AWS News Blog
Elastic Load Balancer SSL Support Options
We’ve added some additional flexibility to Amazon EC2’s Elastic Load Balancing feature:
- You can now terminate SSL sessions at the load balancer and then re-encrypt them before they are sent to the back-end EC2 instances.
- You can now configure the set of ciphers and SSL protocols accepted by the load balancer.
- You can now configure HTTPS health checks.
Terminate and Re-Encrypt
The Elastic Load Balancer has supported SSL for a while. Here’s the original model:
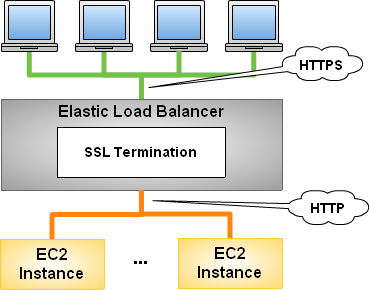
We’re enhancing this feature to allow you to terminate a request at the load balancer and then re-encrypt it before it is sent to an EC2 instance:
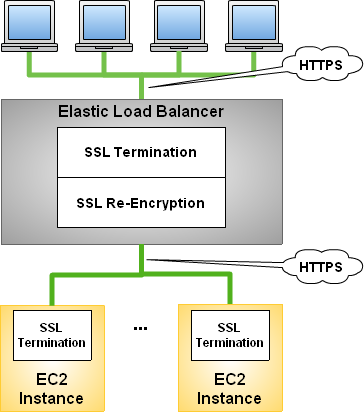
This provides additional protection for your data, a must for PCI compliance, among other scenarios. As a bonus feature, the Elastic Load Balancer can now verify the authenticity of the EC2 server before sending the request. By allowing the ELB to handle the termination and re-encryption, developers can now take advantage of features like session affinity (sticky sessions) while still using HTTPS.
You can set this up from the AWS Management Console, the Command Line tools, or the Elastic Load Balancer APIs.
Configurable Ciphers
You may not know it, but SSL can use a variety of different algorithms (also known as ciphers) to encrypt and decrypt requests and responses. The algorithms vary in the level of protection that they offer and in the computational load required to do the work.
Developers have told us that they need additional control over the set of ciphers used by their Load Balancers. In some cases they need to support archaic clients using equally archaic ciphers. More commonly, they want to use only the most recent ciphers as part of a compliance effort. For example, they might want to stick with 256 bit AES, a cipher that the US Government has approved for the protection of top secret information.
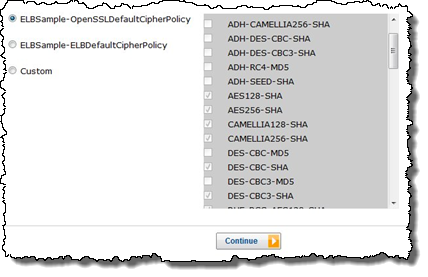
You can now control the set of ciphers that each of your Load Balancers presents to its clients. You can do this using the command-line tools, the APIs, or the AWS Management Console:
HTTPS Health Checks
You can (and definitely should) configure your Load Balancers to perform periodic health checks on the EC2 instances under their purview. Up until now these health checks had to be done via HTTP. As of this release, you can now configure HTTPS health checks. This means that you can configure your instances such that they respond only to requests on port 443.
Keep Going
Read more about these new features in the Elastic Load Balancing Developer Guide.
We’re Hiring
We have the following jobs open on the ELB team:
- Senior Software Development Engineer – AWS Elastic Load Balancing
- System Administrator / Engineer- Amazon Elastic Compute Cloud
— Jeff;