- AWS Solutions Library›
- Guidance for Connected Vehicles on AWS
Guidance for Connected Vehicles on AWS
Use real-time connected vehicle updates to transform vehicle support and roadside assistance
Overview
This Guidance helps you modernize your broker to gather, collect, and distribute data with your connected vehicle workloads using AWS IoT Core and Message Queuing Telemetry Transport (MQTT) 5. Most connected vehicle workloads require the vehicle to be connected to a cellular connection; otherwise, the vehicle would lack connectivity to receive commands from the cloud. With AWS IoT Core and the MQTT protocol, original equipment manufacturers (OEMs) can scale connected vehicles to meet demands during peak usage and right-size their workloads.
This Guidance is composed of five architecture diagrams that address the following using Internet of Things (IoT) services: modernizing connected vehicle workloads, gathering and processing vehicle data, setting up operational certificate lifecycles, encryption and monitoring security, and connecting a companion application.
How it works
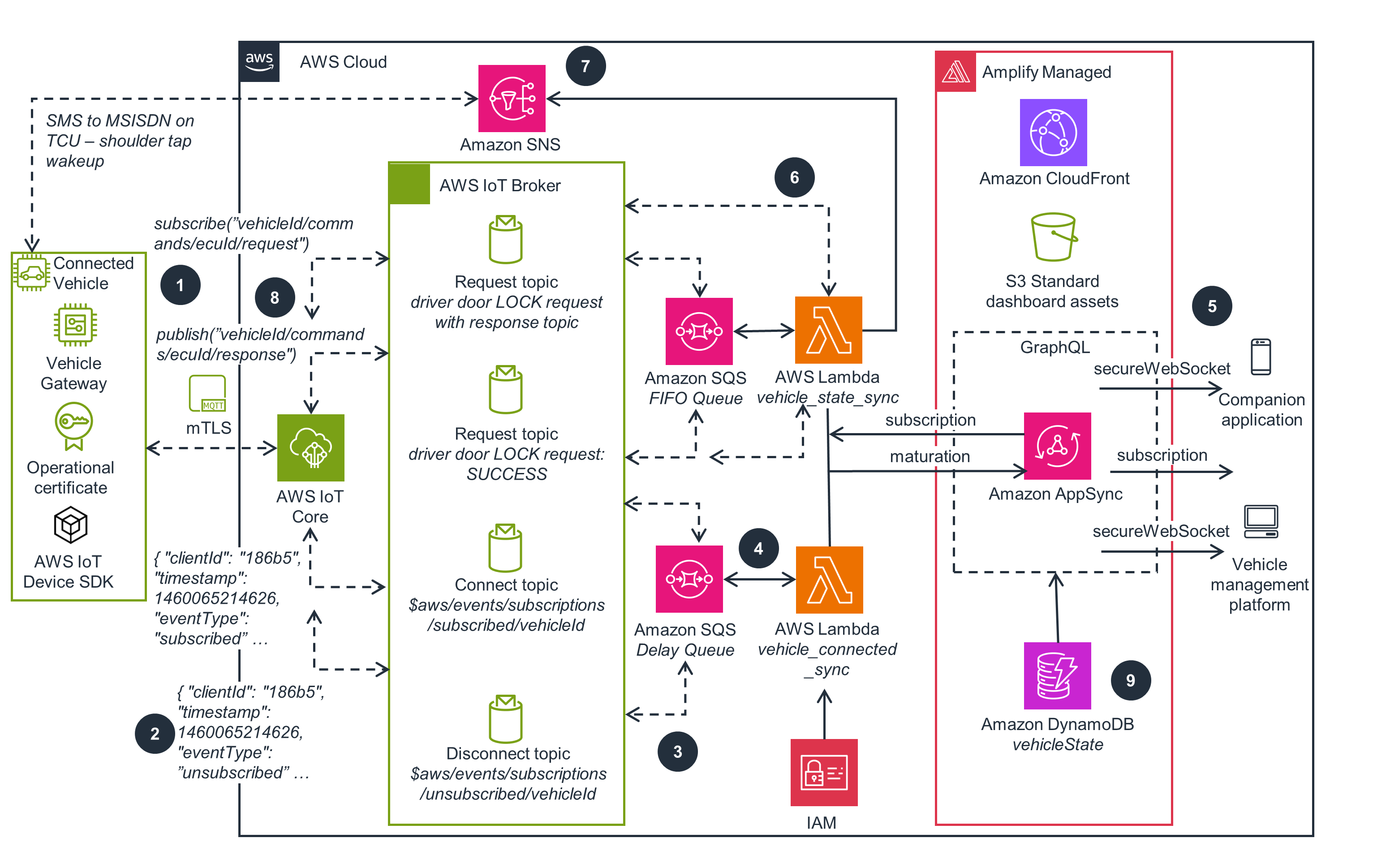
Modernized Connected Vehicles
This architecture diagram shows you how to modernize your connected vehicle workloads.
