AWS News Blog
EC2 Systems Manager – Configure & Manage EC2 and On-Premises Systems
Last year I introduced you to the EC2 Run Command and showed you how to use it to do remote instance management at scale, first for EC2 instances and then in hybrid and cross-cloud environments. Along the way we added support for Linux instances, making EC2 Run Command a widely applicable and incredibly useful administration tool.
Welcome to the Family
Werner announced the EC2 Systems Manager at AWS re:Invent and I’m finally getting around to telling you about it!
This a new management service that include an enhanced version of EC2 Run Command along with eight other equally useful functions. Like EC2 Run Command it supports hybrid and cross-cloud environments composed of instances and services running Windows and Linux. You simply open up the AWS Management Console, select the instances that you want to manage, and define the tasks that you want to perform (API and CLI access is also available).
Here’s an overview of the improvements and new features:
Run Command – Now allows you to control the velocity of command executions, and to stop issuing commands if the error rate grows too high.
State Manager – Maintains a defined system configuration via policies that are applied at regular intervals.
Parameter Store – Provides centralized (and optionally encrypted) storage for license keys, passwords, user lists, and other values.
Maintenance Window -Specify a time window for installation of updates and other system maintenance.
Software Inventory – Gathers a detailed software and configuration inventory (with user-defined additions) from each instance.
AWS Config Integration – In conjunction with the new software inventory feature, AWS Config can record software inventory changes to your instances.
Patch Management – Simplify and automate the patching process for your instances.
Automation – Simplify AMI building and other recurring AMI-related tasks.
Let’s take a look at each one…
Run Command Improvements
