AWS News Blog
Amazon Cognito Your User Pools – Now Generally Available
![]() A few months ago I wrote about the new Your User Pools feature for Amazon Cognito. As I wrote at the time, you can use this feature to easily add user sign-up and sign-in to your mobile and web apps. The fully managed user directories can scale to hundreds of millions of users and you can have multiple directories per AWS account. Creating a user pool takes just a few minutes and you can decide exactly which attributes (address, email, gender, phone number, and so forth, plus custom attributes) must be entered when a new user signs up for your app or service. On the security side, you can specify the desired password strength, require the use of Multi-Factor Authentication (MFA), and verify new users via phone number or email address.
A few months ago I wrote about the new Your User Pools feature for Amazon Cognito. As I wrote at the time, you can use this feature to easily add user sign-up and sign-in to your mobile and web apps. The fully managed user directories can scale to hundreds of millions of users and you can have multiple directories per AWS account. Creating a user pool takes just a few minutes and you can decide exactly which attributes (address, email, gender, phone number, and so forth, plus custom attributes) must be entered when a new user signs up for your app or service. On the security side, you can specify the desired password strength, require the use of Multi-Factor Authentication (MFA), and verify new users via phone number or email address.
Now Generally Available
We launched Your User Pools as a public beta and received lots of great feedback. Today we are making Your User Pools generally available and we are also adding a large collection of new features:
- Device Remembering – Cognito can remember the devices that each user signs in from.
- User Search – Search for users in a user pool based on an attribute.
- Customizable Email Addresses – Control the email addresses for emails to users in your user pool.
- Attribute Permissions – Set fine-grained permissions for each user attribute.
- Custom Authentication Flow – Use new APIs and Lambda triggers to customize the sign-in flow.
- Admin Sign-in – Your app can now sign in users from backend servers or Lambda functions.
- Global Sign-out – Allow a user to sign out from all signed-in devices or browsers.
- Custom Expiration Period – Set an expiration period for refresh tokens.
- API Gateway Integration – Use user pool to authorize Amazon API Gateway requests.
- New Regions – Cognito Your User Pools are now available in additional AWS Regions.
Let’s take a closer look at each of these new features!
Device Remembering
Cognito can now remember the set of devices used by (signed in from) each user. You, as the creator of the user pool, have the option to allow your users to request this behavior. If you have enabled MFA for a user pool, you can also choose to eliminate the need for entry of an MFA code on a device that has been remembered. This simplifies and streamlines the login process on a remembered device, while still requiring entry of an MFA code for unrecognized devices. You can also list a user’s devices and allow them to sign out from a device remotely.
You can enable and customize this feature when you create a new user pool; you can also set it up for an existing pool. Here’s how you enable and customize it when you create a new user pool. First you enable the feature by clicking on Always or User Opt-in:
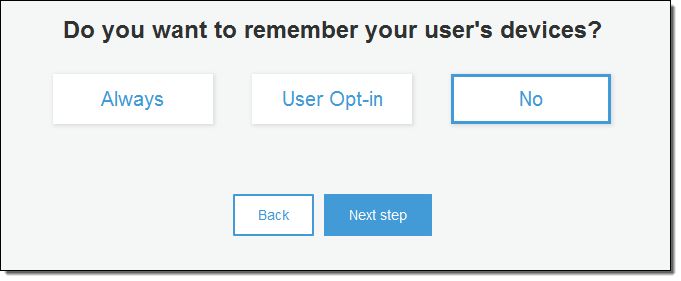
Then you indicate whether you would like to suppress MFA on remembered devices:
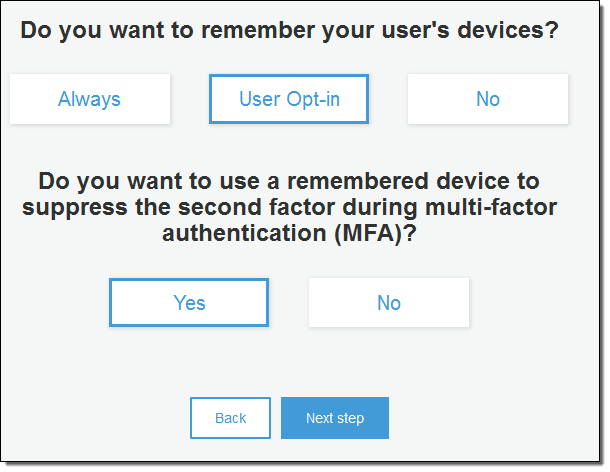
The AWS Mobile SDKs for iOS, Android, and JavaScript contain new methods that you can call from your app to remember devices.
User Search
You, as the creator of a Your User Pool, can now search for users based on a user attribute such as username, given_name, family_name, name, preferred_user_name, email, phone_number, status, or user_status.
