AWS News Blog
Launch – Amazon Cognito User Pools General Availability: App Integration and Federation
Recently I was reading articles on Forbes.com, as well as, some other tech-focused websites around mobile user experience, engagement, and development. Almost every article, it mentions that the success of a mobile app development project is dependent upon the delivery of a well-designed user onboarding experience and an engaging mobile interface. An Inc.com article states that over 90% of all downloaded apps used only once and then removed. The number 3 reason noted for users deleting mobile applications from their devices was a poor user experience and interface design. In addition, a subsequent article shares that one of the rules of mobile application engagement is to “Focus on quick wins during onboarding”.
Implementing a smooth mobile user experience is not easy, and I speak from experience as a developer who has built many mobile apps where each time I have struggled to build the user interface of the mobile application. Since identity is mission critical for applications, and it is usually the first entry point when onboarding users onto most mobile and web applications to present these capabilities in a fluid and seamless user interface. Therefore, I am exultant over AWS Cognito User Pools – App Integration and Federation and thrilled to announce the general availability of this new service feature.
Just in case you have not taken advantage of Amazon Cognito as of yet, let me introduce you to the service. Amazon Cognito is a managed cloud service that allows you to add authentication, authorization, and user management to your web, mobile and even IoT applications.
Amazon Cognito features consists of:
- Amazon Cognito User Pools: create and maintain a user directory in order to add sign-up and sign-in to your mobile app or web application. You can also sign in users to a user pool through social identity providers as well as, SAML-based providers
- Amazon Cognito Federated Identities: enables the creation of unique identities for users and the ability to authenticate them with federated identity providers, such as Google or Facebook, for temporary, limited-privilege access to app resources
- Amazon Cognito Sync: allows you to synchronize user profile data across mobile devices and the web without the need to build a backend. It supports offline access, cross-device synchronizing, and local data caching of application-related user data so the user app experience remains consistent regardless of the device.
With the General Availability of Amazon Cognito User Pools – App Integration and Federation, we are now adding AWS-hosted user sign-up and sign-in UI pages to help web and mobile app developers effortlessly integrate and customize the onboarding user experience for their applications. In addition, when using the Cognito User pools user directory, you can enhance your mobile client login capabilities by providing a sign-up and sign-in for social identity providers including Facebook, Google, Login with Amazon, as well as through SAML with corporate identity providers such as Microsoft Active Directory.
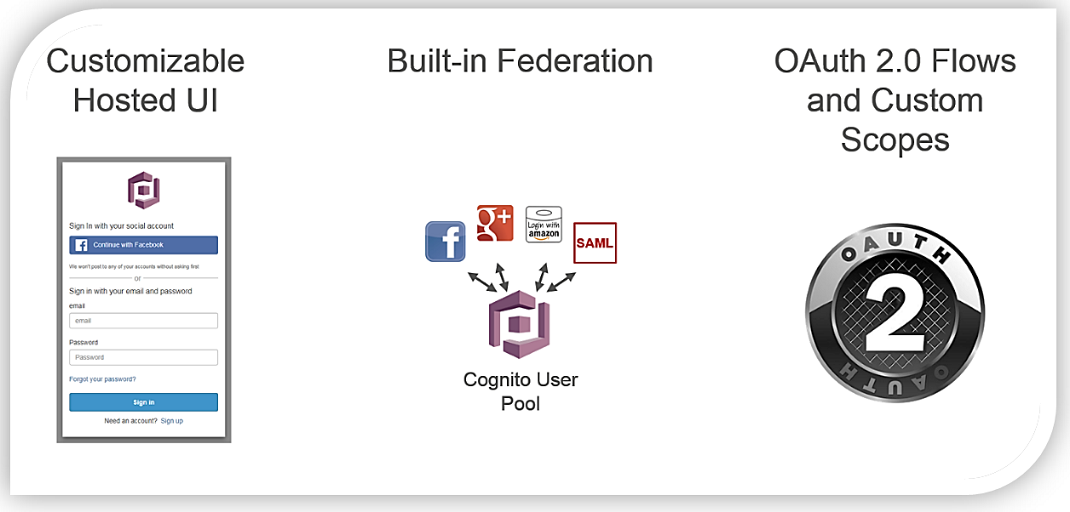
The aspects of the Amazon Cognito User Pools – App Integration and Federation service features provided in this GA release are as follows:
| App Integration with User Pools | |
| Provide a hosted UI for sign up, sign in, forgot password, etc. | Provide a New WebView for Mobile clients |
| Developers can customize the hosted UI to match their style and branding | Enables usage of Custom logo and CSS styles |
| Federation with User Pools | |
| Cognito handles interactions with identity providers to authenticate users and receive tokens | Identity providers are configured in Cognito Ex. SAML metadata document, issuer URL, identifiers, and domains |
| Cognito User Pools act as a universal directory providing user profiles and authentication tokens for federated and “Cognito service users | Supporting Identity Providers: SAML, Facebook, Google, and Amazon |
| OAuth 2.0 Support | |
| Cognito supports OAuth 2.0 as Industry standard protocol for authorization | OAuth 2.0 Permissions are defined as “scopes” Ex. permission to read a user profile or edit photos |
| Client apps can request a set of scopes, and if permitted, get back an access token with those scopes Ex. If the request is in the context of a user, the user can be authenticated | Client apps take the access token to a resource server to access the resources as permitted by the scopes |
Since I can’t wait to try out these new features, let’s build a quick app using the new Cognito User Pool App Integration and Federation features. Therefore, off to the Cognito management console we go. Once in the console, I’ll quickly create a User Pool for our test by clicking the Manage your User Pools button.

