
Overview
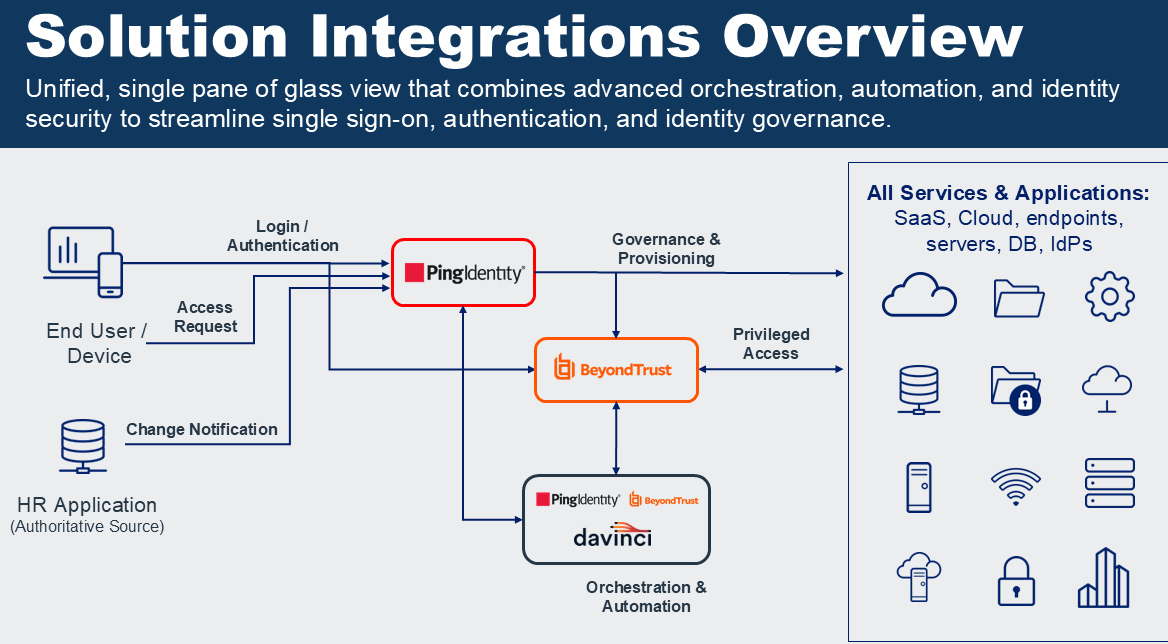
Solution Integration Overview
BeyondTrust and Ping Identity - Unified Identity Security

Solution Integration Overview

Identity Governance & Privileged Access Management

Advanced Application Access Authentication
The BeyondTrust – Ping Identity strategic partnership is much more than just an integration of products. The combined solutions provide a unified identity security fabric enabling a centralized solution for managing, governing, and securing all identities and access pathways. The combined offerings bridge an organization’s security and business outcomes, enabling: operational efficiency (automating JML, reducing manual IT overhead); Improved agility (speeding digital transformation and cloud adoption without slowing access); organizational resilience (continuous identity verification to reduce blast radius of attacks); and addressing regulatory pressures (compliance enabler with automated controls, evidence gathering, and auditability.) Organizations can now automate and orchestrate identity decisions across the entire user and non-human identity lifecycle. Whether granting just enough access for a new employee, revoking privileges at offboarding, or detecting and responding to anomalous behavior in real time, this integrated approach ensures identities are continuously verified and always have the right level of privilege. These joint solutions address three critical needs: 1) Proactive Least Privilege and Zero Standing Privilege Authentication – Enforce just-in-time elevation and adaptive authentication to minimize the attack surface without impacting productivity; 2) Streamlined JML Processes – Ensure fast, accurate provisioning and deprovisioning across all systems and levels of privilege; and 3) AI-Driven Detection and Response – Automatically identify security hygiene and risky behavior and trigger workflows to suspend or terminate access Together, BeyondTrust and Ping deliver a truly scalable identity security architecture that reduces risks, accelerates governed access, and maximizes the value of existing identity investments without sacrificing control or productivity.
Use cases
Application Security
Govern Conditional Access and Enhance Productivity - Add smart and streamlined Just-in-Time access and MFA to applications and data. PingOne + EPM or Insights is a scalable, automated solution that automates access provisioning. Featuring contextual self-service access, Integrated MFA & SSO, and advanced application access authentication.
Identity Management and Access Control
Unify Identity Governance & Privileged Access Management - Ensure access risks are automatically lowered when employees join, change roles, or leave. PingOne’s identity governance + Password Safe & Insights bring full management of Centralized Identity Security to security teams. They provide visibility into ungoverned Identities, unmanaged access and questionable privileges with Policy-Based Access Control that enforce least privilege and adaptive access policies based on user context and risk.
Managed Detection and Response
Automate Threat Response & Session Termination - A faster, simpler process to handle security incidents — from detecting them to ending privileged access for IT staff and outside contractors. No-Code Orchestration using PingOne DaVinci enables drag-and-drop workflow creation for access approvals, provisioning, and revocation. While advanced privilege detection and visibility from Privileged Remote Access supports human, non-human and machine identity trust, and behavioral analytics.
Details
Introducing multi-product solutions
You can now purchase comprehensive solutions tailored to use cases and industries.

Products included



Features and programs
Financing for AWS Marketplace purchases

Pricing
Custom pricing options
Integration guide
The joint BeyondTrust – Ping solution is much more than just an integration of products. Through the use of APIs, connectors and workflows, the combined solutions use this data to build identity analytics, detect identity security threats, and make security recommendations. The combined solution provides a unified identity security fabric enabling a centralized solution for managing, governing, and securing all identities and access pathways. Contact us for more details.
How can we make this page better?
