
Overview
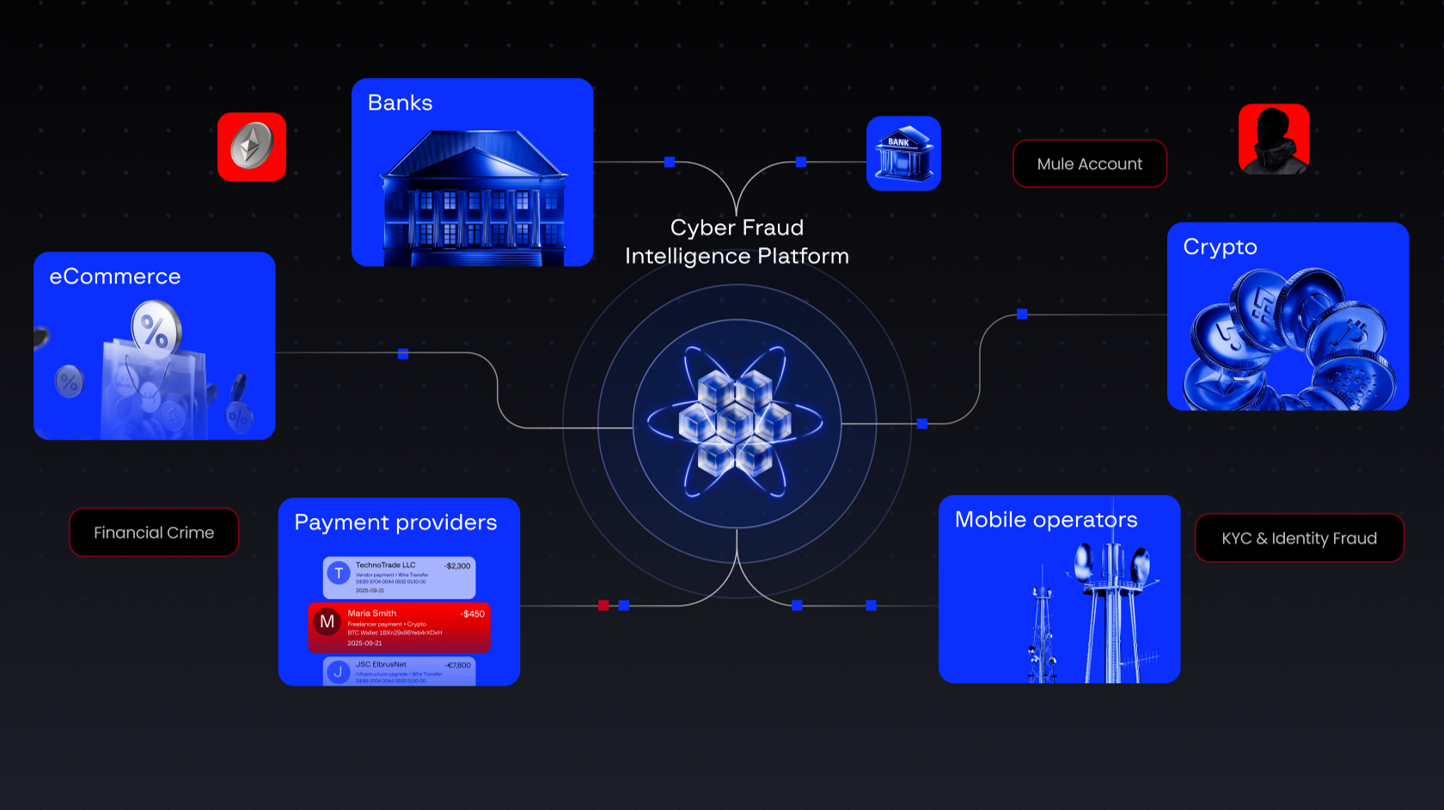
Cyber Fraud Protection Platfrom
Banks, crypto, telco, and merchants collaborating to stop cross-platform fraud without sharing PII.

Cyber Fraud Protection Platfrom

Product video
Secure Payment Tokenization & Collaborative Fraud Defense
The CFIP Connector is a high-security, headless containerized application designed to run on AWS Fargate. It acts as a secure gateway for your payment data, stripping sensitive PII (PANs) and replacing them with anonymized tokens before they ever touch your general storage.
Key Features:
PCI Scope Reduction: Deploys into a dedicated VPC to isolate cardholder data from your main environment.
Headless Architecture: Fully automated via API and Queue integration; no GUI management required.
Zero Ingress Security: Designed to run with "Deny All Inbound" security groups for maximum protection.
Collaborative Intelligence: Safely exchange risk signals with other financial institutions without sharing raw data.
Deployment Note: This product is delivered as a Docker Container. For a secure, PCI-aligned deployment, please use our official CloudFormation Template (linked in the usage instructions) to provision the required Fargate Cluster, KMS Keys, and Private VPCs.
Highlights
- Collaborative Fraud Intelligence: Enables participating institutions to securely exchange risk signals using privacy-preserving cryptographic blinding without exposing PII.
- Zero-Ingress Nitro Architecture: Features a strict "deny-all" inbound design with no interactive access (no SSH/SMM), ensuring a zero-trust, audit-ready environment for high-volume transactions.
- Designed to integrate seamlessly with existing risk platforms as a high-performance enrichment layer, requiring zero replacement of legacy fraud detection systems.
Details
Introducing multi-product solutions
You can now purchase comprehensive solutions tailored to use cases and industries.