You can do a full match or a prefix match using the AWS Management Console, the ListUsers API function, or the list-users command line tool. Here’s a Console-powered search:
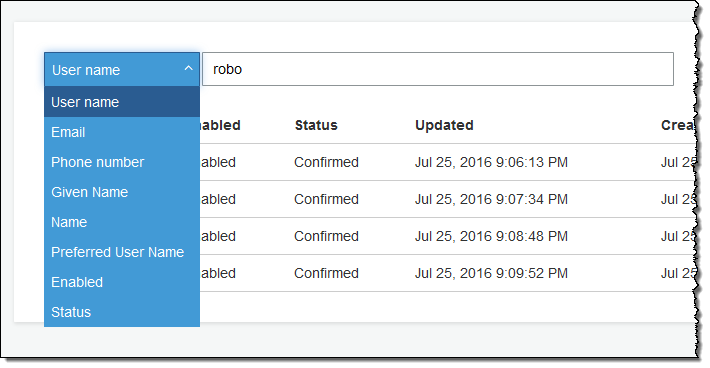
Customizable Email Addresses
You can now specify the From and the Reply-To email addresses that are used to communicate with your users. Here’s how you specify the addresses when you create a new pool:
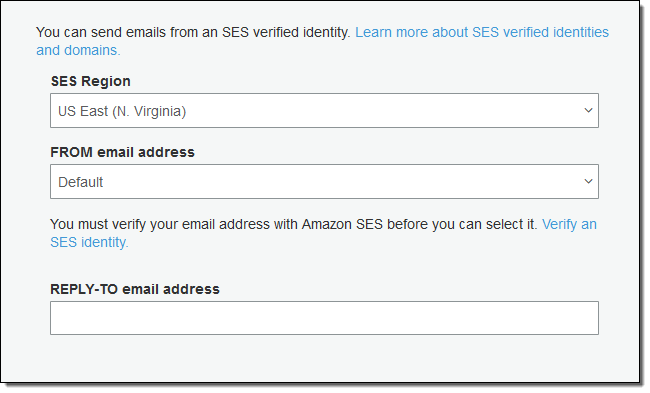
You will need to verify the From address with Amazon Simple Email Service (SES) before you can use it (read Verifying Email Addresses in Amazon SES to learn more).
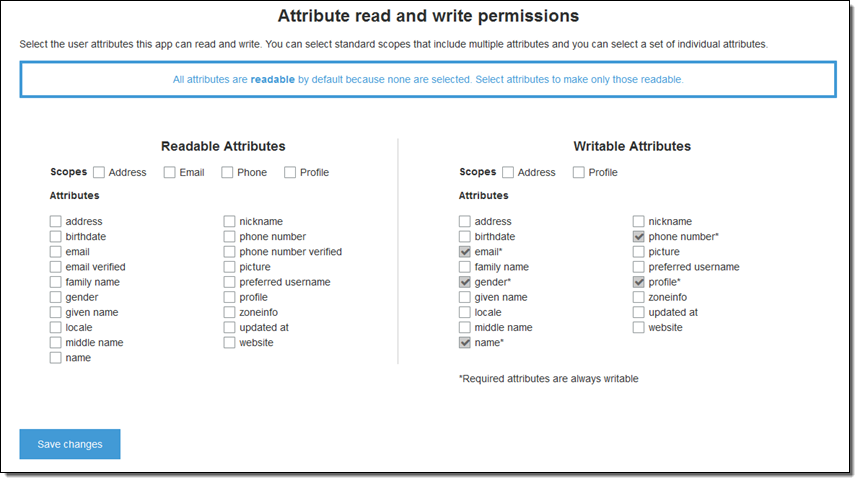
Attribute Permissions
You can now set per-app read and write permissions for each user attribute. This gives you the ability to control which applications can see and/or modify each of the attributes that are stored for your users. For example, you could have a custom attribute that indicates whether a user is a paying customer or not. Your apps could see this attribute but could not modify it directly. Instead, you would update this attribute using an administrative tool or a background process. Permissions for user attributes can be set from the Console, the API, or the CLI.
Custom Authentication Flow
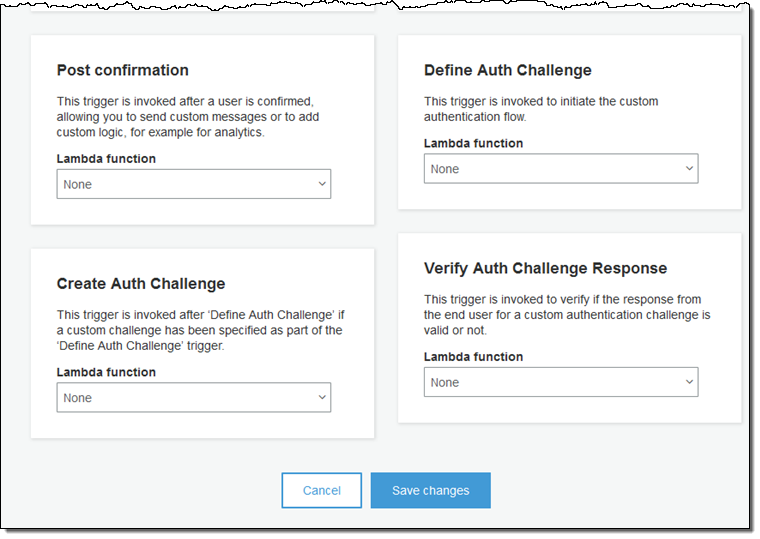
You can now use a pair of new API functions (InitiateAuth and RespondToAuthChallenge) and three new Lambda triggers to create your own sign-in flow or to customize the existing one. You can, for example, customize the user flows for users with different levels of experience, different locations, or different security requirements. You could require the use of a CAPTCHA for some users or for all users, as your needs dictate.
