AWS News Blog
Identity and Access Management for the AWS Marketplace
AWS Marketplace now supports role-based permissions and management via AWS Identity and Access Management.
Let’s review the key terms before diving in to the details:
- AWS Marketplace makes it easy to find, buy, and 1-click deploy software to the cloud, featuring hundreds of popular commercial and open-source software products for developers, IT admins, and business users.
- AWS Identity and Access Management (IAM) offers greater security, flexibility, and control when using AWS. For larger businesses, IAM enables identity federation between your corporate directory and AWS services.
What is Subscribing?
AWS Marketplace lets you browse through more than 25 categories of software, including the most popular developer tools; operating systems, application infrastructure, and middleware; and business applications. When you find software that you want to use, you “subscribe” to the software. AWS Marketplace then creates EC2 instances to run the software.
EC2 instances can be launched either immediately, as part of the subscription process, or later (e.g. during the development cycle). The software is delivered as an AMI, so when youre ready to create an EC2 image with the AMI, you can do so through the Marketplace UI, or alternatively through the same EC2 API or command line statements that you use for any other AMI. Once youve subscribed to software, the Marketplace AMI looks to you just like any of your other AMIs.
As the AWS account owner, you now have fine-grained control over usage and software costs. Roles and permissions are created and managed through IAM, making it easy to get started, and easy to add controls for AWS Marketplace to new or existing IAM groups. You can now use Marketplace permissions to control access to Marketplace and to the EC2 instances that it launches, based on a user’s role in the business. For example you can set up your account so that:
- Managers and employees of the Finance Department can manage subscriptions but can’t run or terminate EC2 instances.
- Developers and IT personnel can inspect, run, and terminate EC2 instances, but cannot subscribe to applications.
Marketplace actions are now controlled by IAM permissions.
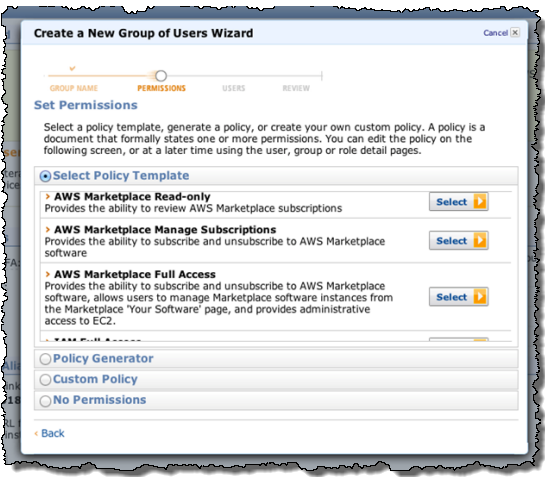
With the new IAM integration, we are providing three pre-made templates (these can be fully customized or changed, just like any other IAM template):
The permissons in the View Subscribed Software template are generally designed for administrators, staff concerned with technical standards, or anyone else interested in understanding usage and adoption of software, but who don’t need to actually create or manage particular instances of software.
The Manage Subscriptions permissions let a user subscribe to software, but not start or manage particular EC2 that run the software. This is useful for technical standards, procurement, or admin staff who want to enable or approve software for use inside an organization, but who do not need to create particular instances of the software.
Finally, the permissions in the Full Control template combines the permissions from the previous templates while adding in administrative EC2 permission, thereby enabling a user to subscribe to new software, as well as create and manage EC2 images running that software.
Our goal with these templates is to make it very easy for a company to get started with AWS Marketplace without the worries of losing control over software costs or usage. For organizations that have a strong procurement and standards function, the Manage Subscriptions and Manage EC2 roles make it easy to support workflows and use cases where approving software for use is a separate responsibility from actual implementation. However, for more decentralized organizations, the Full Control permission duplicates the existing Marketplace experience, letting a single user find, buy, and deploy software in a matter of minutes. Meanwhile, the View Subscribed Software role can be used to oversee and audit usage.
Here’s a walkthrough so that you can see how these features work together.
First, some new IAM users are created:
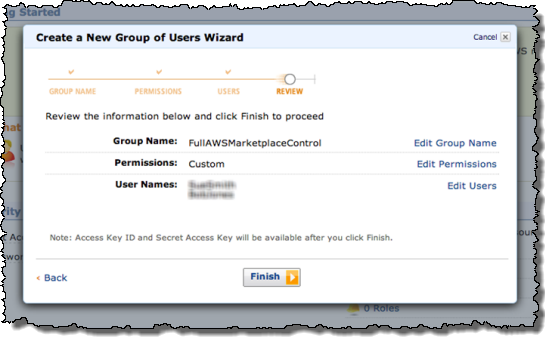
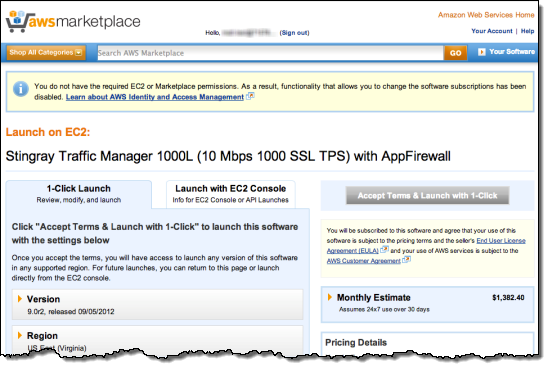
One of the users tries to launch an application in the AWS Marketplace. They are informed (via the message in the yellow box) that they do not have permission to do so:
They are then given the appropriate permissions via an IAM policy:
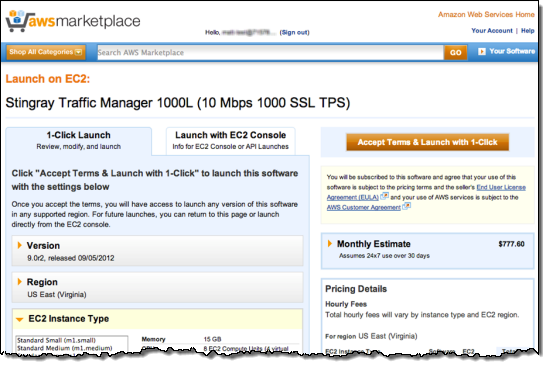
The users can log into AWS Marketplace using the IAM user name that theyve been given. Then can then make changes to subscriptions in AWS Marketplace:
— Jeff;
PS – We’ve been adding new applications to the AWS Marketplace every week; check it out if you have yet to visit.