What is Cryptography?
Cryptography is the practice of protecting information through the use of coded algorithms, hashes, and signatures. The information can be at rest (such as a file on a hard drive), in transit (such as electronic communication exchanged between two or more parties), or in use (while computing on data). Cryptography has four primary goals:
- Confidentiality – Makes information available to only authorized users.
- Integrity – Ensures that information has not been manipulated.
- Authentication – Confirms the authenticity of information or the identity of a user.
- Non-repudiation – Prevents a user from denying prior commitments or actions.
Cryptography uses a number of low-level cryptographic algorithms to achieve one or more of these information security goals. These tools include encryption algorithms, digital signature algorithms, hash algorithms, and other functions. This page will describe a few of the most commonly used low-level cryptographic algorithms.
What is cryptography used for?
Cryptography has its roots in sending sensitive information between military and political figures. Messages could be encrypted so that they appear to be random text to anyone but the intended recipient.
Today, the original techniques for encryption have been thoroughly broken. They're broken to the point that they are only found in the puzzle sections of some newspapers. Fortunately, the field has made major advancements in security, and the algorithms used today rely on rigorous analysis and mathematics for their security.
As security has advanced, the field of cryptography has expanded to include a broader range of security goals. These include message authentication, data integrity, secure computation, and more.
Cryptography is at the foundation of the modern society. It's the basis of countless internet applications via the Secure Hypertext Transfer Protocol (HTTPS), secure text and voice communication, and even digital currencies.
What is encryption?
An encryption algorithm is a procedure that converts a plaintext message into an encrypted ciphertext. Modern algorithms use advanced mathematics and one or more encryption keys. These make it relatively easy to encrypt a message but virtually impossible to decrypt it without knowing the keys.
Encryption techniques fall into two categories, symmetric and asymmetric, based on how their keys function.
What is symmetric-key cryptography?
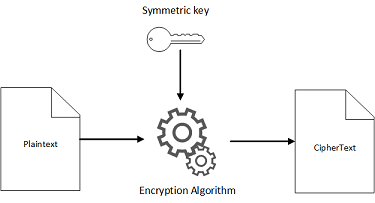
Symmetric-key cryptographic algorithms use the same cryptographic keys for both the encryption of the plaintext and the decryption of the ciphertext. Symmetric encryption requires that all intended message recipients have access to a shared key.
The following illustrations show how encryption and decryption work with symmetric keys and algorithms, assuming that all parties share the same key.
In the first illustration, a symmetric key and algorithm are used to convert a plaintext message into ciphertext. The second illustration shows the same secret key and symmetric algorithm being used to turn ciphertext back into plaintext.
One of the most popular block ciphers is the Advanced Encryption Standard (AES). This block cipher supports 128-, 192-, or 256-bit keys. AES is often combined with Galois/Counter Mode (GCM) and known as AES-GCM to make an authenticated encryption algorithm.
AES is the industry standard for encryption performed around the world. Its security is well understood, and efficient software and hardware implementations are widely available.
What is asymmetric (public-key) cryptography?
Asymmetric (or public-key) cryptography consists of a broad set of algorithms. These are based on mathematical problems that are relatively easy to perform in one direction, but which cannot be easily reversed.
One famous example of this type of problem is the factoring problem: for carefully chosen prime numbers p and q, we can compute the product N=p*q quickly. However, given only N, it is very hard to recover p and q.
A common public-key cryptographic algorithm based on the factoring problem is the Rivest-Shamir-Adleman (RSA) function. When combined with an appropriate padding scheme, RSA can be used for multiple purposes, including asymmetric encryption.
An encryption scheme is called asymmetric if it uses one key—the public key—to encrypt data, and a different but mathematically related key—the private key—to decrypt data.
It must be computationally infeasible to determine the private key if the only thing one knows is the public key. Therefore, the public key can be distributed broadly while the private key is kept secret and secure. Together the keys are referred to as a key pair.
One popular asymmetric encryption scheme is RSA-OAEP, which is a combination of the RSA function with the Optimal Asymmetric Encryption Padding (OAEP) padding scheme. RSA-OAEP is typically only used to encrypt small amounts of data because it is slow and has ciphertexts which are much larger than the plaintext.