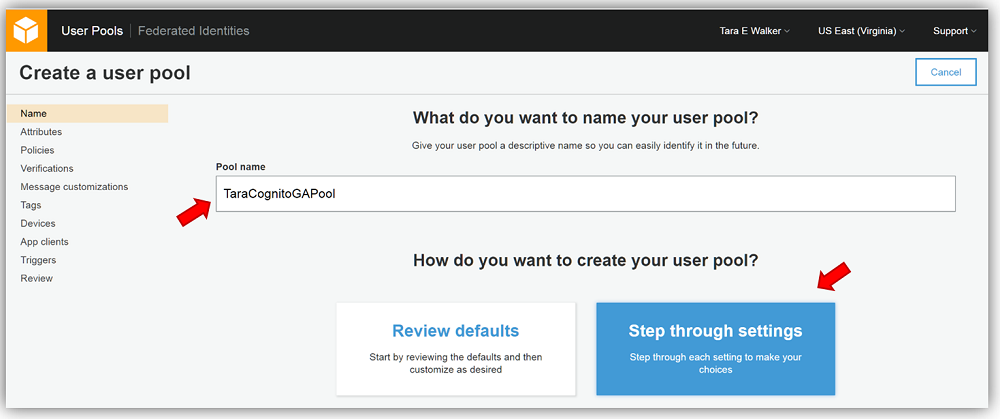
Once in the User Pools console, I’ll click the Create a user pool button. Once in the Create a user pool screen, I’ll name my new user pool, TaraCognitoGAPool, and since I want to customize my hosted UI and take advantage of the other new features, I opt for creating my pool by selecting the Step Through the Settings button to complete the creation of my user pool.
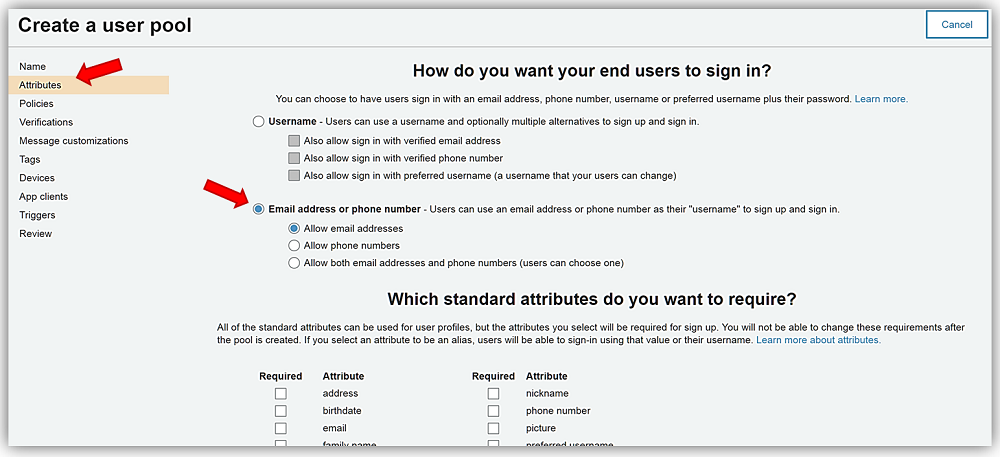
On the Attributes tab, I have two sign-in options for my users; they can sign in via Username and I can additionally grant the user multiple alternatives of how to log into my application. The other option is to allow the user to make use of their Email address or phone number to sign in and I can provide them the ability to use both options or ensure only one of the aforementioned methods are used. Usually, I opt for the user to use Username with email, but since we are testing out the new features of App Integration and Federation today, I am going to select Email address or phone number and only allow the use of email addresses for sign-in/sign-up.