You can now control the number of concurrent command executions. This can be useful in situations where the command references a shared, limited resource such as an internal update or patch server and you want to avoid overloading it with too many requests.
This feature is currently accessible from the CLI and from the API. Here’s a CLI example that limits the number of concurrent executions to 2:
$ aws ssm send-command \
--instance-ids "i-023c301591e6651ea" "i-03cf0fc05ec82a30b" "i-09e4ed09e540caca0" "i-0f6d1fe27dc064099" \
--document-name "AWS-RunShellScript" \
--comment "Run a shell script or specify the commands to run." \
--parameters commands="date" \
--timeout-seconds 600 --output-s3-bucket-name "jbarr-data" \
--region us-east-1 --max-concurrency 2
Here’s a more interesting variant that is driven by tags and tag values by specifying --targets instead of --instance-ids:
$ aws ssm send-command \
--targets "Key=tag:Mode,Values=Production" ... You can also stop issuing commands if they are returning errors, with the option to specify either a maximum number of errors or a failure rate:
$ aws ssm send-command --max-errors 5 ...
$ aws ssm send-command --max-errors 5% ...
State Manager
State Manager helps to keep your instances in a defined state, as defined by a document. You create the document, associate it with a set of target instances, and then create an association to specify when and how often the document should be applied. Here’s a document that updates the message of the day file:
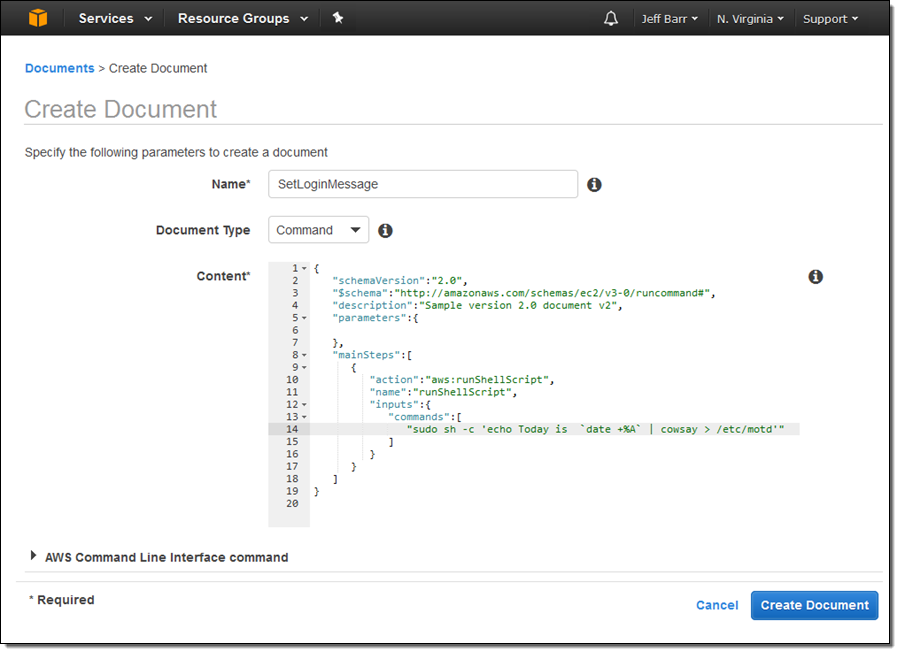
And here’s the association (this one uses tags so that it applies to current instances and to others that are launched later and are tagged in the same way):
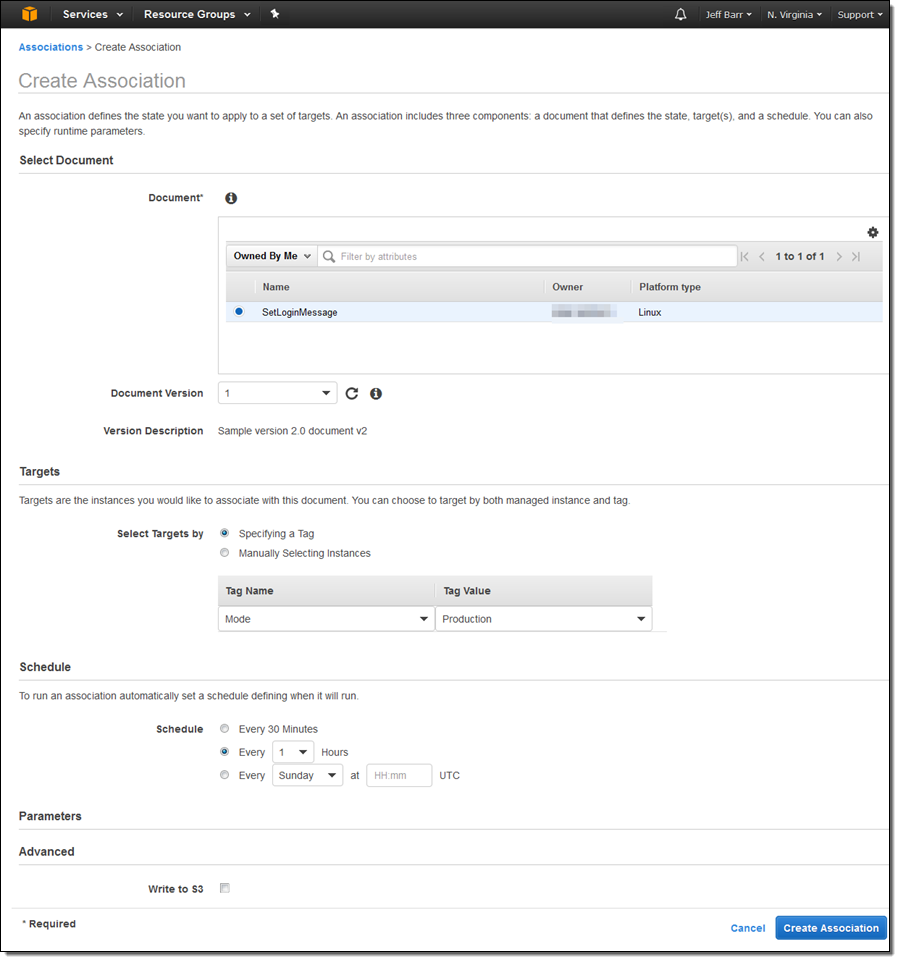
Specifying targets using tags makes the association future-proof, and allows it to work as expected in dynamic, auto-scaled environments. I can see all of my associations, and I can run the new one by selecting it and clicking on Apply Association Now:
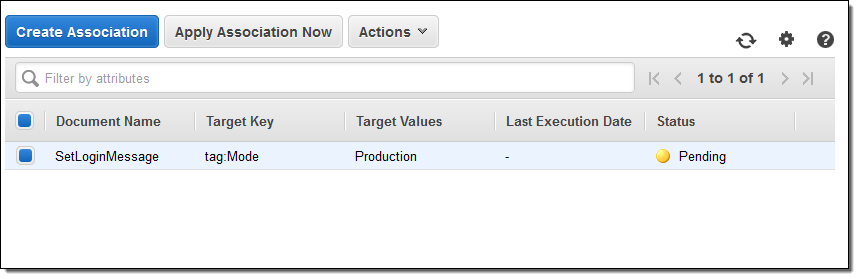
Parameter Store
