AWS News Blog
Enable Single Sign On to the AWS Management Console
AWS Identity and Access Management (IAM) enables you to create and manage IAM users and manage access to your AWS account. Some customers have told us that they prefer leveraging their existing corporate identities to access AWS services and resources via identity federation. Today, were making it even easier for you to get started with federation to AWS using a new pre-packaged sample application.
The sample illustrates how customers using Windows Active Directory (AD) can easily configure Single Sign-On (SSO) to the AWS Management Console. Implementing SSO means that your users no longer have to remember yet another password and that you dont have to manage users and passwords within both AD and AWS. The sample includes a setup wizard to help you get up and running in minutes to try out federation to AWS and includes everything required for you to enable your users to Single Sign-On to the AWS Management Console.
Heres How It Works
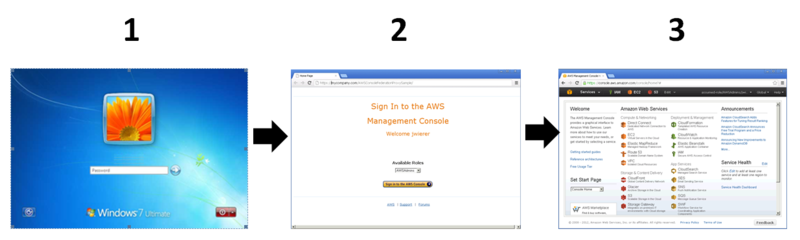
Here’s the basic flow of an AD user who wants to access the AWS Management Console:
- User signs on to the corporate network with their AD credentials. The sample creates an internal website that hosts a proxy server. A user browses to that website. The site authenticates the user against AD and displays a set of IAM roles that are determined by the users AD group membership.
- The user selects the desired role and clicks on Sign in to AWS Management Console. Behind the scenes, the proxy calls the AWS Security Token Service (STS) to assume the selected role. The response includes temporary security credentials. Using these credentials, the federation proxy constructs a temporary sign-in URL.
- User is redirected to the temporary sign-in URL and is automatically signed in to the AWS Management Console, without being prompted for another username and password. The user is limited to the privileges defined in the role they selected.
By default, the console session will expire after one hour and the console will be inaccessible. This helps protect your AWS account in the case where users mistakenly leave their computers unlocked while signed in to the console. When the session expires the user will be redirected to a page that includes a URL to the site that hosts the federation proxy. Clicking the URL will re-direct the user to the site that hosts the federation proxy so they can re-authenticate.
For additional information and a link to download the sample, please visit the AWS Management Console Federation Proxy Sample download page or attend Jeff Wierer’s talk “SEC302: Delegating Access to Your AWS Environment” at AWS re: Invent on Nov 28th – Wednesday 3:25 PM (Venetian, Room 3401A)
– Jinesh;