The new Lambda triggers are:
Define Auth Challenge – Invoked to initiate the custom authentication flow.
Create Auth Challenge – Invoked if a custom authentication challenge has been defined.
Verify Auth Challenge Response – Invoked to check the validity of a custom authentication challenge.
You can set up the triggers from the Console like this:
Global Sign-out
You can now give your users the option to sign out (by invalidating tokens) of all of the devices where they had been signed in. Apps can call the [GlobalSignOut] function using a valid, non-expired, non-revoked access token. Developers can remotely sign out any user by calling the [AdminUserGlobalSignOut] function using a Pool ID and a username.
Custom Expiration Period
Cognito sign-in makes use of “refresh” tokens to eliminate the need to sign in every time an application is opened. By default, the token expires after 30 days. In order to give you more control over the balance between security and convenience, you can now set a custom expiration period for the refresh tokens generated by each of your user pools.
API Gateway Integration
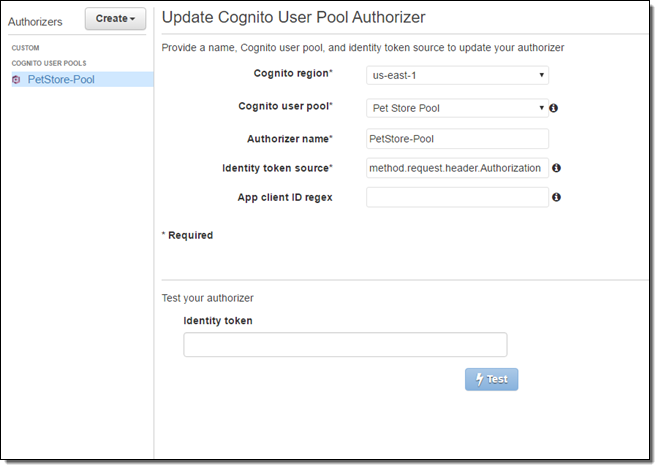
Cognito user pools can now work hand-in-hand with Amazon API Gateway to authorize API requests. You can configure API Gateway to accept Id tokens to authorize users based on their presence in a user pool.
To do this, you first create a Cognito User Pool Authorizer using the API Gateway Console, referencing the user pool and choosing the request header that will contain the identity token:
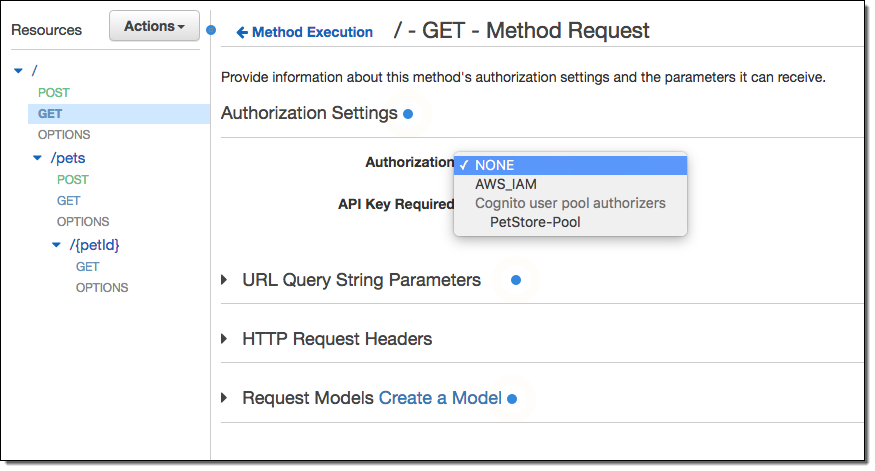
Navigate to the desired method and select the new Authorizer:
New Regions
As part of today’s launch we are making Cognito available in the US West (Oregon) Region.
In addition to the existing availability in the US East (N. Virginia) Region, we are making Your User Pools available in the Europe (Ireland), US West (Oregon), and Asia Pacific (Tokyo) Regions.
Available Now
These new features are available now and you can start using them today! To learn more, watch Getting Started with Your User Pools in Amazon Cognito.
— Jeff;