This feature simplifies storage and management for license keys, passwords, and other data that you want to distribute to your instances. Each parameter has a type (string, string list, or secure string), and can be stored in encrypted form. Here’s how I create a parameter:
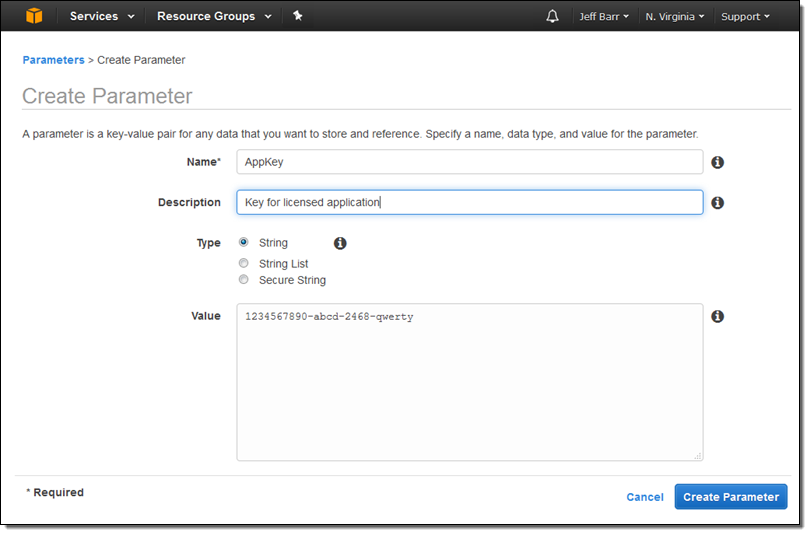
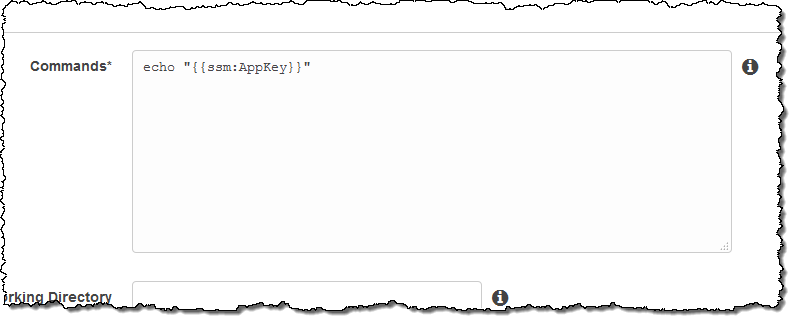
And here’s how I reference the parameter in a command:
Maintenance Window
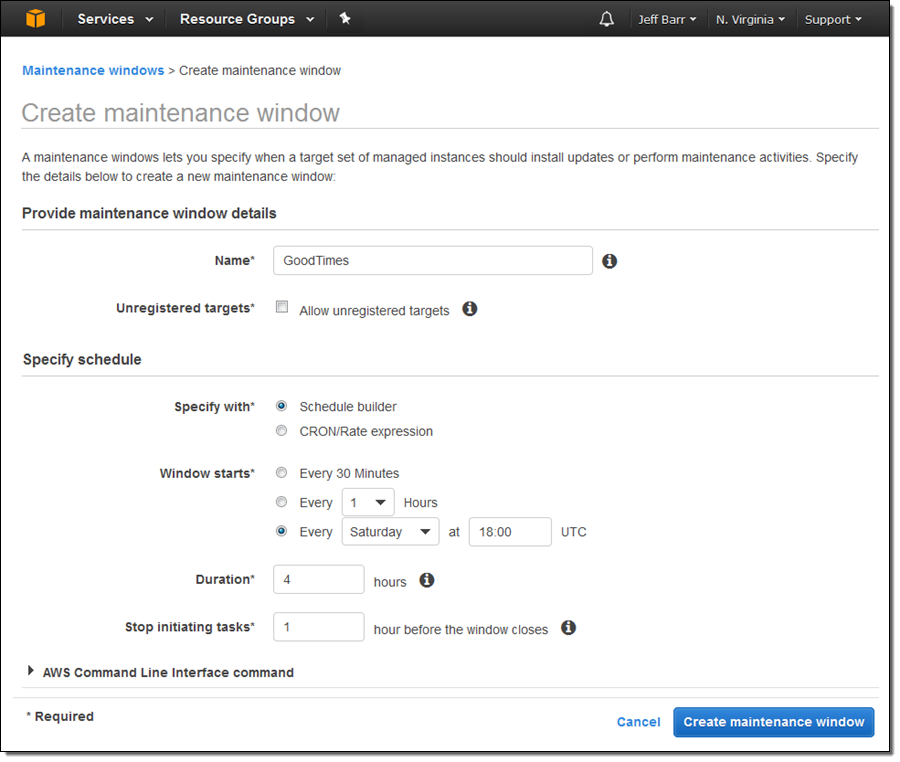
This feature allows specification of a time window for installation of updates and other system maintenance. Here’s how I create a weekly time window that opens for four hours every Saturday:
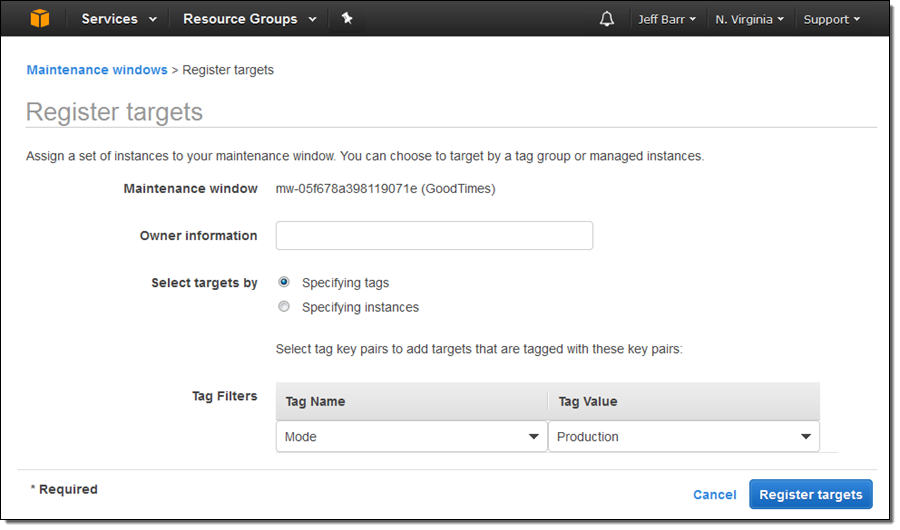
After I create the window I need to assign a set of instances to it. I can do this by instance Id or by tag:
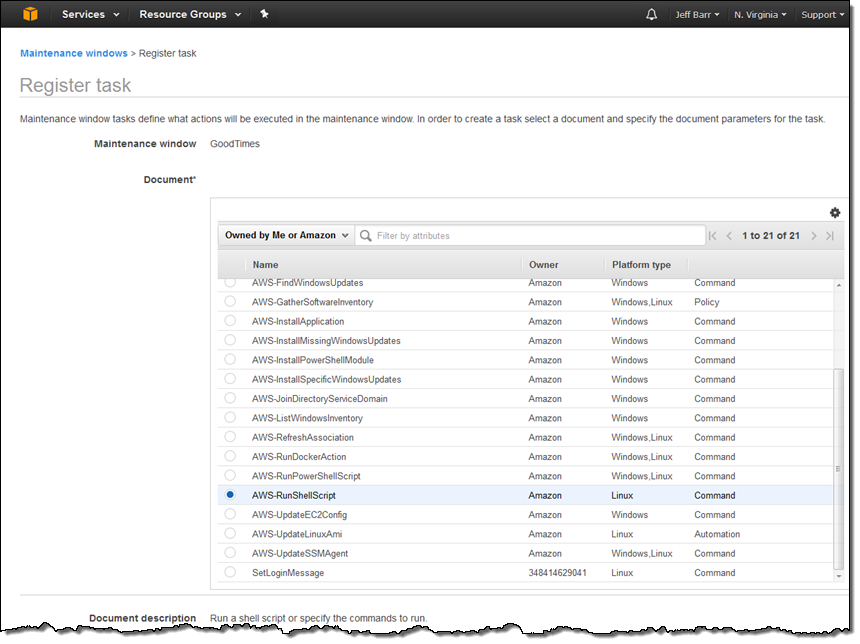
And then I need to register a task to perform during the maintenance window. For example, I can run a Linux shell script:
Software Inventory
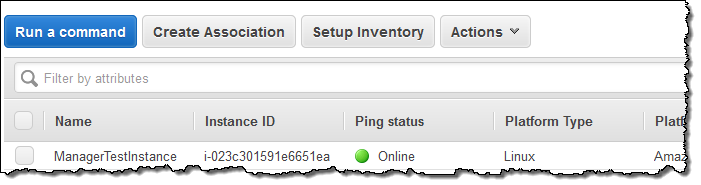