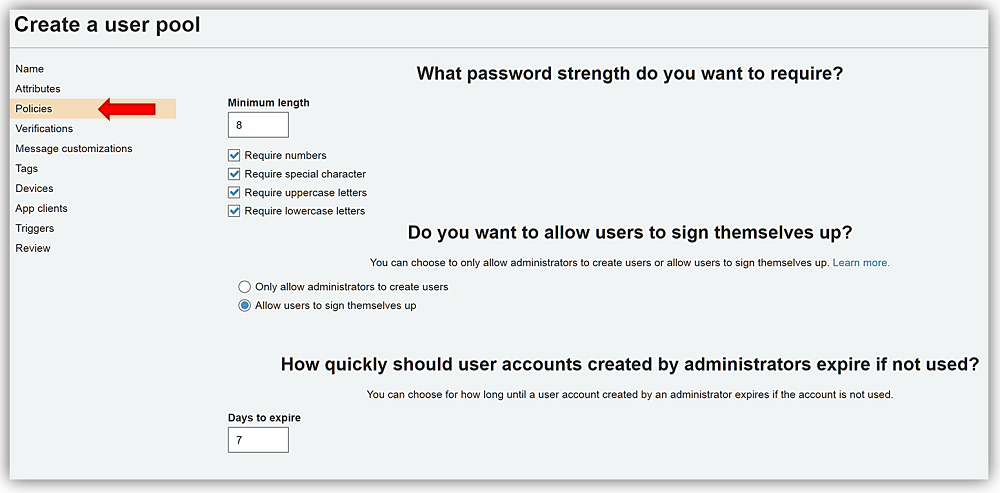
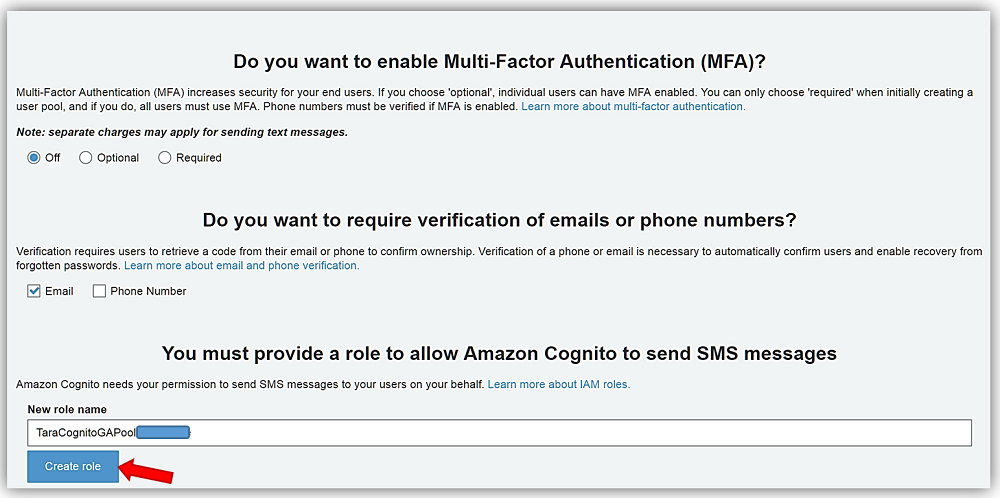
Next stop is the Policies and the Verifications tabs for which I will keep all of the default options selected on both of the tabs. On the Verification tab, however, I do want to provide the option for Cognito to send SMS messages on my behalf. Therefore, I will choose the Create Role button and allow an IAM role to be created granting SMS permissions. I complete the selection of options for my user pool options by clicking Save Changes button.
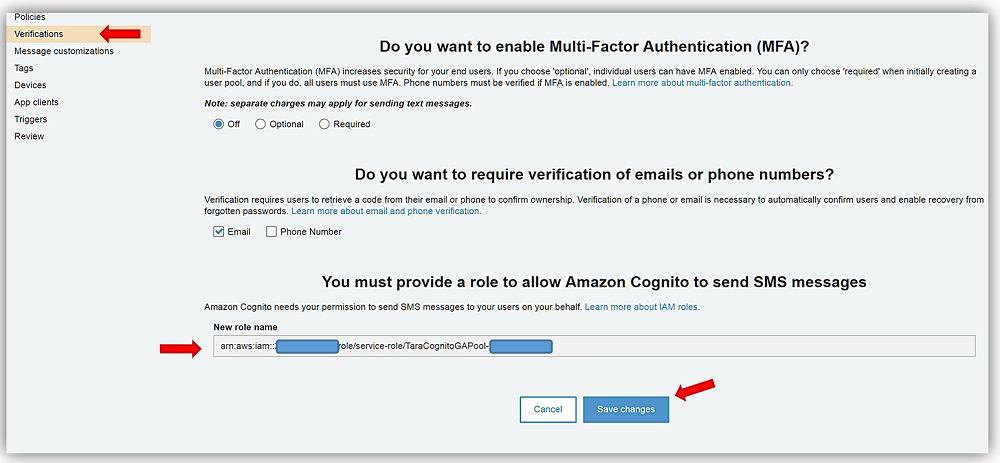
The last step is to go to the App clients tab and create an app client by clicking the Add an app client link on the page. I’ll name my app client, TaraCognitoGA-App, leave all the default options the same, and click the Create app client button.
