- AWS Solutions Library›
- Guidance for Multi-Account Environments on Amazon QuickSight
Guidance for Multi-Account Environments on Amazon QuickSight
Overview
How it works
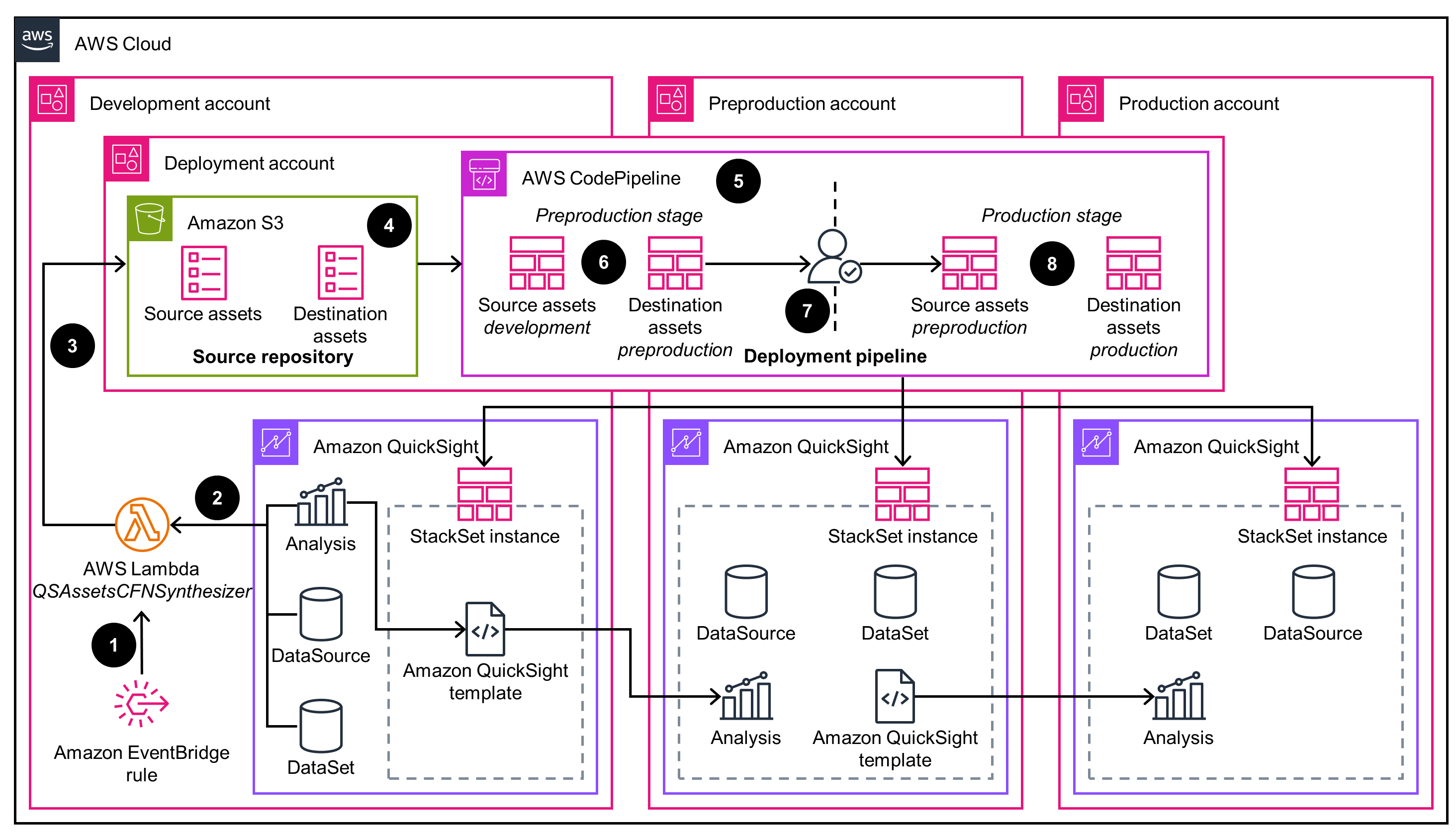
Amazon QuickSight template
There are two deployment modes for this Guidance, the first one uses an Amazon QuickSight template, the second uses an asset bundle API. This architecture diagram displays the configuration of deploying a QuickSight template. For details on the asset bundle API deployment mode, refer to the next tab.