This feature collects information about software and settings for a set of instances. To access it, I click on Managed Instances and Setup Inventory:
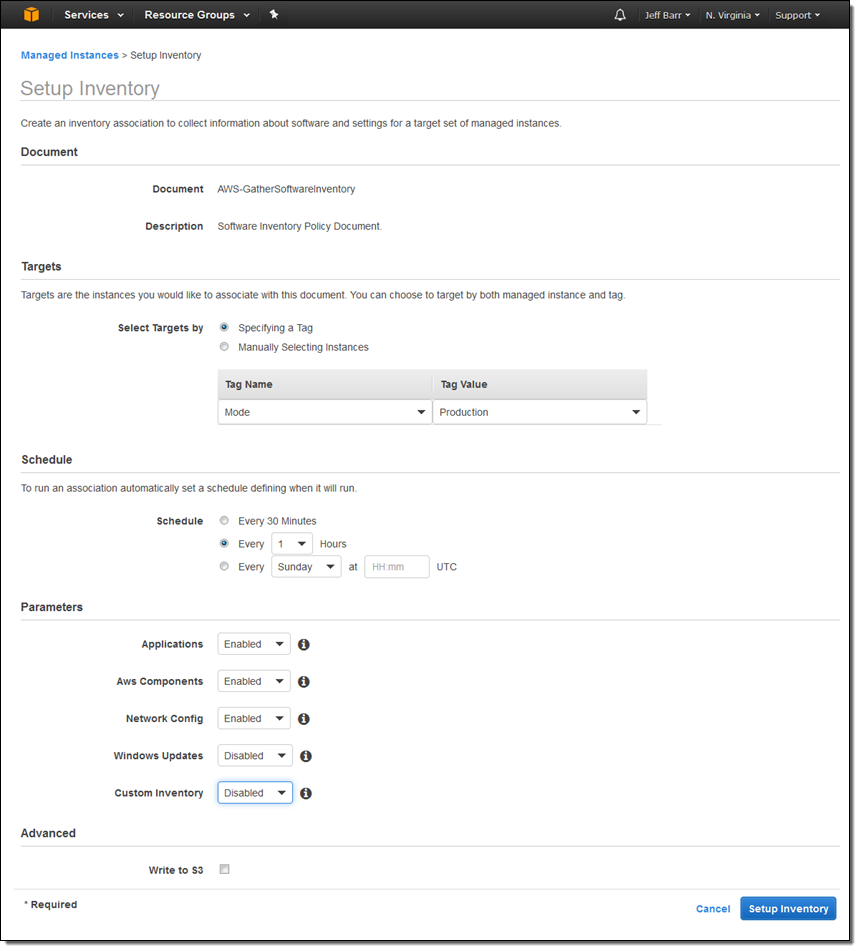
Setting up the inventory creates an association between an AWS-owned document and a set of instances. I simply choose the targets, set the schedule, and identify the types of items to be inventoried, then click on Setup Inventory:
After the inventory runs, I can select an instance and then click on the Inventory tab in order to inspect the results:
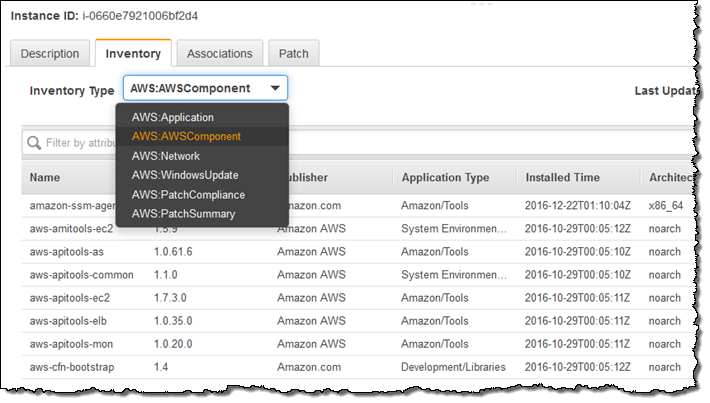
The results can be filtered for further analysis. For example, I can narrow down the list of AWS Components to show only development tools and libraries:
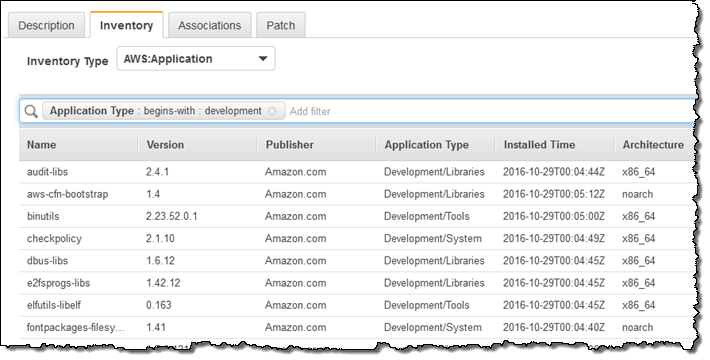
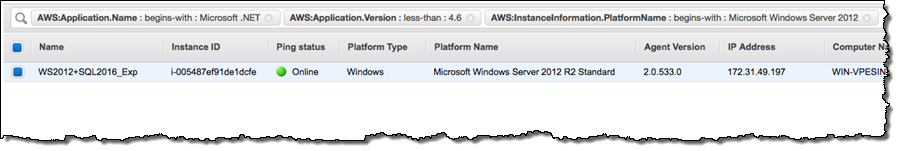
I can also run inventory-powered queries across all of the managed instances. Here’s how I can find Windows Server 2012 R2 instances that are running a version of .NET older than 4.6:
AWS Config Integration