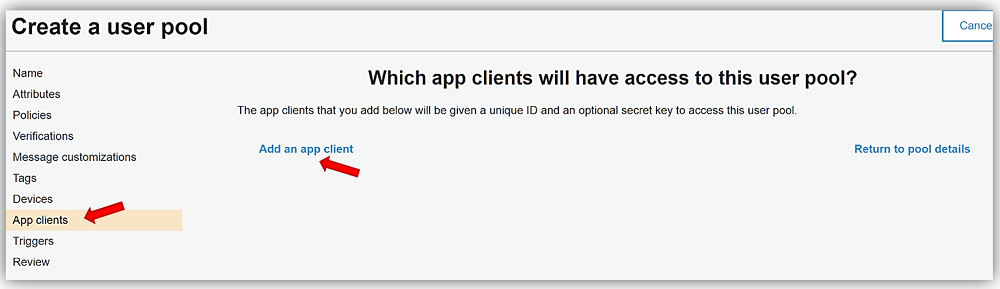
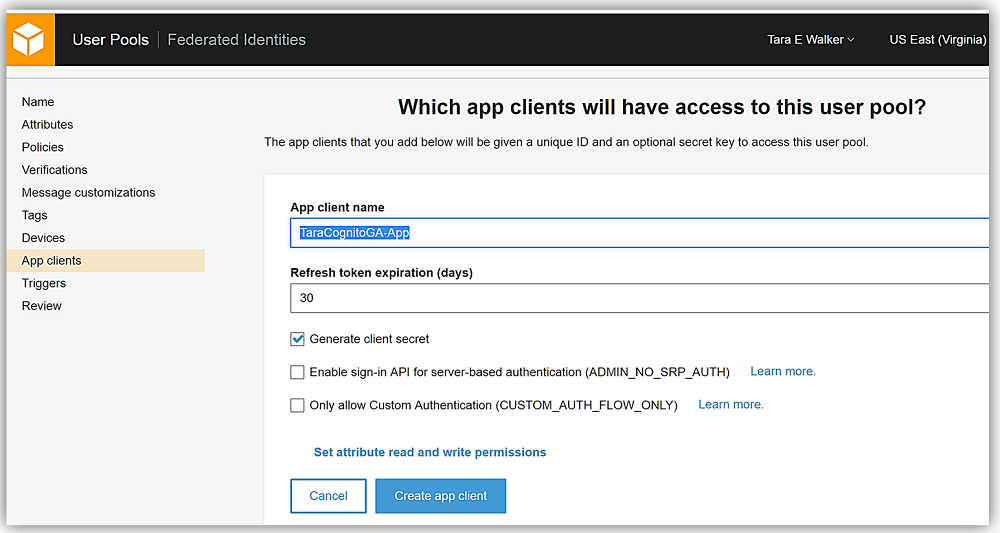
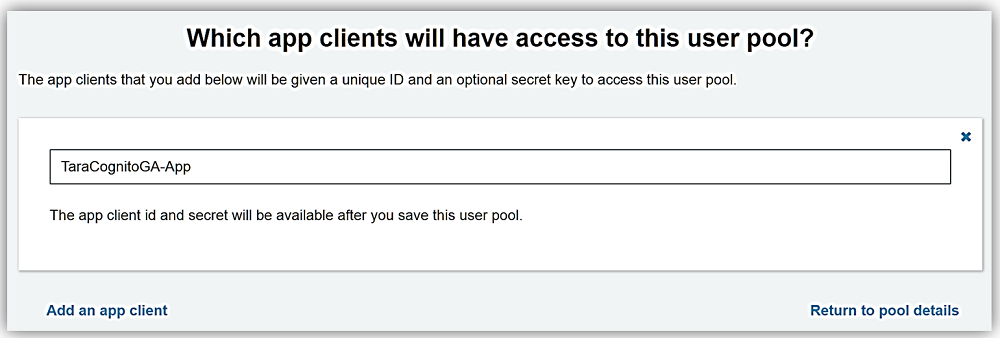
All that is left is to review the TaraCognitoGAPool options and click Create pool button.
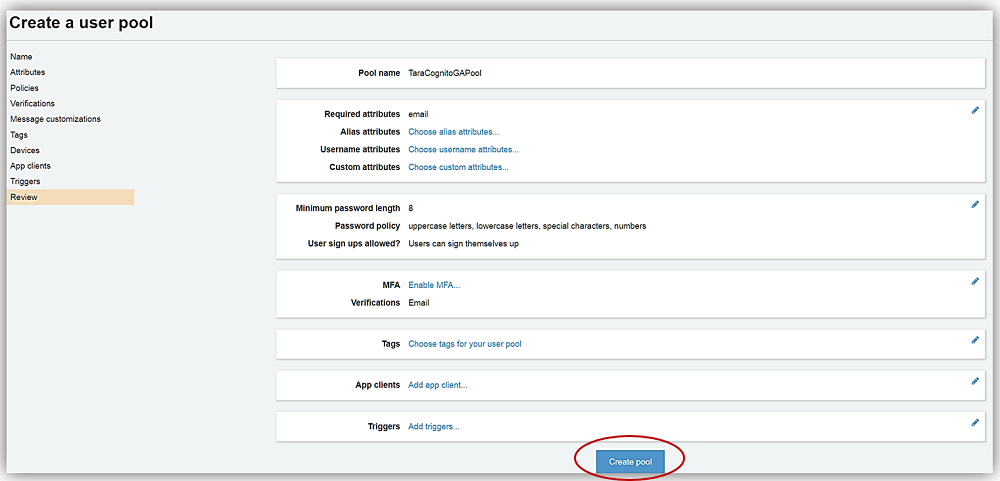
Great! Now that my user pool, TaraCognitoGAPool has been created. I can take advantage of the new App Integration and Federation features. If you have created a user pool before, you will notice that the user pool screen now contains tabs for the new user pools features in the menu side bar.
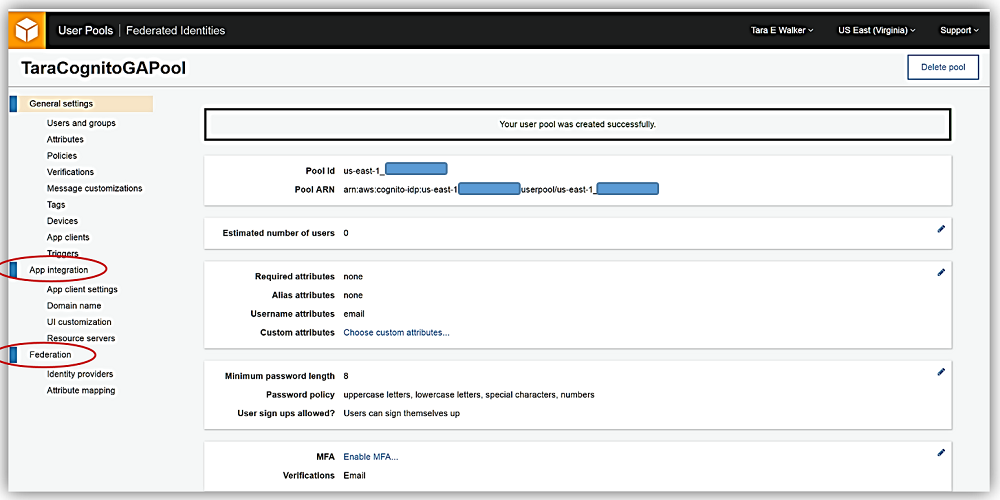
This is what we’ve been waiting for. Now I will go into App integration tab in order to configure settings to have my own customized, built-in UI for signing up and signing in users to my TaraCognitoGA-App.
