
Overview
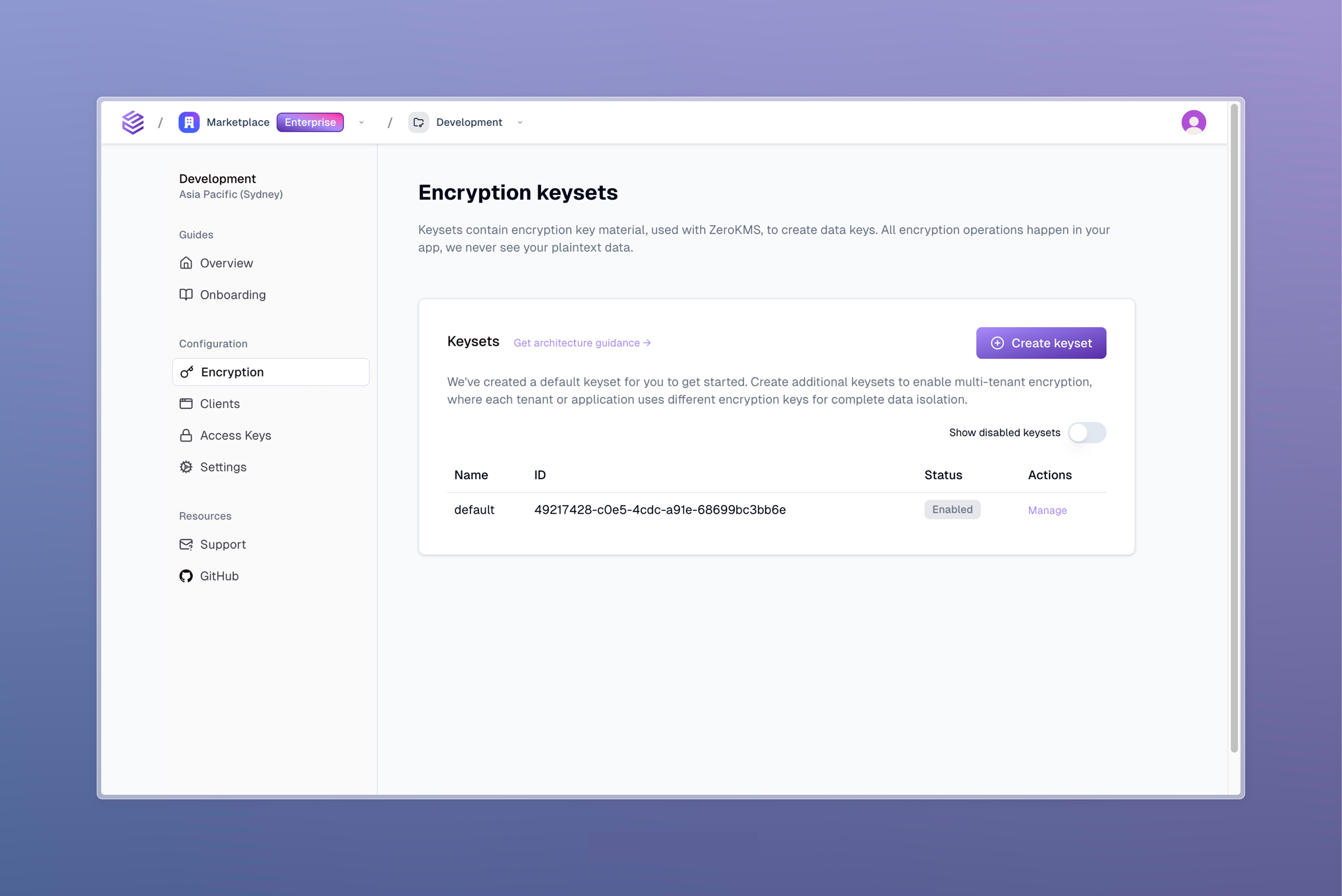
CipherStash Management Dashboard
Manage keysets and other operational actions directly in the CipherStash dashboard or through our APIs.

