
Overview
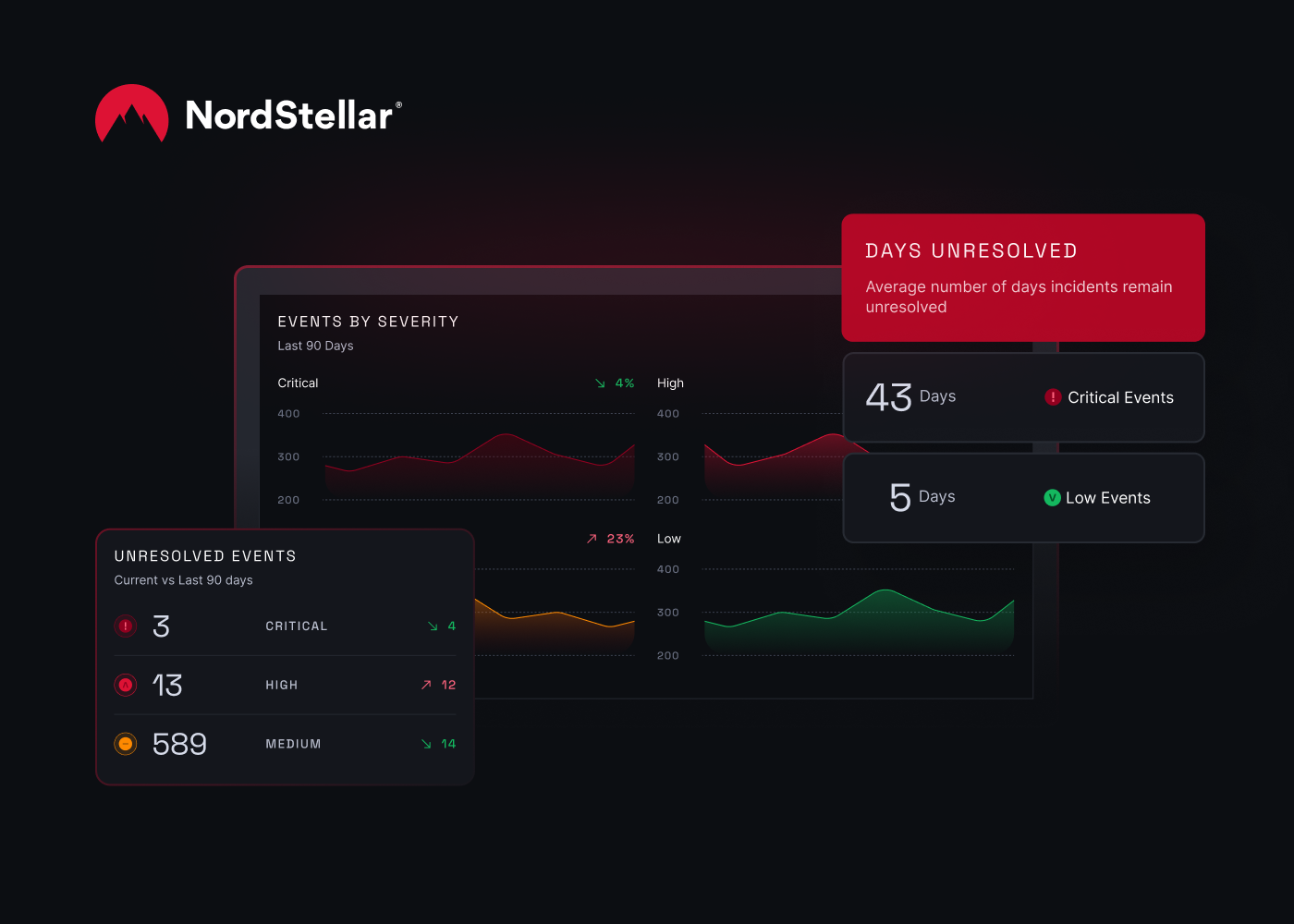
NordStellar Platform

NordStellar Platform
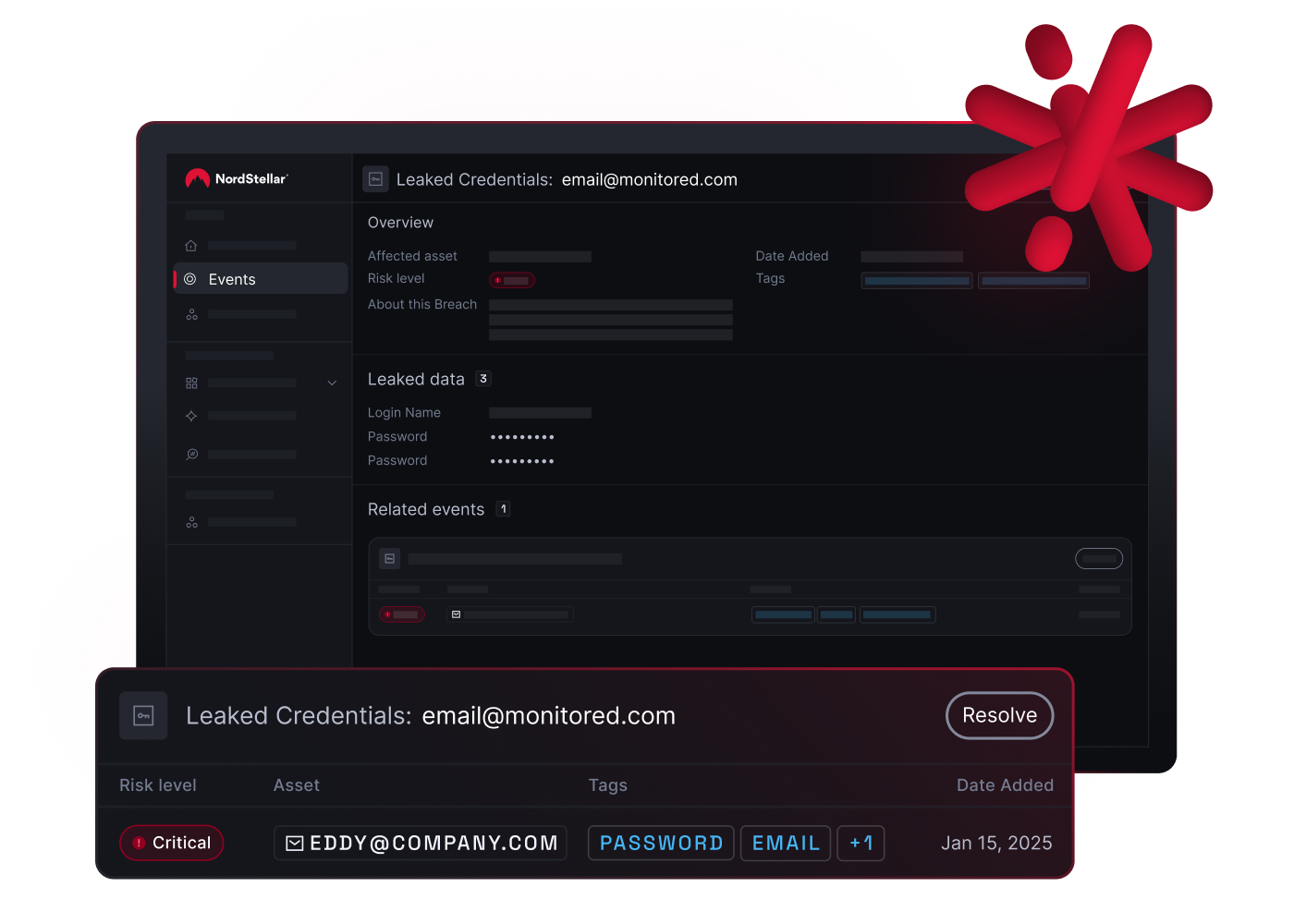