First I’ll go into my App client settings under the App Integration tab. Here I will enable the identity providers I want to allow users of my application to use when signing in. Since I have only enabled Cognito User Pools as an identity provider, it is currently the only identity provider option. If I want to allow users to sign in with external identity providers like Facebook or a SAML provider I will have to configure them with Federation. We’ll discuss this shortly.
For now, I’ll enter the callback URL that my app should go to once the user has been successful in logging in, and the URL that the app should return to once the user has logged out. I’ve created a quick S3 website to use with my Cognito new sign-in. For more information on these options please see: Specifying Identity Provider Settings for Your User Pool App in the Cognito developer guide.
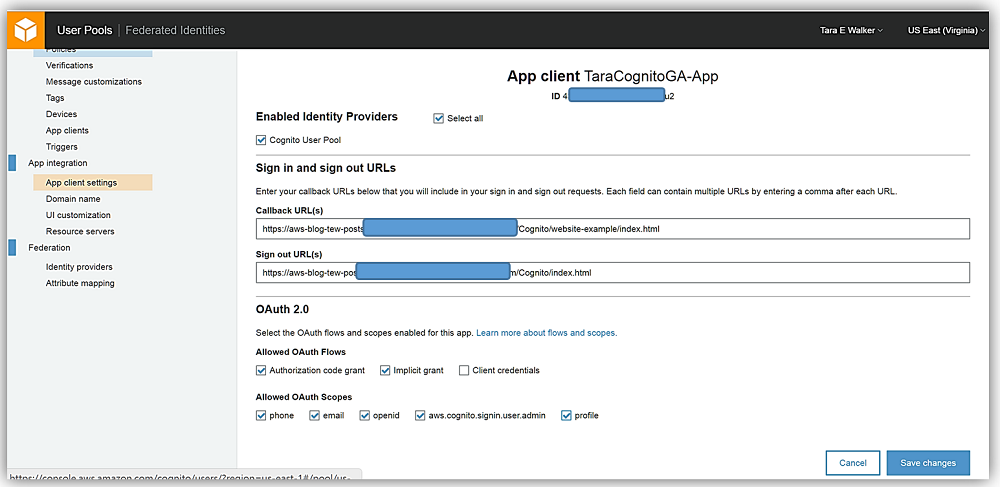
Now I’ll to go to the Domain name option under the App Integration tab, and I’ll enter a domain prefix to be used for my sign-up and sign-in pages hosted by Cognito. Keeping with my current naming convention, I’ll name my domain, taracognitodomain-ga, and click the Check Availability button. Remember your domain name must be unique across the chosen AWS region and can only contain lowercase letters, numbers, and hyphens. Since my domain name is available, I will click Save changes and go to UI customization settings.
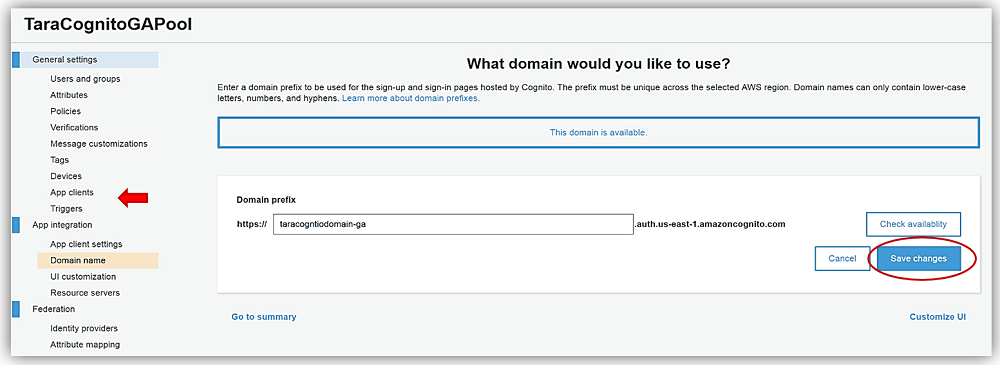
UI customization settings is where I can change the look and feel of the default AWS UI hosted sign-in for a specific app client or as the default look for all my app clients. I’ll select the app client I created earlier and upload my personal logo to be displayed on my page. You should note that you can customize the CSS for several fields and HTML tags for your page as well by selecting the options under the CSS customizations (optional) section and adding your CSS as desired.