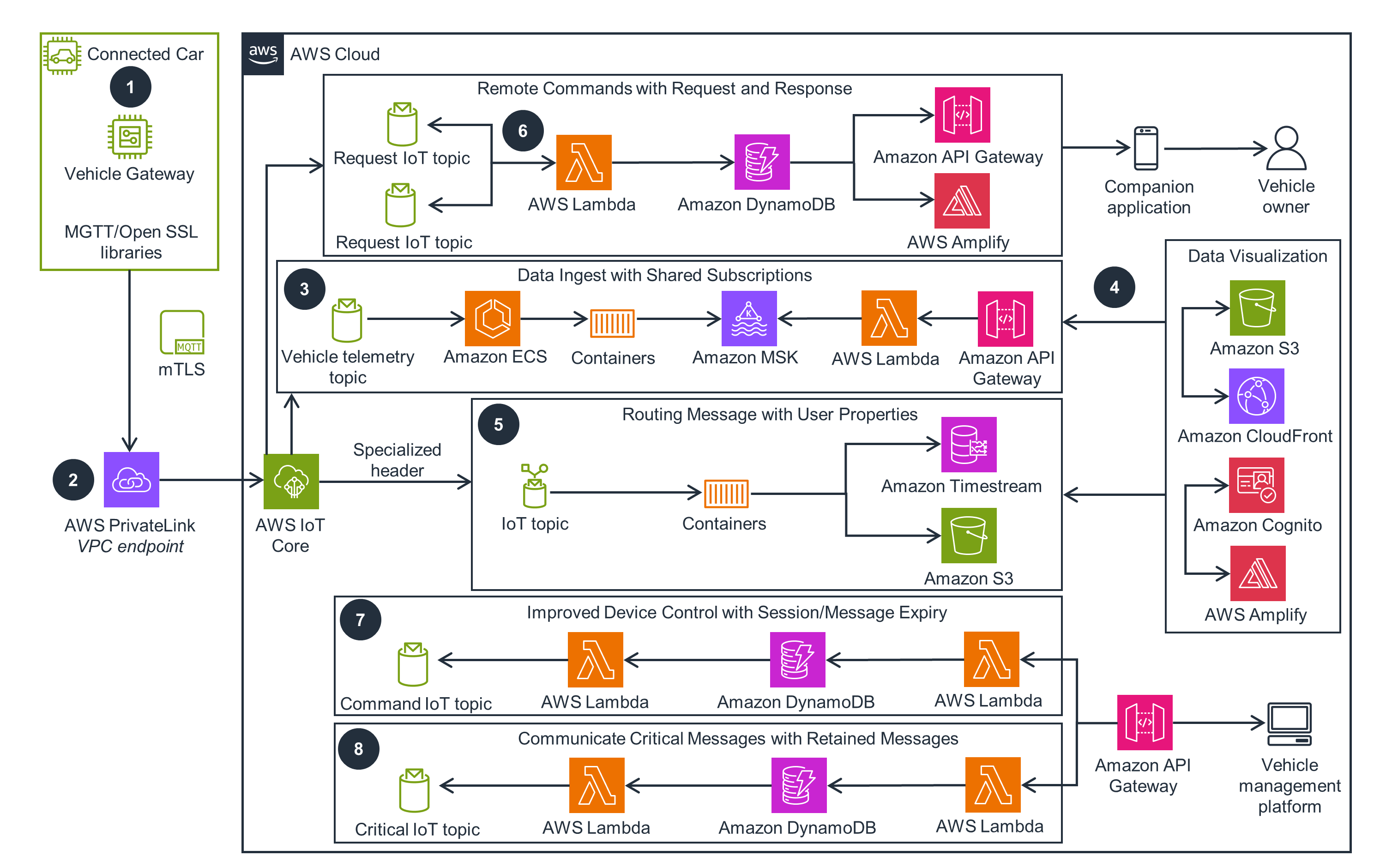
Data Gathering and Processing
This architecture diagram shows you how to gather, process, analyze, and act on connected vehicle data.