NordStellar Account Takeover Prevention

NordStellar Dar Web Monitoring
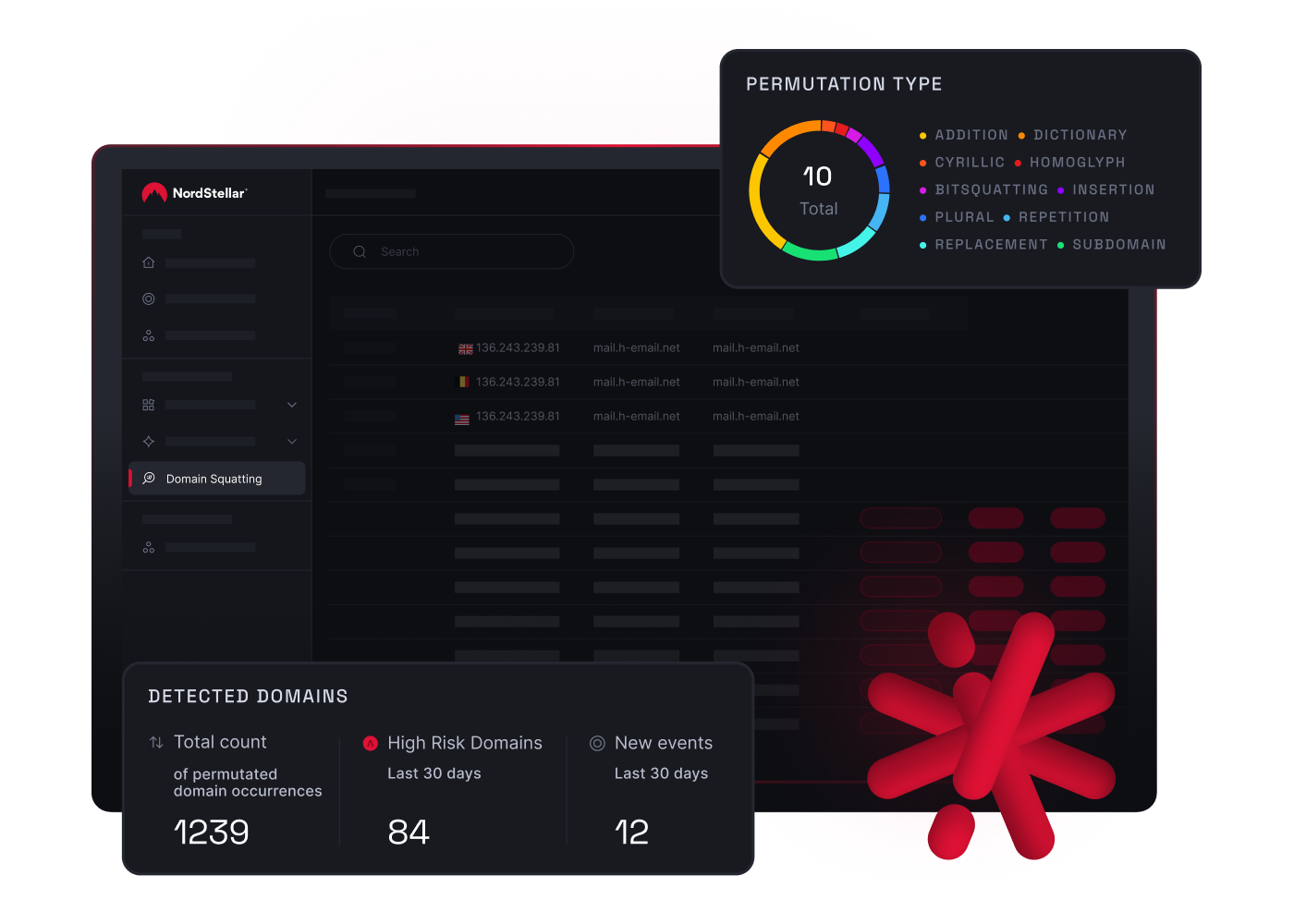
NordStellar Domain Squatting