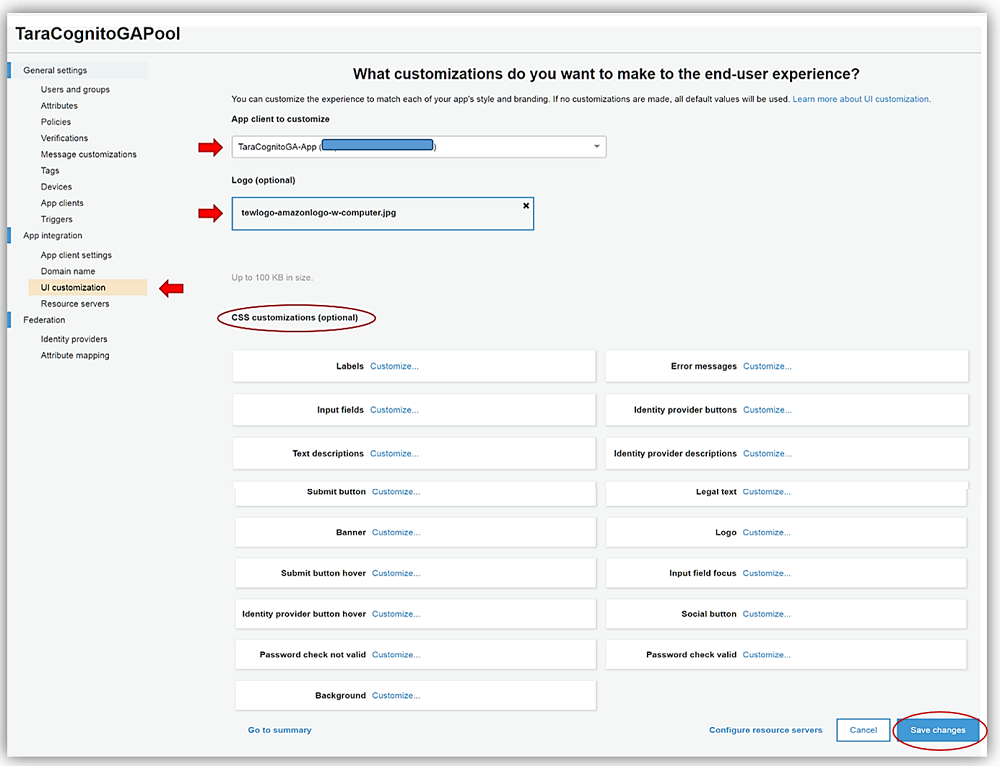
After selecting the Save Changes button, I can now view my login page, which I can use for by web and mobile app clients. The hosted UI for your Cognito User Pool can be accessed by using a URL with the following pattern:
Which would make my hosted URL as following (my client id is obfuscated):
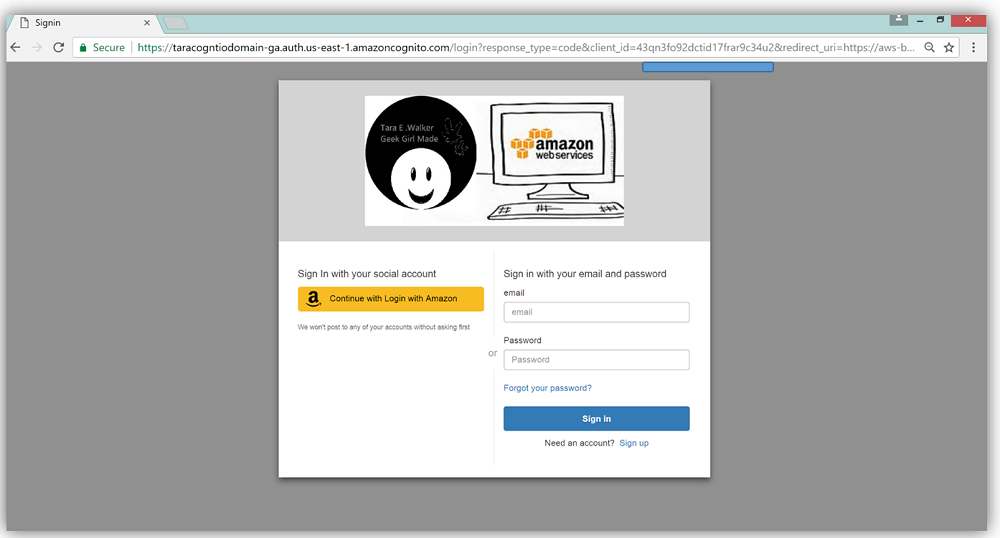
Clicking on this link displays my custom sign-in and sign-up page hosted by AWS Cognito User Pools with my custom logo presented. How exciting!
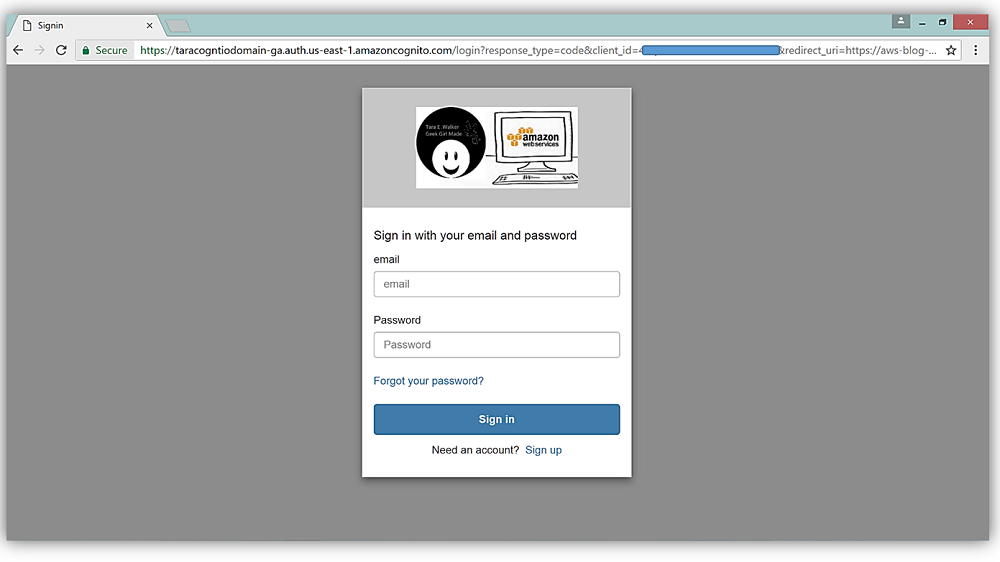
We’re cooking with gas! But wait, I promised that I would discuss how to tie Federation and external federated identity providers to your Cognito User Pool. I’m sure you thought that I had forgotten. No worries, I’ll discuss Federation now.