What is hybrid encryption?
Because public-key algorithms like RSA-OAEP are less efficient than their symmetric counterparts, not commonly used to directly encrypt data. However, they do serve an important role in the cryptographic ecosystem by providing a means for key exchange.
In order to use symmetric encryption, parties must share a key. Although this key could be sent over an existing encrypted channel, we wouldn’t need a new key if we already had a secure channel. Instead, we solve the key exchange problem using public-key cryptography.
Here are two common methods for exchanging symmetric keys.
- Asymmetric encryption. One party generates a symmetric key, then encrypts the key using an algorithm like RSA-OAEP to another party’s public key. The recipient can decrypt the ciphertext using their private key to recover the symmetric key.
- Diffie-Hellman Key Exchange – (DH). Diffie-Hellman is a different type of public-key cryptographic algorithm specifically designed to help parties agree on a symmetric key in the absence of a secure channel. Diffie-Hellman is based on a different mathematical problem than the RSA function, and is less flexible than RSA. However, it does have more efficient constructions, which make it preferable in some use cases.
This combination of public-key cryptography for key exchange and symmetric encryption for bulk data encryption is known as hybrid encryption.
Hybrid encryption uses the unique properties of public-key cryptography for exchanging secret information over an untrusted channel with the efficiency of symmetric encryption. This achieves a practical end-to-end solution for data privacy.
Hybrid encryption is used extensively in data transfer protocols for the web, such as in Transport Layer Security (TLS). When you connect to a website that uses HTTPS (HTTP secure with TLS), your browser will negotiate the cryptographic algorithms that secure your connection. These include algorithms for key exchange, symmetric encryption, and digital signatures.
What is a digital signature?
Digital signature schemes are a type of public-key cryptography that ensures integrity, authenticity, and non-repudiation of data.
The signing process can be thought of much like encrypting the file using the private key. The signer uses their private key to produce a “signature” on a digital document such as a file or a piece of code.
This signature is unique to the document/ private key pair, and can be attached to the document and verified with the signer’s public key. Two common algorithms for digital signatures are RSA with Probabilistic Signature Scheme (RSA-PSS) and Digital Signature Algorithm (DSA).
What is a message authentication code?
A message authentication code (MAC) is the symmetric version of a digital signature. With a MAC, two or more parties share a key. One party creates a MAC tag, which is the symmetric version of a digital signature, and attaches it to the document. Another party can verify the message’s integrity using the same key used to create the tag.
Note that multiple parties share the key used to create MAC tags, so MACs cannot be used for authentication or non-repudiation since it isn’t clear which party created the tag.
MACs can be standalone algorithms, such as hash-based message authentication code (HMAC). However, since message integrity is almost always a valuable assurance, it is frequently integrated into symmetric encryption algorithms like AES-GCM.
What is elliptic-curve cryptography?
Elliptic-curve cryptography (ECC) is a public-key cryptography technique based on the mathematical theory of elliptic curves.
The biggest advantage of ECC is that it can provide a similar level of protection as more traditional techniques, but with smaller keys and faster operations. The efficiency of ECC makes it well suited for use in devices with relatively low computational power, such as mobile phones.
ECC can be used for efficient key exchange using an elliptic-curve variant of Diffie-Hellman (ECDH) or for digital signatures using the Elliptic Curve Digital Signature Algorithm (ECDSA). Because of its speed and flexibility, ECC is widely utilized across many applications across the internet.
What is hashing in cryptography?
A cryptographic hash function is a tool for turning arbitrary data into a fixed-length “fingerprint”. Hash functions are designed so that it is hard to find two different inputs that have the same fingerprint, and it is difficult to find a message whose fingerprint matches a fixed value.
Unlike encryption schemes, signature schemes, and MACs, hash functions do not have a key. Anyone can compute the hash of a given input and the hash function will always produce the same output on the same input.
