AWS News Blog
Amazon Inspector – Automated Security Assessment Service
As systems, configurations, and applications become more and more complex, detecting potential security and compliance issues can be challenging. Agile development methodologies can shorten the time between “code complete” and “code tested and deployed,” but can occasionally allow vulnerabilities to be introduced by accident and overlooked during testing. Also, many organizations do not have enough security personnel on staff to perform time-consuming manual checks on individual servers and other resources.
New Amazon Inspector
Today we are announcing a preview of the new Amazon Inspector. As the name implies, it analyzes the behavior of the applications that you run in AWS and helps you to identify potential security issues.
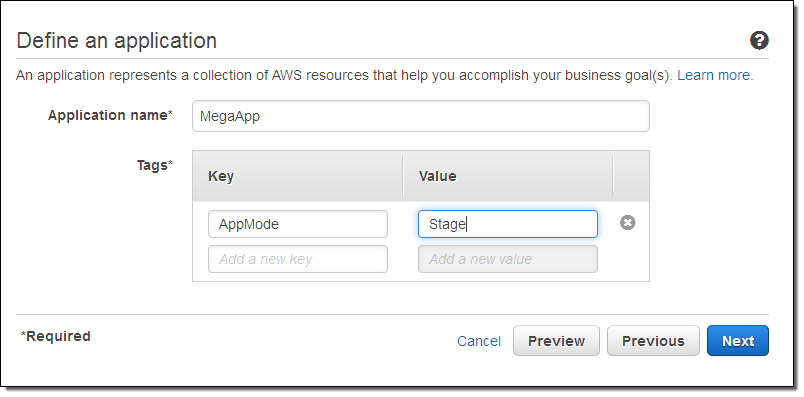
Inspector works on an application-by-application basis. You start by defining a collection of AWS resources that make up your application:
Then you create and run a security assessment of the application:
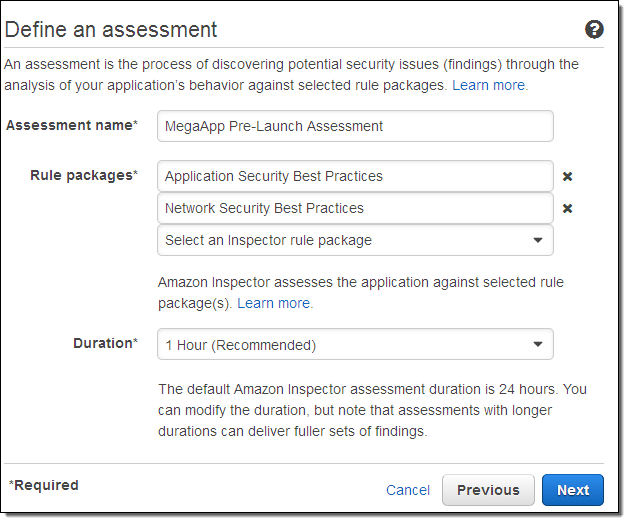
The EC2 instances and other AWS resources that make up your application are identified by tags. When you create the assessment, you also define a duration (15 minutes, 1 / 8 / 12 hours, or 1 day).
During the assessment, an Inspector Agent running on each of the EC2 instances that play host to the application monitors network, file system, and process activity. It also collects other information including details of communication with AWS services, use of secure channels, network traffic between instances, and so forth. This information provides Inspector with a complete picture of the application and its potential security or compliance issues.
After the data has been collected, it is correlated, analyzed, and compared to a set of built-in security rules. The rules include checks against best practices, common compliance standards, and vulnerabilities and represent the collective wisdom of the AWS security team. The members of this team are constantly on the lookout for new vulnerabilities and best practices, which they codify into new rules for Inspector.
The initial launch of Inspector will include the following sets of rules:
- Common Vulnerabilities and Exposure
- CIS Operating System Security Configuration Benchmarks
- Security Best Practices
- Runtime Behavior Analysis
Issues identified by Inspector (we call them “findings”) are gathered together and grouped by severity in a comprehensive report.
You can access the Inspector from the AWS Management Console, AWS Command Line Interface (AWS CLI), or API.
More to Come
I plan to share more information about Inspector shortly after re:Invent wraps up and I have some time to catch my breath, so stay tuned!
— Jeff;