
Overview
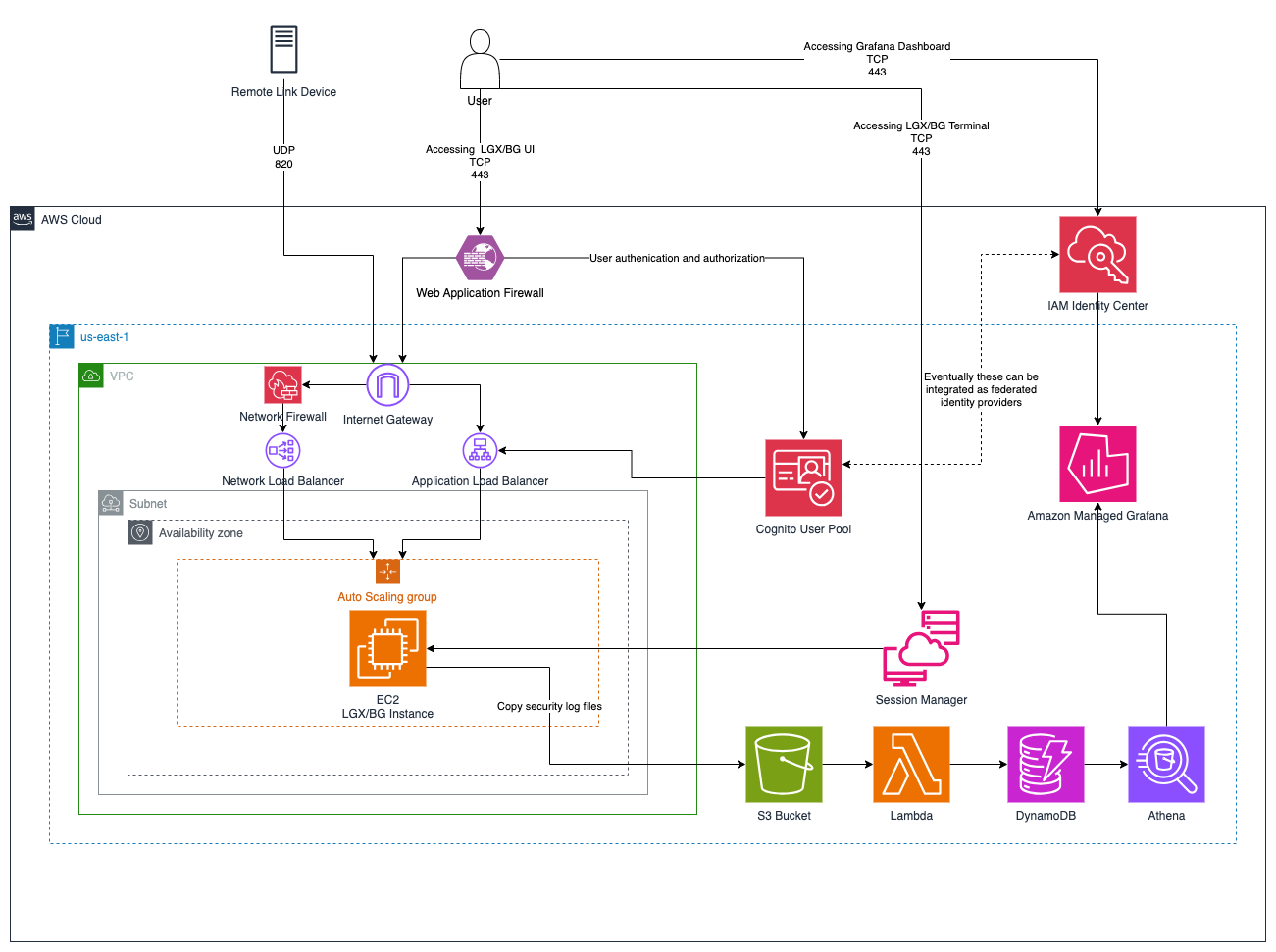
Architecture diagram
CyberCloak Cloud on AWS is a cloud-native, hardened virtual appliance designed to bring Blue Ridge Networks trusted zero-trust security to cloud environments. It enables secure Layer 2 encrypted tunnels between remote sites, edge devices, and AWS-hosted resources, without requiring changes to your existing network configuration. CyberCloak Cloud builds on the proven success of LinkGuard Express, a widely deployed solution known for protecting critical infrastructure with simplicity and reliability. As organizations increasingly adopted cloud and hybrid architectures, the need for a flexible and secure cloud-based solution became clear. CyberCloak Cloud was developed to meet that need, providing the same level of protection in a scalable, cloud-native form. The solution is easy to integrate into your AWS environment. It is available as a preconfigured Amazon Machine Image (AMI) in AWS Marketplace, allowing you to subscribe and deploy in minutes. You can quickly establish secure connections between your cloud workloads and on-premise systems, or securely connect remote users and edge devices to your AWS infrastructure. CyberCloak Cloud supports full Layer 2 tunneling, making it ideal for environments that rely on legacy protocols, tightly coupled applications, or latency-sensitive systems. It delivers end-to-end encryption from the very first packet and cloaks protected resources from unauthorized discovery or access. The pricing model is affordable and usage-based, scaling with your needs. There are no hidden fees or complex licensing requirements. You only pay for what you use. Whether you need to extend secure access from edge to cloud or bring cloud workloads closer to on-premise operations, CyberCloak Cloud gives you the control, visibility, and protection you need in a cloud-native form.
Highlights
- Rapid deployment and easily integrates into existing environments without re-architecting critical systems
- Overlay solution is protocol agnostic and protects network and devices without the need to modify existing networks.
- Data transfers encrypted from the very first packet
Details
Introducing multi-product solutions
You can now purchase comprehensive solutions tailored to use cases and industries.

