AWS News Blog
CloudFront Update – HTTPS & TLS v1.1/v1.2 to the Origin, Add/Modify Headers
Amazon CloudFront can be used to deliver static and dynamic content using a global network of edge locations. You can set it up in minutes and give your customers the benefit of fast, low-latency access to your web site, movies, music, and so forth.
Each CloudFront distribution references one or more origins (web servers or S3 buckets). When CloudFront needs content that is not cached at an edge location, it makes a request to the appropriate origin, as determined by a set of mappings (behaviors) that are also specified within the distribution.
Today we are launching three new features that will give you additional control over the connection between CloudFront and your origins:
- Support for TLS v1.1 and v1.2
- HTTPS-only connection
- Control of edge-to-origin request headers
Support for TLS v1.1 and v1.2
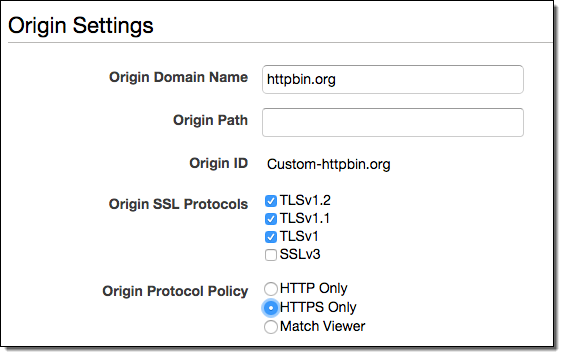
We have added TLS v1.1 and TLS v1.2 to the list of protocols that you can configure between the edge and a custom origin. With this change, you can now configure CloudFront to use SSLv3, TLS v1.0, v1.1, and v1.2 for each custom origin you set up for a CloudFront distribution.
HTTPS-Only Connection
You can now configure CloudFront to always use HTTPS while connecting to your origin, regardless of the protocol (HTTP or HTTPS) that was used to connect to the edge. Previously, CloudFront connected to the origin using the same protocol (HTTP or HTTPS) that was used to connect to the edge. When you enable this new feature, both HTTP and HTTPS requests from the viewer will be sent to the origin using HTTPS.
Here is how you configure the desired protocols and HTTP-Only for a custom origin:
Control of Edge-to-Origin Request Headers
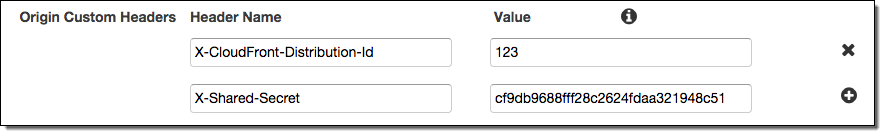
You can now configure CloudFront to add custom headers or override the value of existing request headers when CloudFront forwards requests to your origin. You can use these headers to help validate that requests made to your origin were sent from CloudFront (shared secret) and configure your origin to only allow requests that contain the custom header values that you specify.
For Cross-Origin Request Sharing (CORS), you can configure CloudFront to always supply the applicable headers to your origin to accommodate viewers that don’t automatically include those headers in requests. This also allows you to disable varying on the Origin header, which increases your cache hit ratio.
Here’s how you would add new headers named X-CloudFront-Distribution-Id and X-Shared-Secret:
These features are available now and you can start using them today at no additional cost. To learn more, read the CloudFront Developer Guide.
— Jeff;