Features and programs
Financing for AWS Marketplace purchases

Pricing
Dimension | Description | Cost/unit |
|---|---|---|
Completed Risk Analysis | A billable unit is counted when the Connector sucessfully receives a response | $1.00 |
Vendor refund policy
No refunds are provided for this product. All sales are final and subject to the specific terms and conditions outlined in your accepted Private Offer
Custom pricing options
How can we make this page better?

Legal
Vendor terms and conditions
Content disclaimer
Delivery details
CFIP Connector Image
- Amazon ECS
- Amazon EKS
- Amazon ECS Anywhere
- Amazon EKS Anywhere
Container image
Containers are lightweight, portable execution environments that wrap server application software in a filesystem that includes everything it needs to run. Container applications run on supported container runtimes and orchestration services, such as Amazon Elastic Container Service (Amazon ECS) or Amazon Elastic Kubernetes Service (Amazon EKS). Both eliminate the need for you to install and operate your own container orchestration software by managing and scheduling containers on a scalable cluster of virtual machines.
Version release notes
his release introduces support for Confidential Computing via AWS Nitro Enclaves. Sensitive metering and fraud intelligence workloads are now processed in a fully isolated, hardware-encrypted environment with no interactive access or external networking, providing our most secure connector experience to date
Additional details
Usage instructions
Usage instructions Group-IB CFIP Connector: Usage Instructions
-
Product Overview The CFIP Connector is a lightweight containerized application responsible for the cryptographic blinding of sensitive data (e.g., PANs, PII) before it leaves your environment. It runs within your VPC (ECS Fargate or EC2).
-
Prerequisites IAM Role: The Task Execution Role must allow kms:Decrypt (for the blinding key) and aws-marketplace:MeterUsage (for billing). Network: Outbound HTTPS (443) access to the Group-IB Coordinator Endpoint. Secret Management: A Customer Managed Key (CMK) in AWS KMS to secure the Blinding Factor.
-
Launch Instructions (ECS Fargate Example) Create a Task Definition: Select the Group-IB CFIP image from your Marketplace subscriptions. Configure Environment Variables: You must pass the following variables to the container: COORDINATOR_URL: The endpoint URL provided by Group-IB. KMS_KEY_ARN: The ARN of your AWS KMS key holding the blinding secret. AWS_REGION: The region where your KMS key is located (e.g., us-east-1). Run the Task: Launch the task in your private subnet.
-
Data Encryption & Sensitive Information Data in Transit: All communication with the Group-IB Coordinator is encrypted via TLS 1.3. Data at Rest: The Connector is stateless and does not persist PII to disk. Key Management: The "Blinding Factor" (private key) is never stored in plain text. It is retrieved securely from AWS KMS at runtime.
-
Health Assessment & Monitoring To verify the application is functioning correctly: Logs: Navigate to Amazon CloudWatch Logs for your ECS Task. Success Signal: Look for the log entry: [INFO] Connection established with Coordinator. Ready to process.
Failure Signal: If you see [ERROR] Connection refused or [ERROR] KMS Access Denied, verify your Security Group rules and IAM policies respectively.
- Service Quotas & Pricing Resource Usage: This container requires minimal resources (approx. 0.5 vCPU / 1 GB RAM per instance). Usage falls under your standard Amazon ECS/EC2 quotas. Licensing: Software usage is billed via AWS Marketplace Metering based on the number of API replies processed. Standard AWS infrastructure charges (e.g., Fargate vCPU hours) apply separately.
Resources
Vendor resources
Support
Vendor support
Support Information Support Email: fraud@eu.group-ib.com fraud@mea.group-ib.com fraud@apac.group-ib.com fraud@amer.group-ib.com
Support URL: https://www.group-ib.com/contacts/
Support Description
Customers who purchase Group-IB Fraud Protection receive 24/7/365 access to our dedicated technical and analytical support teams. Our service includes assistance with initial setup, integration, and ongoing configuration to ensure optimal performance. Buyers can contact our experts via the secure support portal, email, or phone for real-time assistance, threat analysis, and guidance on mitigating fraudulent activity detected by the platform.
AWS infrastructure support
AWS Support is a one-on-one, fast-response support channel that is staffed 24x7x365 with experienced and technical support engineers. The service helps customers of all sizes and technical abilities to successfully utilize the products and features provided by Amazon Web Services.
Similar products