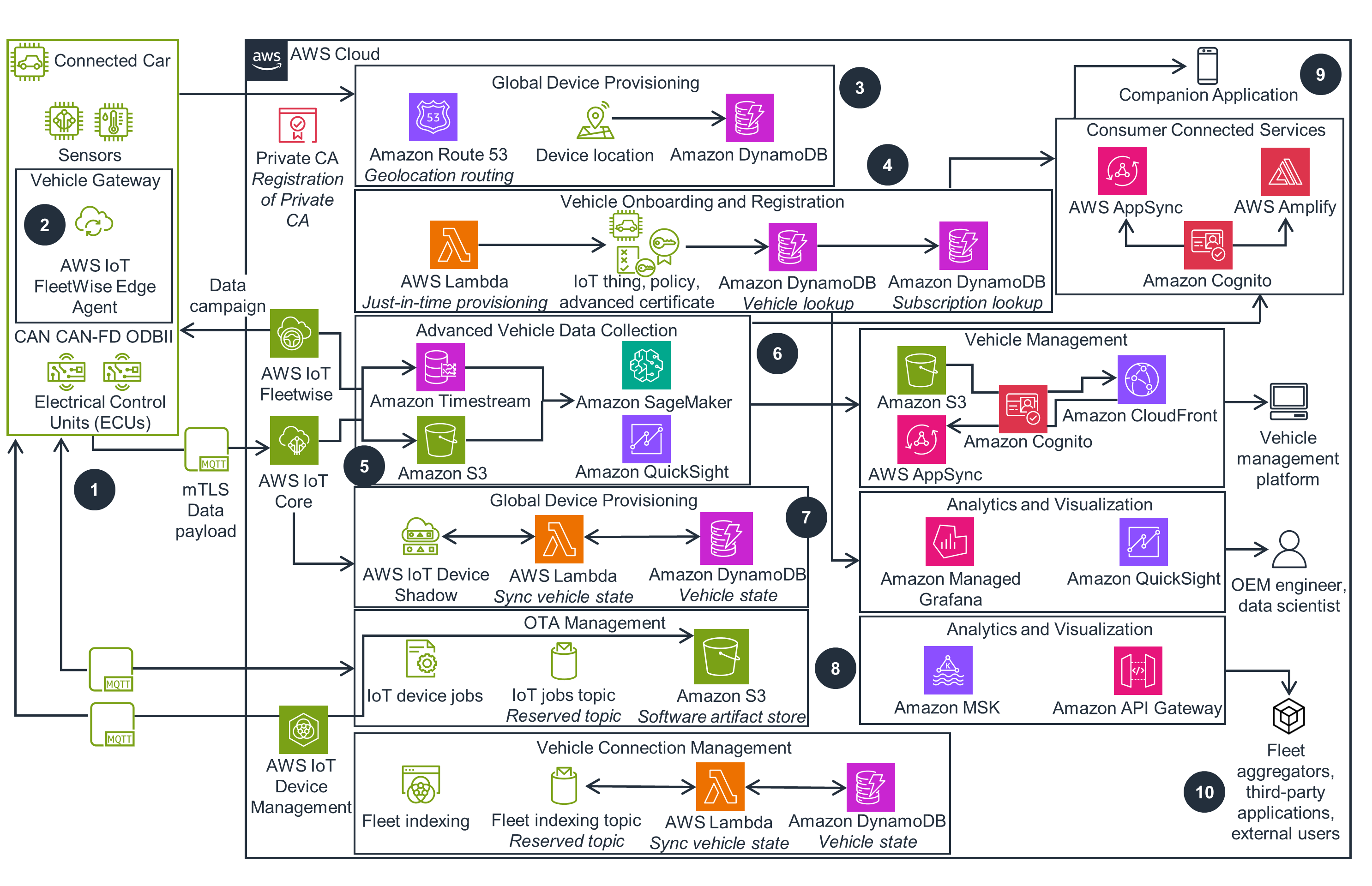
Operational Certificate Lifecycle
This architecture diagram shows an operational certificate lifecycle.