CipherStash Management Dashboard
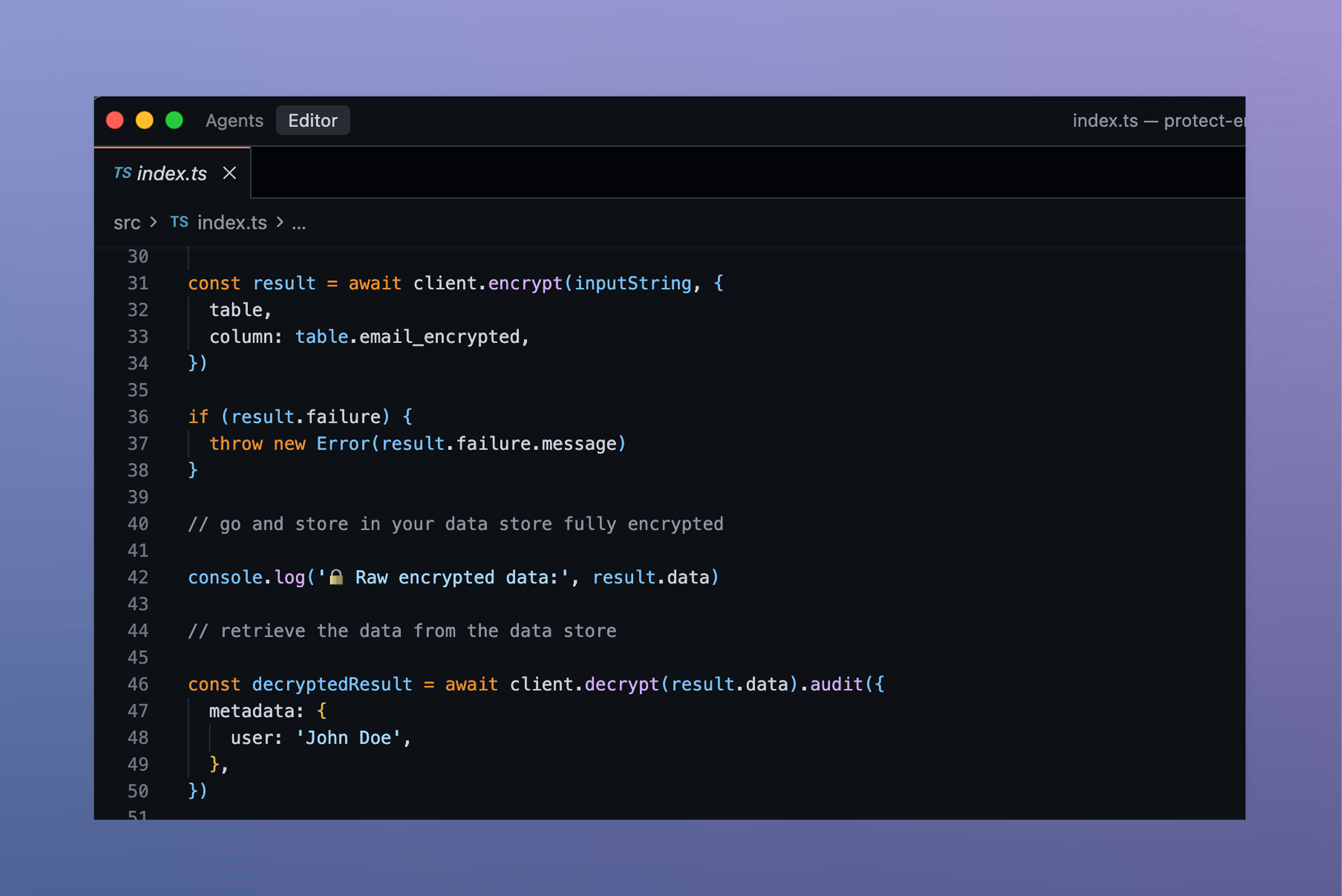
CipherStash TypeScript SDK
CipherStash believes organizations shouldn't have to choose between protecting their data or using it to drive growth. Together with AWS, CipherStash gives teams the confidence to collect and use high-value, sensitive data knowing it will be continuously protected, correctly governed, and fully auditable. By combining CipherStash with AWS-native services like KMS, RDS, DynamoDB, Aurora, and IAM, companies can think differently about how they use data to grow their business while still meeting security, compliance, and customer expectations. CipherStash ZeroKMS delivers searchable encryption, identity-aware encryption, and true zero-trust key management, all designed for enterprise scale on AWS. Keys are derived on demand and never stored, reducing storage overhead and improving security, while high-performance key generation delivers up to 10,000 keys per second per node for both single and bulk operations.
Using language-specific SDKs (including TypeScript and Go), developers can enable fully searchable encryption, automatic key rotation, multi-tenant encryption with Keysets, and encryption lock contexts that enforce attribute-based access control using cryptographic proofs.
With identity-bound access controls that integrate with AWS IAM and identity providers like Auth0, Okta, and Clerk, CipherStash ensures both client and server must independently consent to every key operation, and data keys are never shared, making revocation instant.
Real-time access auditing provides full-context logs to help meet SOC 2, HIPAA, and GDPR requirements on AWS, turning data access into a provable, continuously monitored control surface. For specialized configurations and contract pricing for CipherStash on AWS Marketplace, contact sales@cipherstash.com .
Highlights
- Searchable encryption with ZeroKMS: Enable high-performance, zero-trust key management with on-demand key derivation.
- Identity-aware, zero-trust access controls: Enforce fine-grained, identity-bound access using AWS IAM or providers like Auth0, Okta, and Clerk, with cryptographically isolated multi-tenant encryption and instant key revocation.
- Continuous compliance and real-time auditing: Strengthen security posture with full-context audit logs to support SOC 2, HIPAA, and GDPR, while preserving developer productivity with language-specific SDKs that make searchable encryption simple to deploy.
Details
Introducing multi-product solutions
You can now purchase comprehensive solutions tailored to use cases and industries.

Features and programs
Financing for AWS Marketplace purchases

Pricing
Dimension | Description | Cost/unit |
|---|---|---|
Usage | Unit based pricing | $0.001 |
Vendor refund policy
Refer to the terms of service.
Custom pricing options
How can we make this page better?

Legal
Vendor terms and conditions
Content disclaimer
Delivery details
Software as a Service (SaaS)
SaaS delivers cloud-based software applications directly to customers over the internet. You can access these applications through a subscription model. You will pay recurring monthly usage fees through your AWS bill, while AWS handles deployment and infrastructure management, ensuring scalability, reliability, and seamless integration with other AWS services.
Support
Vendor support
Service Level Agreements (SLAs)
- For non-urgent support requests, CipherStash will respond within 1 business day.
- For support requests that indicate service availability or core functionality is impacted, CipherStash will respond within 4 hours.
Support Services
- Create support tickets by emailing support@cipherstash.com .
AWS infrastructure support
AWS Support is a one-on-one, fast-response support channel that is staffed 24x7x365 with experienced and technical support engineers. The service helps customers of all sizes and technical abilities to successfully utilize the products and features provided by Amazon Web Services.