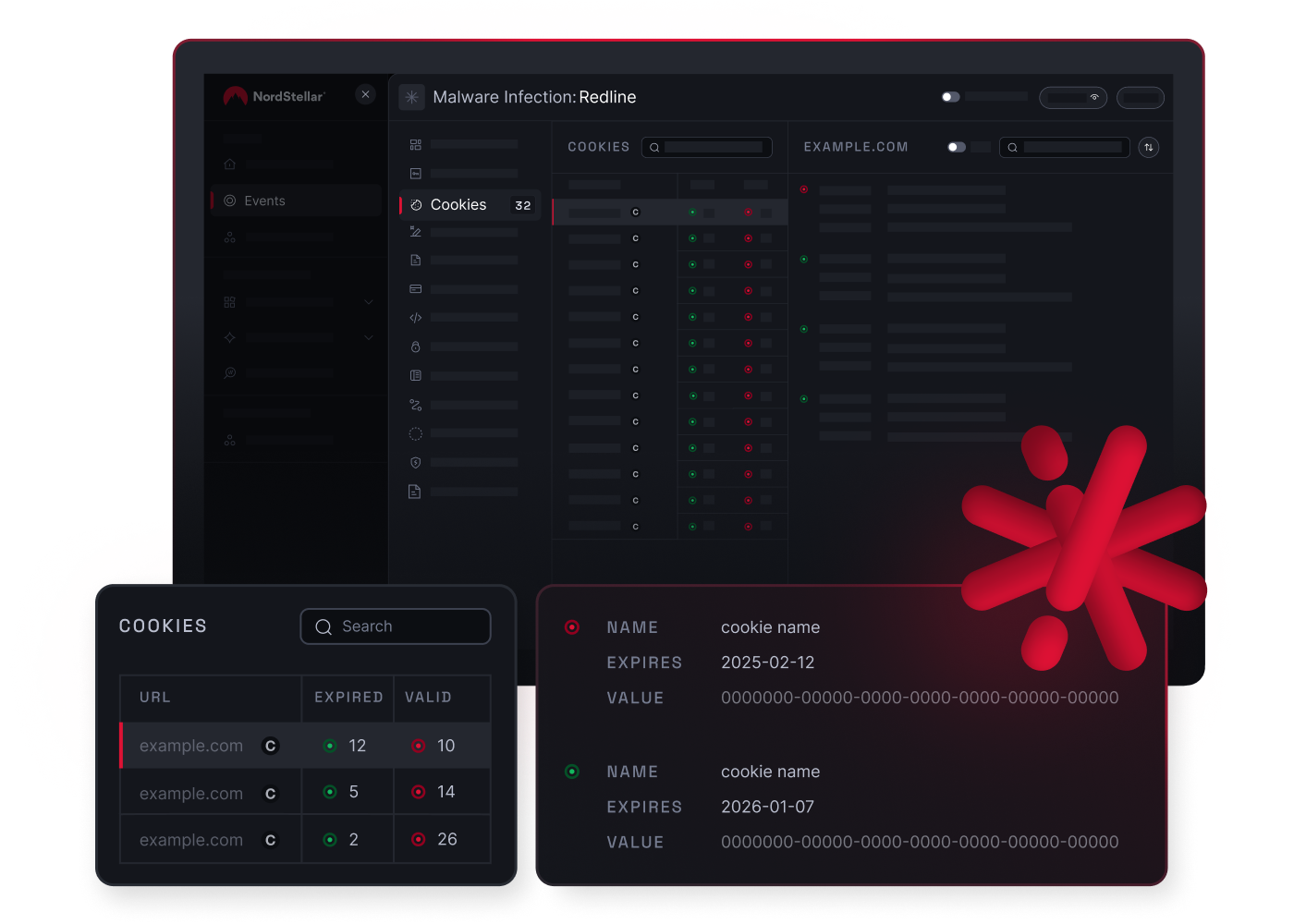
NordStellar Session Hijacking Prevention
NordStellar is a unified Threat Exposure Management (TEM) platform developed by the team behind NordVPN. It empowers security teams to eliminate blind spots and prevent external threats early, before they escalate.