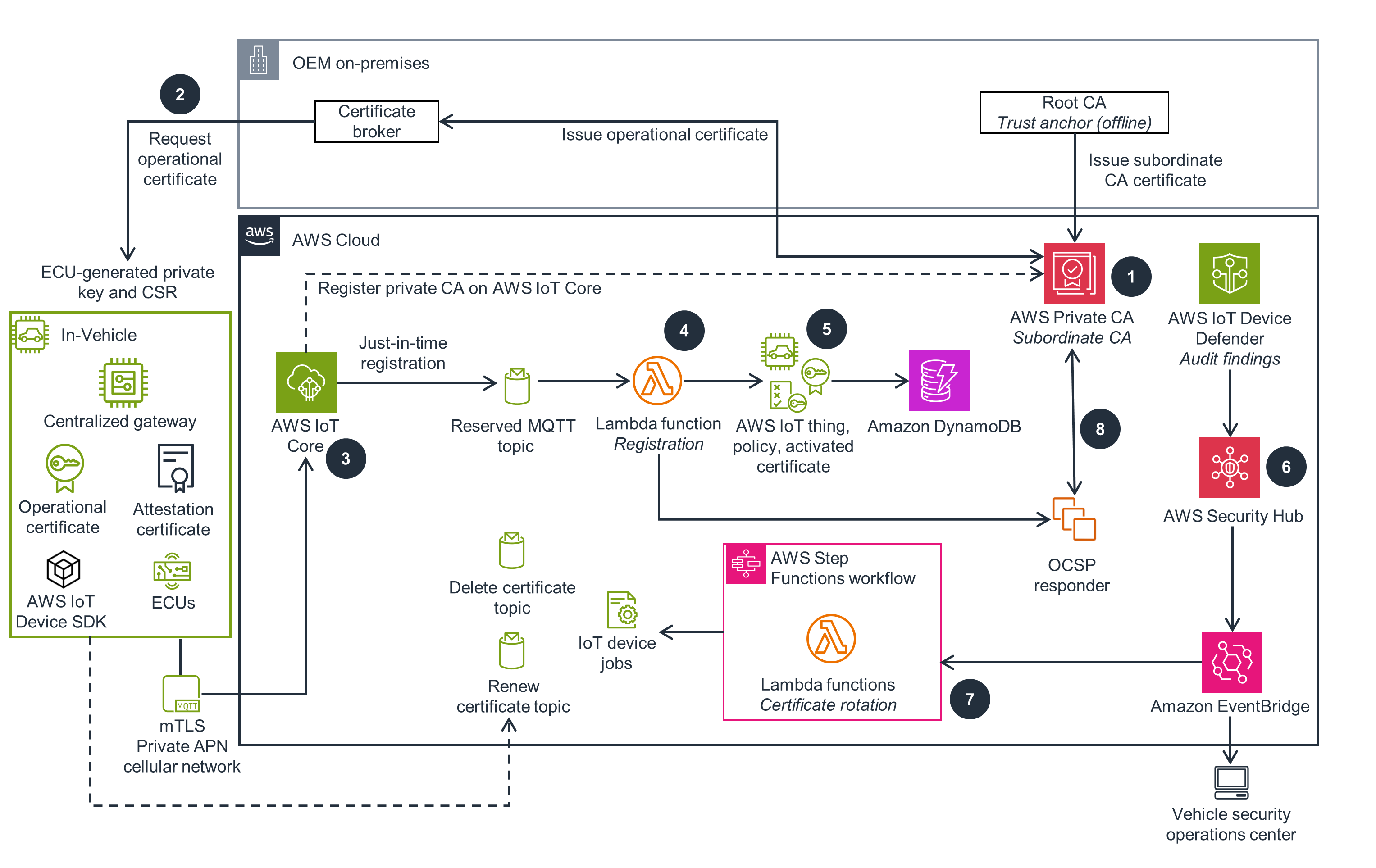
Encryption and Monitoring Security
This architecture diagram shows you how to secure connected vehicles through encryption and monitoring.