The results of the inventory can be routed to AWS Config and allow you to track changes to the applications, AWS components, instance information, network configuration, and Windows Updates over time. To access this information, I click on Managed instance information above the Config timeline for the instance:
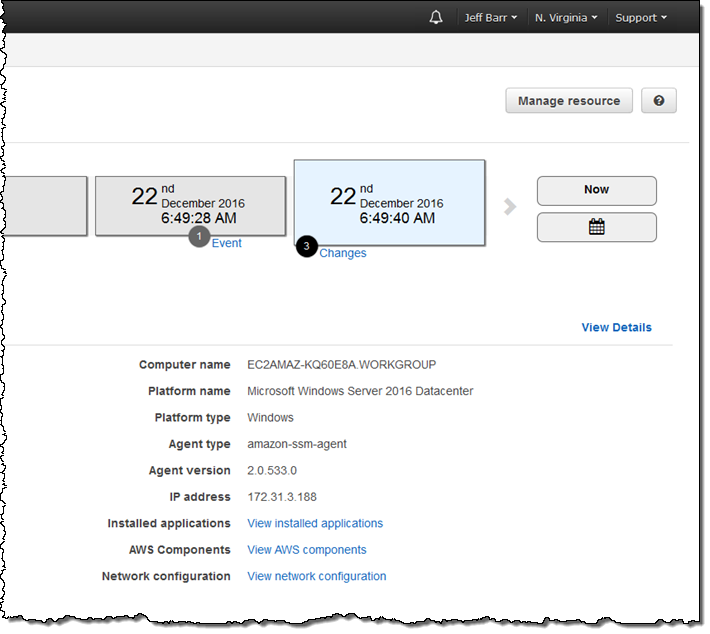
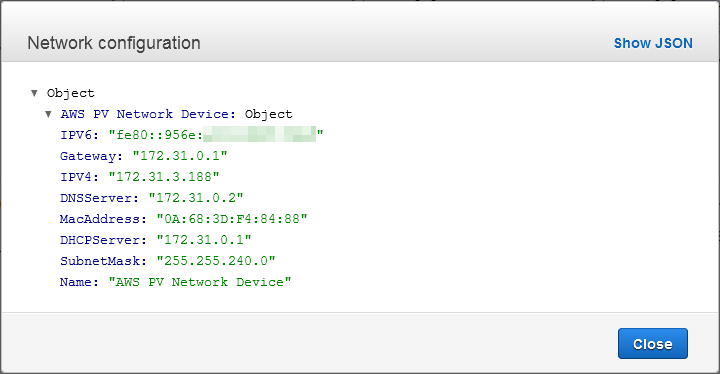
The three lines at the bottom lead to the inventory information. Here’s the network configuration:
Patch Management
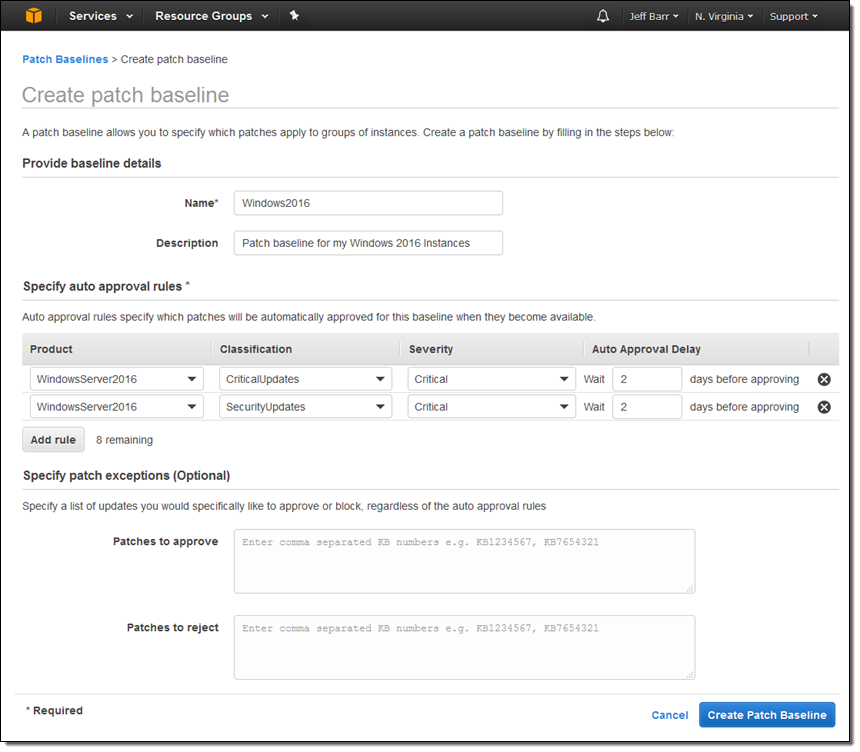
This feature helps you to keep the operating system on your Windows instances up to date. Patches are applied during maintenance windows that you define, and are done with respect to a baseline. The baseline specifies rules for automatic approval of patches based on classification and severity, along with an explicit list of patches to approve or reject.
Here’s my baseline:
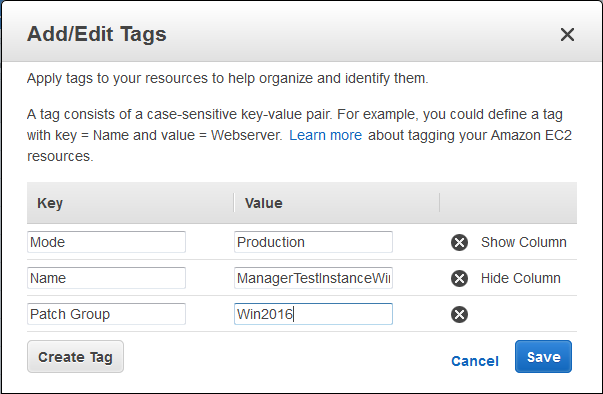
Each baseline can apply to one or more patch groups. Instances within a patch group have a Patch Group tag. I named my group Win2016:
