Audit Manager
-
Explore
Explore reference architecture diagrams to help you use AWS security, identity, and compliance services.
Explore architecture diagrams »
Explore whitepapers to help you get started, learn best practices, and understand your security, identity, and compliance options on AWS.
Explore vetted solutions and architectural guidance for common AWS security, identity, and compliance use cases.