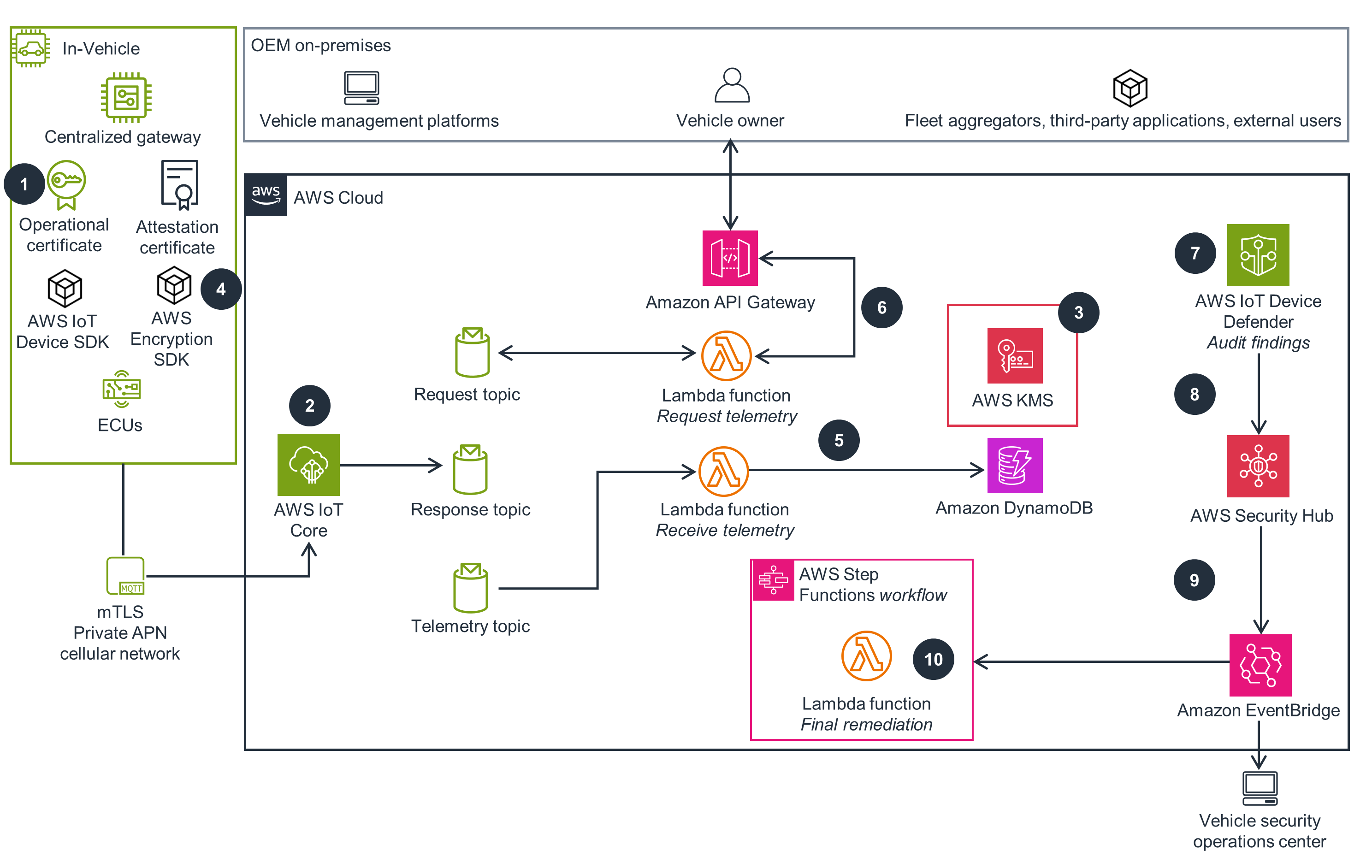
Companion Application
This architecture diagram shows you how to build a connected vehicle companion application.