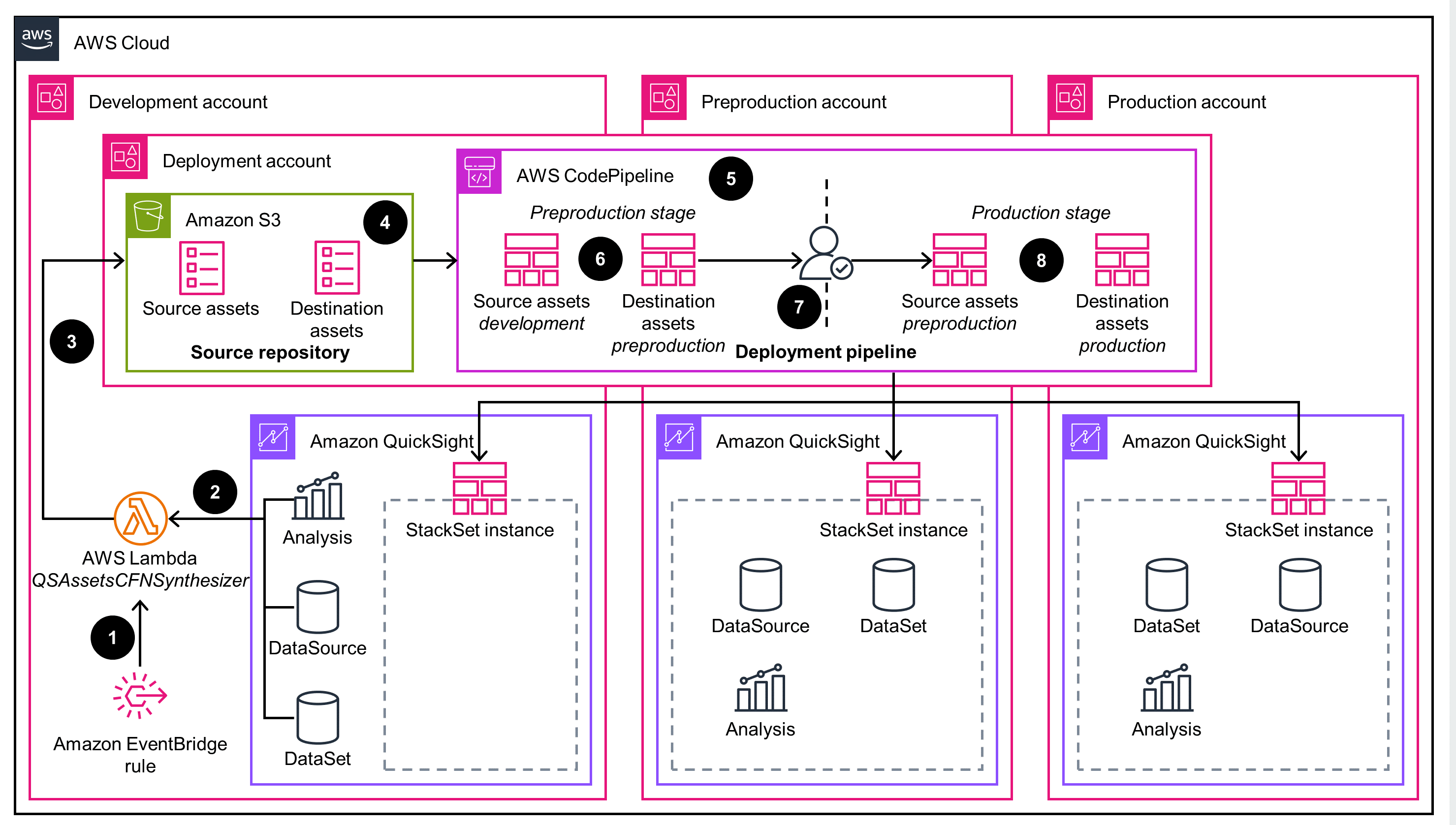
Asset Bundle API
This architecture diagram displays the asset bundle API deployment mode.
Well-Architected Pillars
The architecture diagram above is an example of a Solution created with Well-Architected best practices in mind. To be fully Well-Architected, you should follow as many Well-Architected best practices as possible.
CodePipeline provides continuous delivery across different environments or stages without human intervention. This helps you reduce maintenance, complexity, and the introduction of errors. Additionally, you can configure a manual approval action, sent to an Amazon Simple Notification Service (Amazon SNS) topic, to prevent unwanted changes from reaching critical environments, such as production. CodePipeline uses CloudFormation to deploy assets in a repeatable, auditable, and scalable way, managing the entire asset lifecycle. For auditability, Lambda sends logs that are useful for visibility and troubleshooting.
In this Guidance, AWS Identity and Access Management (IAM) resource policies have all been scoped down to the minimum permissions required for the resources to work properly. IAM also allows audited and authorized access to assets between accounts. For example, the Lambda function can upload data to a bucket in a different account by assuming an IAM role as an identity. Additionally, AWS Key Management Service (AWS KMS) encrypts content that is sent to the Amazon SNS topic, both in transit and at rest, until it is delivered through the selected method (such as email).
QuickSight , CloudFormation , and Lambda are Regional AWS managed services that are designed for reliability and fault tolerance. These services help make the solution secure, reliable, and scalable while reducing its complexity. Additionally, Lambda and CloudFormation play a key role in deploying resources across accounts, providing an extra layer of isolation (such as for different software lifecycle environments) and a disaster recovery environment.
CloudFormation provides a simple, reliable, and repeatable way to deploy your assets across AWS accounts or AWS Regions within minutes. By using it (as a deployment provider) in conjunction with CodePipeline , you can automate the deployment of changes across all environments. Through QuickSight and the ability to implement continuous deployment of assets, you can democratize access to business intelligence tools at scale in your company, making data consumption easier. This also improves your company’s agility in experimenting and developing new functionalities or features.
Lambda , CodePipeline , and QuickSight are serverless, so you can avoid the cost of maintaining your own servers. Additionally, they scale up and down based on demand, helping you reduce costs by only paying for the resources you use. For CodePipeline , you only pay for each pipeline that is active per month, and because CloudFormation is used as the deployment provider, there are no deployment costs. For Lambda , you pay only for the implementation time and memory that your functions use. Finally, for QuickSight , you pay for provisioned authors, and you pay when readers access the platform. However, QuickSight charges only up to a maximum price to keep costs predictable.
Due to their serverless nature, Lambda , CodePipeline , Amazon S3 , and QuickSight can dynamically scale based on demand, which means that resources never run when they are not needed. This helps minimize emissions and their associated environmental impact. Additionally, this Guidance uses an Amazon S3 lifecycle feature that automatically deletes assets based on an age and version history rules, helping reduce the resources dedicated to storage.
Deploy with confidence
Ready to deploy? Review the sample code on GitHub for detailed deployment instructions to deploy as-is or customize to fit your needs.
Disclaimer
Did you find what you were looking for today?
Let us know so we can improve the quality of the content on our pages