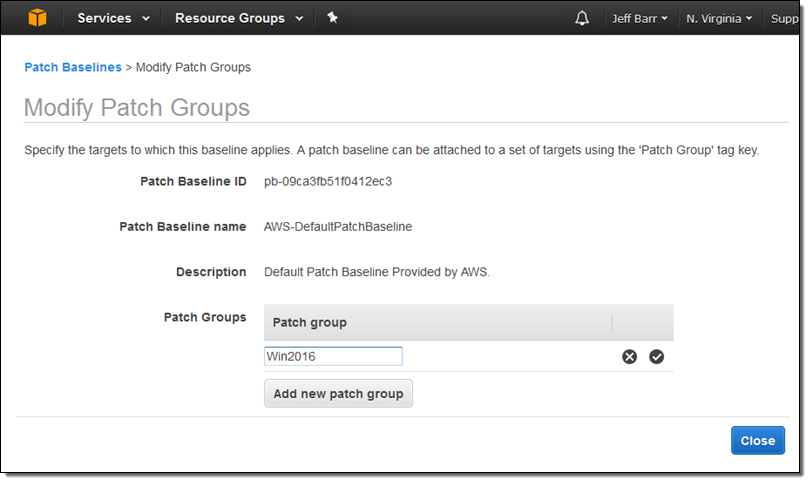
Then I associated the value with the baseline:
The next step is to arrange to apply the patches during a maintenance window using the AWS-ApplyPatchBaseline document:
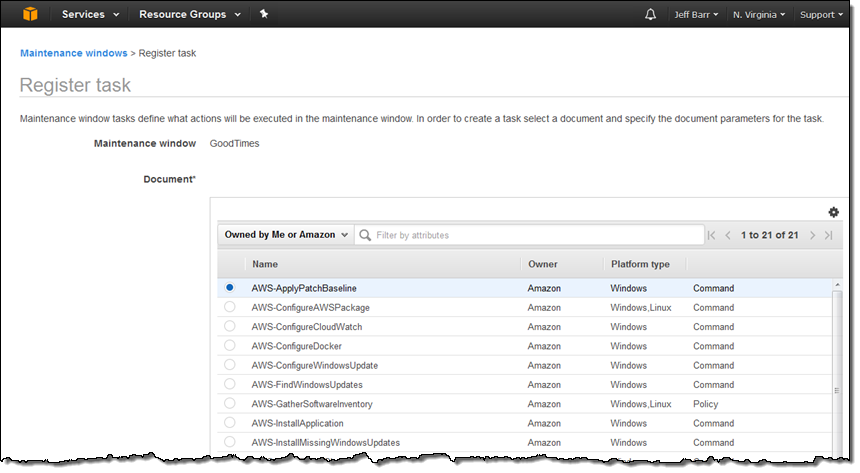
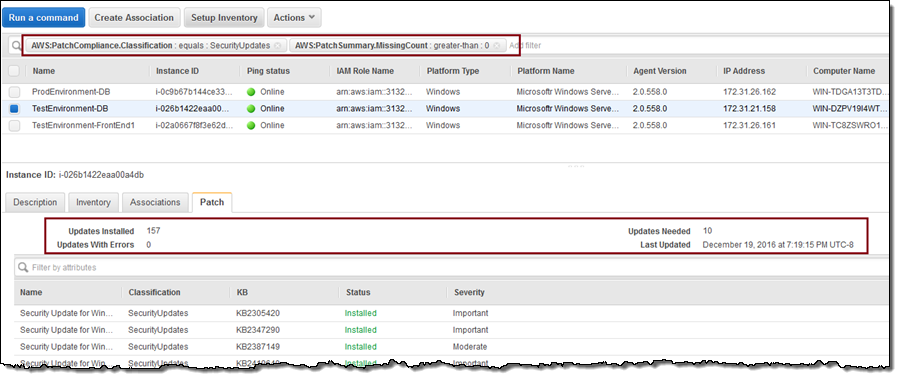
I can return to the list of Managed Instances and use a pair of filters to find out which instances are in need of patches:
Automation
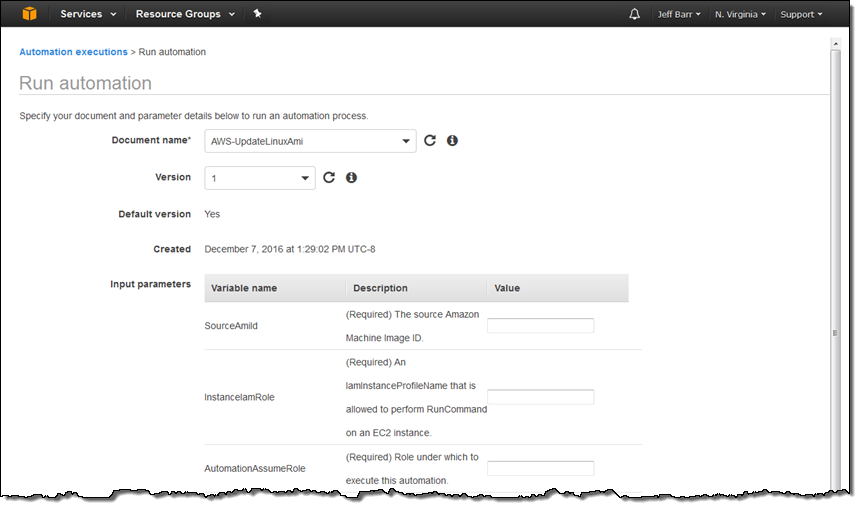
Last but definitely not least, the Automation feature simplifies common AMI-building and updating tasks. For example, you can build a fresh Amazon Linux AMI each month using the AWS-UpdateLinuxAmi document:
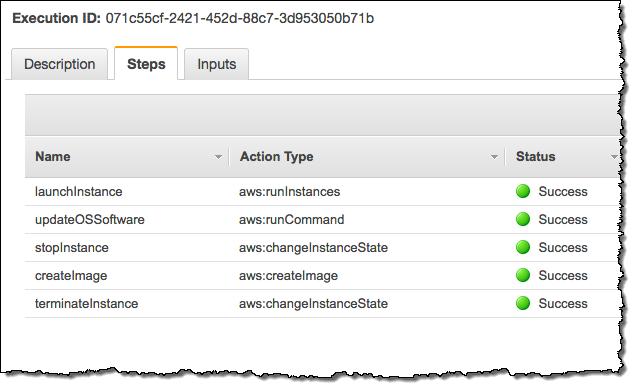
Here’s what happens when this automation is run:
Available Now
All of the EC2 Systems Manager features and functions that I described above are available now and you can start using them today at no charge. You pay only for the resources that you manage.
— Jeff;