Configuring Federation with a social and/or a SAML identity provider is pretty easy. With Cognito’s built-in integrations, you no longer have to integrate multiple identity provider SDKs or handle redirects or post backs in your app. Cognito handles the identity provider interactions for you and creates user profiles for federated users in Cognito User Pools.
However, before I show you how to configure a Cognito Federated identity provider, I actually need one to show. Given this, I ran over to the Login with Amazon page and created an app so I can use it as one of my federated identity providers. Sure, I could have done Facebook or Google but everyone does those identity providers, and hey, we all need a little variety in our lives.
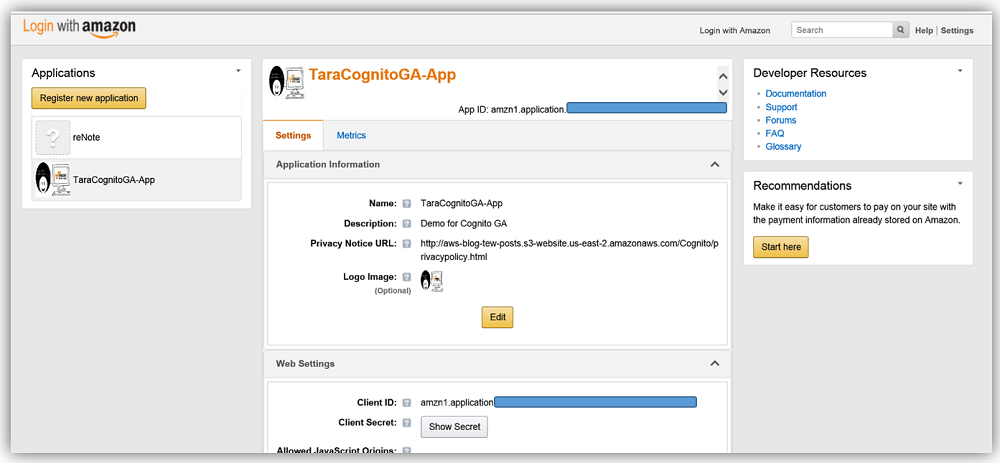
With my Login with Amazon app id and app secret in hand, I’ll return to the Cognito User Pool console and go to the Federation tab on the menu side bar. I’ll select the identity providers option, and here I am presented with all the identity providers supported for sign in with Cognito User Pools. Here I will select the Login with Amazon identity provider.
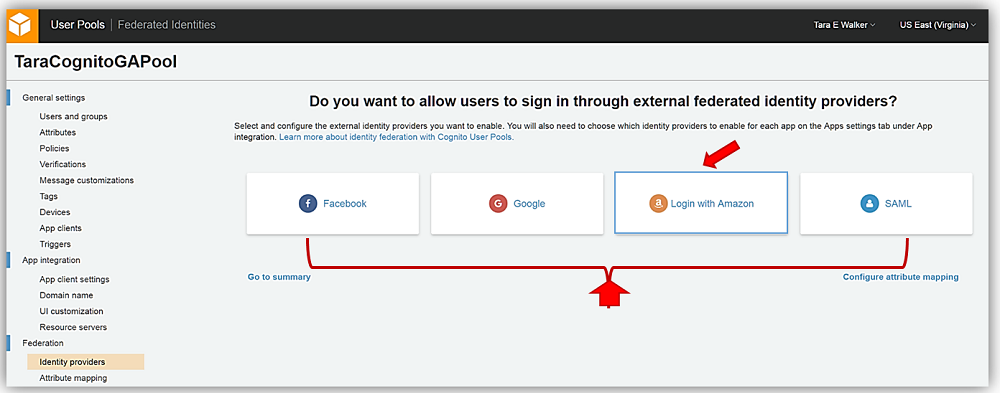
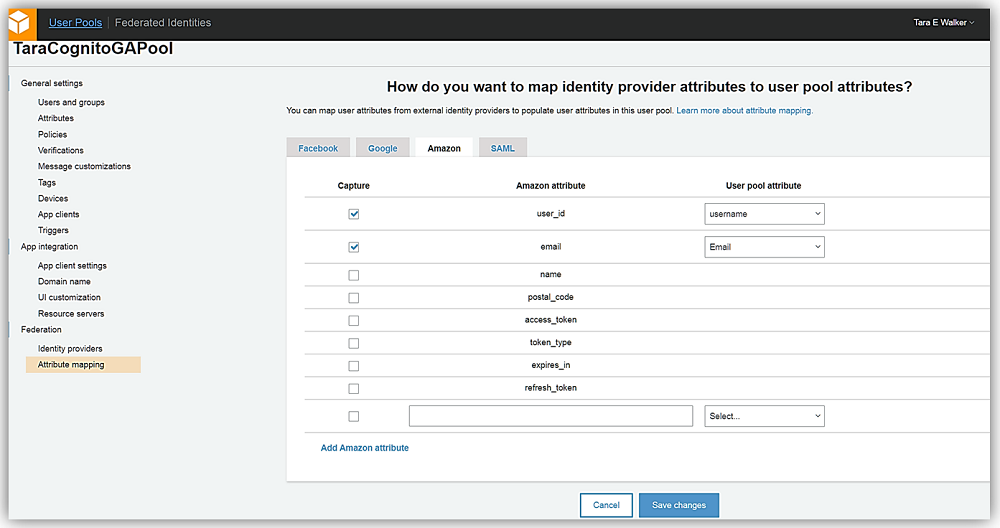
Now I will enter my app ID/client ID and app secret provided by the Login with Amazon service into the Amazon app ID and App secret fields. I also can determine what scopes and related data are authorized by this login. For this sample, I have chosen to enter profile, postal_code, and email in the Authorize scope field.