Well-Architected Pillars
The architecture diagram above is an example of a Solution created with Well-Architected best practices in mind. To be fully Well-Architected, you should follow as many Well-Architected best practices as possible.
In this Guidance, we chose AWS IoT Core, Amazon ECS, DynamoDB, AWS IoT Device Management, AWS KMS, Amazon Cognito, API Gateway, and AWS IoT Device Defender to support operational excellence, because these services collectively address key challenges in connected vehicle and IoT systems. They optimize data transfer, processing, and storage, help ensure data security, and proactively manage device health and security. For example, AWS IoT Device Defender proactively identifies and mitigates security threats.
AWS IoT Core provides secure communication and authentication for IoT devices, preventing unauthorized access. AWS Private CA manages certificates for device authentication, so only trusted devices can connect. AWS KMS manages encryption keys for data in transit and at rest, protecting sensitive information from unauthorized access. Amazon Cognito manages user access and authentication for secure and controlled access to vehicle-related data and functionalities. AWS IoT Device Defender monitors device behavior for security threats, proactively identifying and mitigating abnormal activities and reducing the risk of security breaches.
By using these services, you can mitigate security risks, protect sensitive data, and maintain the integrity and confidentiality of information, which is crucial for building trust and helping ensure compliance in IoT deployments.
The services in this Guidance help you reduce the risk of system failures, downtime, and data loss, ultimately enhancing user satisfaction and operational efficiency in their IoT deployments. AWS IoT Core helps ensure reliable and secure data transfer between devices and the cloud, reducing the risk of data loss or communication failures. Amazon ECS provides scalability to handle varying workloads, preventing performance bottlenecks and ensuring consistent system performance. AWS IoT Device Management enables OTA device management, reducing downtime by allowing remote updates and configuration changes. AWS IoT Device Defender monitors device behavior and security, proactively identifying and mitigating issues that could impact device reliability and system performance.
AWS IoT Device Management enables OTA device management, allowing for remote updates and configuration changes without disrupting device performance. OTA updates through AWS IoT Device Management reduce the need for manual interventions and system downtime, allowing devices to maintain peak performance while staying up-to-date. AWS IoT Core offers features such as shared subscriptions, topic aliasing, and payload size reduction, which optimize data transfer and reduce latency, enhancing overall system performance and contributing to faster data processing.
Additionally, Amazon ECS provides scalability and efficient resource allocation for processing telemetry data so that system performance remains optimal, even during periods of high data processing.
Amazon ECS provides scalability to efficiently handle varying workloads, optimize resource usage, and reduce infrastructure costs. By facilitating OTA updates, AWS IoT Device Management reduces the need for expensive physical interventions and recalls, saving time and resources. AWS IoT Core optimizes data transfer and communication, reducing data transmission costs and improving overall efficiency, which directly contributes to cost savings. These services can help you strike a balance between maintaining high-quality services and controlling costs, leading to more efficient and cost-effective IoT operations.
AWS IoT services in this Guidance reduce the need for on-premises infrastructure and its associated energy consumption. AWS IoT services also enable efficient data processing and transmission that can lead to energy savings, support OTA updates that reduce the need for physical recalls or manual updates, and incorporate monitoring and analytics tools that identify inefficiencies and anomalies. This helps you optimize resource utilization and reduce environmental impact.
Disclaimer
Did you find what you were looking for today?
Let us know so we can improve the quality of the content on our pages