什麼是 AWS 上的偵測與回應?
AWS 偵測與回應服務藉助統一安全解決方案中的整合式安全功能,助力您保護雲端環境。憑藉這些服務,您可關聯並擴充威脅與漏洞等安全訊號,持續偵測關鍵問題並確定優先級,從而能夠顯示作用中安全風險並確定優先級,以及大規模精簡回應,進而為您的雲端環境提供防護。
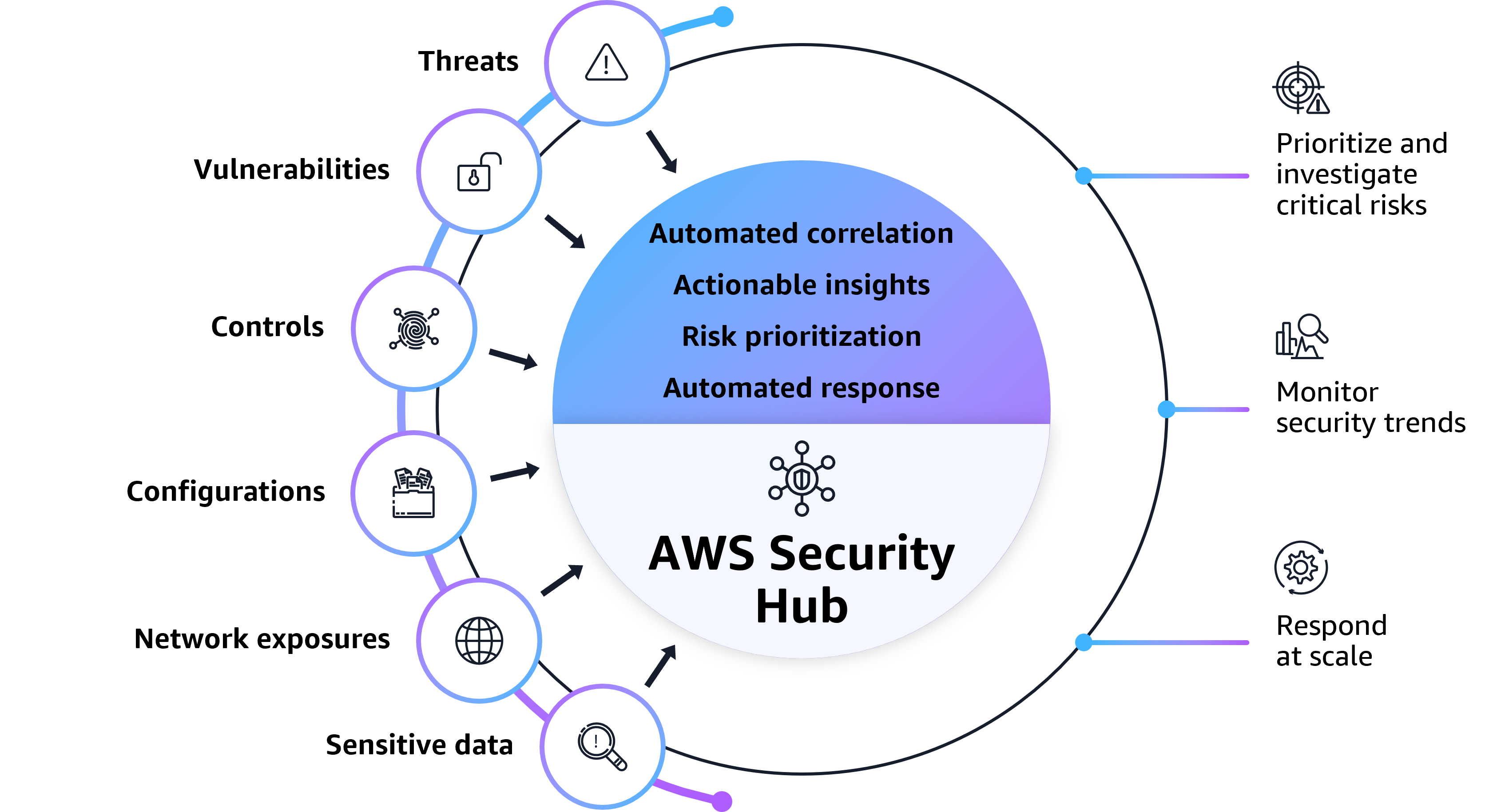
概觀
藉助自動化關聯並擴充安全訊號,例如威脅與漏洞,來持續偵測關鍵問題並確定優先級,進而協助您的組織在 AWS 上更安全地營運。
憑藉統一安全解決方案的集中式管理,並彙總您的帳戶與區域中 AWS 服務及合作夥伴產品的安全資料,在您的雲端環境中實現更廣泛的安全可視性。
憑藉切實可行的洞察與自動化工作流程,顯示作用中風險並確定優先級,從而大規模實現精簡回應。
標準化與整合雲端和內部部署來源的安全資料,獲得安全性全面檢視,並善用您喜好的分析工具來調查和回應事件,同時保留對資料的控制和擁有權。
開始使用 AWS 上的偵測和回應
使用案例
跨多項安全服務、集中式管理,以及標準化控制項採用統一訊號,來顯示作用中風險,藉此降低營運複雜性。
進一步了解 AWS Security Hub
近乎即時地自動探索漏洞調查結果,並快速將其傳送給相應的團隊,以便其立即採取行動。
持續偵測和修復雲端資源設定錯誤和合規風險,以確保您的環境依據安全最佳實務運作。
進一步了解 AWS Security Hub
保護您的帳戶和工作負載免受潛在威脅的侵害,利用自動化精簡威脅回應,並透過加速修復和恢復時間來最大限度地減少業務影響。
探索並保護敏感資料和工作負載,以提高可視性,並自動修復資料安全風險。
進一步了解 Amazon Macie。
Expedia
Expedia 需要了解全球和本地的合規要求,以及能夠處理、分析和控制我們產生的大量資料。我們在 Amazon Macie 的基礎上建置了 AWS 解決方案,協助我們自動執行資料掃描、標記、取樣和識別,以及實作規則設定、產生指標及擴展安全控制。Macie 是解決方案的核心,我們可減少敏感資料的佔用空間。透過減少個人識別資料,我們可向分析師開放資料存取,同時減少風險,並為我們的客戶提供強大且豐富的體驗。
Expedia 集團首席工程師 Aaron Miller

精選影片
部落格
載入中
載入中
載入中
載入中
載入中