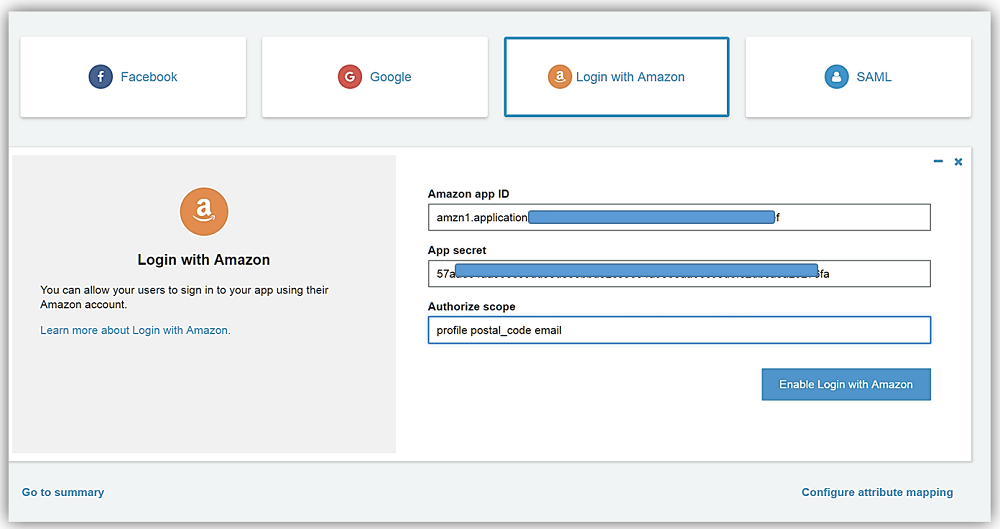
All that is left is for me to select the Enable Login with Amazon button, and I have successfully added the identity provider for the Login with Amazon identity service.
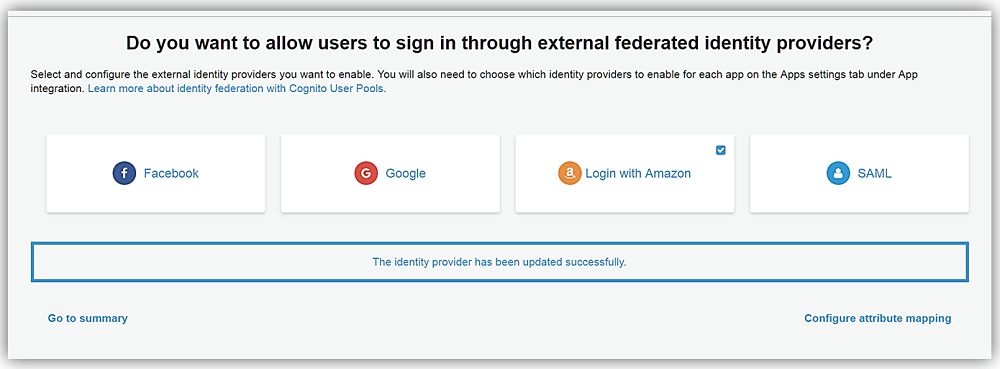
My final step is to go to the Attribute mapping section also under the Federation section. Here I will select the Amazon tab and map the Login with Amazon attributes to the attributes captured by Cognito User Pool. Once I hit that Save changes button, I have successfully added the Login with Amazon identity provider.
If I go back to App client settings and enable Login with Amazon provider by checking the provider related check box, and return to my Cognito UI hosted login page; I now see that Cognito has successfully added the Login with Amazon to my sign in page.
Summary
Fantastic! Now as a developer, I can focus on making my app experience as smooth and engaging as possible, including a simple, customized sign in process for my app users without the heavy lifting typically needed to implement a sign in screen with social and SAML identity providers.
AWS Cognito User Pools – App Integration and Federation enables web and mobile app developers to easily integrate and customize a user experience for users to sign-up and sign-in though AWS-hosted web pages. Additionally, it simplifies user management by providing a unified user authentication and authorization mechanism whether using Cognito User Pools as a user directory and/or other identity providers including Facebook, Google, Login with Amazon, as well as, corporate SAML providers like Microsoft Active Directory. Learn more about this great service by checking out the Amazon Cognito product page or the Amazon Cognito developer guide.
Enjoy!
– Tara