
Overview
QuProtect R3

QuProtect R3

Product video
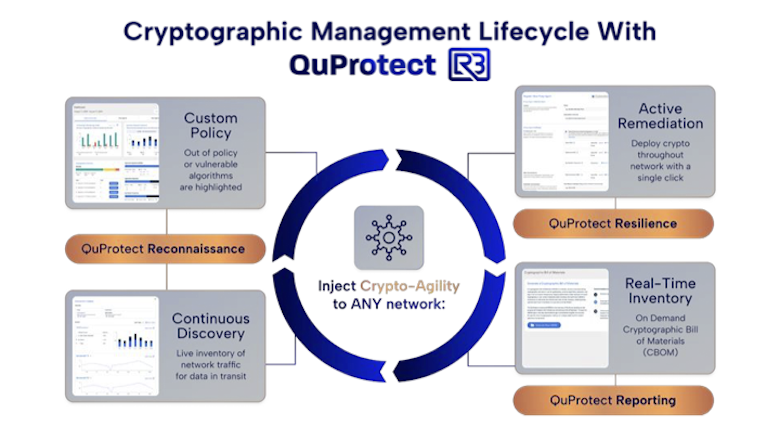
Continuous Discovery. Gain a comprehensive, live inventory of crypto in use to secure network data in transit. Leverage QuProtect Reconnaissance for custom assessments that easily highlight out-of-policy or vulnerable algorithms, providing actionable insights to strengthen your security posture.
Active Remediation. Deploy cryptographic protection across your entire network with ease using QuProtect Resilience. Execute crypto-agility to instantly update encryption across all devices and systems, ensuring adaptive defense without disruptions or code changes, even when algorithms are compromised or new standards emerge.
Real-Time Reporting. Streamline compliance with QuProtect Reporting, offering on-demand visibility and control. Access Cryptographic Bill of Materials (CBOM) to ensure compliance with evolving standards like NIST, FIPS, and GDPR, while maintaining full transparency over your cryptographic inventory.
Highlights
- QuProtect Recon. Discovery. Gain an evergreen inventory of cryptographic assets across cloud, on-prem, and legacy systems in days, not months. See what is actually protecting your data in real-time, not just what is configured in files.
- QuProtect Resilience. Remediation. Rapidly remediate cryptographic risk with clicks, not code changes, no rip-and-replace required. Seamlessly transition to post-quantum cryptography and enhance zero-trust security across all systems.
- QuProtect Reporting. Automated Compliance & Reporting. Generate Cryptographic Bill of Materials (CBOM) reports with a single click for CNSA 2.0, CNSSP 15, and GDPR compliance. Transform operational data into board-ready metrics showing remediation progress and risk reduction over time.
Details
Introducing multi-product solutions
You can now purchase comprehensive solutions tailored to use cases and industries.

Features and programs
Financing for AWS Marketplace purchases

Pricing
Dimension | Description | Cost/month |
|---|---|---|
QuProtect | QuProtect provides secure web app to server, server to server, and router to router communication. | $20,000.00 |
Vendor refund policy
Contact QuSecure @ info@qusecure.com for the refund policy.
Custom pricing options
How can we make this page better?

Legal
Vendor terms and conditions
Content disclaimer
Delivery details
Software as a Service (SaaS)
SaaS delivers cloud-based software applications directly to customers over the internet. You can access these applications through a subscription model. You will pay recurring monthly usage fees through your AWS bill, while AWS handles deployment and infrastructure management, ensuring scalability, reliability, and seamless integration with other AWS services.
Support
Vendor support
Tier 1-3 Support, 8AM-5PM Pacific Time, M-F, contact support@qusecure.com
AWS infrastructure support
AWS Support is a one-on-one, fast-response support channel that is staffed 24x7x365 with experienced and technical support engineers. The service helps customers of all sizes and technical abilities to successfully utilize the products and features provided by Amazon Web Services.