Features and programs
Financing for AWS Marketplace purchases

Pricing
Vendor refund policy
All purchases are non-refundable once a license key is issued and activated. This product is BYOL; all billing and refund requests are handled directly by Blue Ridge Networks. Refunds may be considered prior to activation, at our sole discretion. No refunds for partial use or expired licenses. Failure to maintain updates or system compatibility does not qualify for a refund.
How can we make this page better?

Legal
Vendor terms and conditions
Content disclaimer
Delivery details
Easy Deployment
This template automatically deploys the CyberCloak secure access environment, including VPC, networking, security groups, identity services, load balancer, and the CyberCloak compute instance. It creates a dedicated VPC with public, private, and isolated enclave subnets; configures routing, NAT, and Internet access; and deploys strict security policies for management and encrypted DPF tunnel traffic. The stack also provisions AWS Cognito for admin authentication with MFA and role-based access, launches the CyberCloak EC2 instance with required IAM permissions, and auto-configures CyberCloak networking, enclave bridge settings, and authentication integration. A Network Load Balancer is created to provide access to the management UI (TCP 443) and secure tunnel services (UDP 820), with health checks and fail-safe routing. Outputs include the load balancer DNS name and Cognito identifiers to complete initial setup. Use this template for a one-step automated deployment of a ready-to-use CyberCloak zero-trust environment.
CloudFormation Template (CFT)
AWS CloudFormation templates are JSON or YAML-formatted text files that simplify provisioning and management on AWS. The templates describe the service or application architecture you want to deploy, and AWS CloudFormation uses those templates to provision and configure the required services (such as Amazon EC2 instances or Amazon RDS DB instances). The deployed application and associated resources are called a "stack."
Additional details
Usage instructions
The relevant product documentation from the link below: CyberCloak Deployment Guide: https://marketplace-assets-108216259777.s3.us-east-1.amazonaws.com/Documentation/CyberCloak+Deployment+Guide.pdf List of allowed instances: https://marketplace-assets-108216259777.s3.us-east-1.amazonaws.com/Documentation/Allowed+instances.htm
Support
Vendor support
support@blueridgenetworks.com , +1 (800) 722-1168, <www.blueridgenetworks.com >
AWS infrastructure support
AWS Support is a one-on-one, fast-response support channel that is staffed 24x7x365 with experienced and technical support engineers. The service helps customers of all sizes and technical abilities to successfully utilize the products and features provided by Amazon Web Services.