Hash functions are an important building block in larger cryptographic algorithms and protocols. These include digital signature algorithms, dedicated MAC algorithms, authentication protocols, and password storage.
What is cryptocurrency?
Cryptocurrency is a digital currency in which transactions are verified and records maintained by a decentralized system, rather than by a centralized authority. Cryptocurrency is an example of an application of cryptography.
Cryptocurrency uses many different low-level cryptographic algorithms to create a trusted and secure platform. Cryptocurrency uses many of the concepts discussed on this page—elliptic-curve cryptography, digital signatures, hash functions, and many more. Together, these algorithms allow trust and accountability to be built without a centralized authority.
What is post-quantum cryptography?
Over the past few decades there has been significant investment in quantum computing. Quantum computers use quantum physics and can solve mathematical problems, such as the factoring problem, that are computationally infeasible for classical computers.
A large-scale quantum computer would break the public-key cryptosystems we use today, including cryptosystems based on Rivest-Shamir-Adleman (RSA) functions. A break in these algorithms would mean the loss of confidentiality and authentication of many of the applications and protocols we use today.
Although small quantum computers exist today, they are too small to break cryptographic algorithms. It is not known if or when a cryptographically relevant quantum computer (CRQC) will become available. There are significant scientific breakthroughs necessary to develop a CRQC.
Post-quantum cryptography (PQC) refers to cryptographic algorithms that run on the computers we use today, and are not known to be vulnerable against a large-scale quantum computer.
Learn more about AWS research and engineering participation in quantum-resistant cryptography projects and working groups with the global cryptographic community at AWS Post-Quantum Cryptography.
What is cryptographic computing?
The tools introduced so far allow you to use encryption at rest and encryption in transit. Traditionally, data had to be decrypted before it could be used in a computation. Cryptographic computing fills this gap by providing tools to operate directly on cryptographically protected data.
The term cryptographic computing covers a broad range of technologies including secure multi-party computation, homomorphic encryption, and searchable encryption. Though they differ in details, these technologies cryptographically protect data in a way that allows you to perform computation on the protected data while simultaneously preserving the confidentiality of that data.
What cryptographic services does AWS provide to customers?
AWS's cryptographic services utilize a wide range of encryption and storage technologies that can assure the integrity of your data at rest or in transit. AWS offers several tools for cryptographic operations:
- AWS CloudHSM provides hardware security modules (HSMs) that can securely store a variety of cryptographic keys, including root keys and data keys.
- AWS Key Management Service (KMS) provides tools for generating root keys and other data keys. AWS KMS also interacts with many other AWS services to encrypt their service-specific data.
- AWS Encryption SDK provides a client-side encryption library for implementing encryption and decryption operations on all types of data.
- Amazon DynamoDB Encryption Client provides a client-side encryption library for encrypting data tables before sending them to a database service, such as Amazon DynamoDB.
- AWS Secrets Manager provides encryption and rotation of encrypted secrets used with AWS-supported databases.
Many AWS services rely on these cryptographic services during data transfer or storage. For a list of such services and an overview of how they use cryptographic practices, see Other AWS Services.
AWS also provides open-source cryptographic libraries:
- AWS libcrypto (AWS-LC) provides a general-purpose cryptographic library maintained by the AWS Cryptography team for AWS and their customers. It іs based on code from the Google BoringSSL project and the OpenSSL project. AWS-LC contains portable C implementations of algorithms needed for TLS and common applications. For performance critical algorithms, optimized assembly versions are included for x86 and ARM.
- s2n-tls provides an implementation of the TLS/SSL protocols that is designed to be simple, small, fast, and with security as a priority.
You can also check out the Amazon Science Blog and the AWS Security Blog. There we detail what we're doing to develop, benchmark and prototype cryptographic research. We write about cryptographic computing, post-quantum cryptography, verified cryptographic code, and more.
How can I use cryptographic services in AWS that are compliant with a governmental or professional regulation?
AWS cryptographic services comply with a wide range of cryptographic security standards, making it easy for you to protect your data without worrying about governmental or professional regulations. For a full list of AWS data security standard compliances, see AWS Compliance Programs.