NordStellar 4-in-1 solutions:
- Data Breach Monitoring: Monitors the deep and dark web for employee and consumer data leaks. Detects infostealer logs, stolen session cookies, and credentials to prevent MFA bypass and unauthorized access.
- Dark Web Monitoring: Scans thousands of cybercrime channels for brand mentions while allowing on-demand searches for specific keywords. Tracks ransomware blogs to preempt incoming targeted attacks.
- External Attack Surface Management (EASM): Maps external assets and shadow IT. Identifies and verifies vulnerabilities, providing a prioritized hit-list of critical risks for immediate remediation.
- Brand Protection: Detects typosquatting domains and impersonations across websites, social profiles, and apps. Executes takedowns to protect brand reputation and customer trust.
Strategic Advantages:
- Prevent data leaks early: Stop threats before they escalate into breaches by monitoring the deep and dark web for immediate containment.
- Gain total visibility: Reveal a unified view of your digital footprint, from shadow IT to dark web exposures, eliminating blind spots.
- Prioritize threats: Focus resources on critical exposures using multi-level risk scoring to distinguish noise from real threats.
- Consolidate vendors: Reduce costs by unifying 4 essential solutions into a single, comprehensive platform.
- Simplify compliance: NordStellar contributes to meeting DORA, NIS 2, SOC 2, and ISO 27001 compliance with proactive threat monitoring.
Ready to know what hackers know? Uncover your organization's external risks in a personalized session. Book your walkthrough: https://nordstellar.com/aws-demo-booking/
Highlights
- Unified 4-in-1 visibility: Consolidate Dark Web and Data Breach Intelligence, Attack Surface Management, and Brand Protection into a single dashboard to eliminate tool sprawl and blind spots.
- Industry-leading threat insights: Leverage access to one of the largest deep & dark web data pools in the industry. Detect compromised credentials and infostealer logs that others miss.
- Map shadow IT & assets: Automatically discover exposed network services, forgotten web applications, and vulnerabilities to shrink your external attack surface.
Details
Introducing multi-product solutions
You can now purchase comprehensive solutions tailored to use cases and industries.

Features and programs
Financing for AWS Marketplace purchases

Pricing
Dimension | Description | Cost/12 months |
|---|---|---|
NordStellar Platform | Full cyber threat visibility for business | $20,000.00 |
Vendor refund policy
Refunds available as required by law.
Custom pricing options
How can we make this page better?

Legal
Vendor terms and conditions
Content disclaimer
Delivery details
Software as a Service (SaaS)
SaaS delivers cloud-based software applications directly to customers over the internet. You can access these applications through a subscription model. You will pay recurring monthly usage fees through your AWS bill, while AWS handles deployment and infrastructure management, ensuring scalability, reliability, and seamless integration with other AWS services.
Resources
Vendor resources
Support
Vendor support
Questions? For existing clients, please contact your Account Manager or our 24/7 tech-savvy customer support team at support@nordstellar.com .
AWS infrastructure support
AWS Support is a one-on-one, fast-response support channel that is staffed 24x7x365 with experienced and technical support engineers. The service helps customers of all sizes and technical abilities to successfully utilize the products and features provided by Amazon Web Services.
Customer reviews
Superb Threat Exposure Management Platform
Comprehensive threat insights with minimal setup
Must have in your security arsenal
Solid tool to strengthen overall security
It is also important that the team behind the product listens to the feedback and finds a way to solve the issues. Over a short period, the tool became much more usable, and new sources were added.
All you need to do is to provide the company domain, and you are ready to go.
Really happy about this purchase.