AWS News Blog
New VPC Peering for the Amazon Virtual Private Cloud
The Amazon Virtual Private Cloud (VPC) gives you the power to create a logically isolated section of the AWS Cloud, which you can think of as virtual network. You can launch AWS resources, including Amazon EC2 instances within the network, and you have full control over the virtual networking environment, including the IP address range and the subnet model. You also have full control over network routing, both within the VPC (using route tables) and between networks (using network gateways).
VPC Peering
Today we are making the VPC model even more flexible! You now have the ability to create a VPC peering connection between VPCs in the same AWS Region. Once established, EC2 instances in the peered VPCs can communicate with each other across the peering connection using their private IP addresses, just as if they were within the same network.
You can create a peering connection between two of your own VPCs, or with a VPC in another AWS account.A VPC can have one-to-one peering connections with up to 50 other VPCs in the same Region.
VPC peering enables a number of interesting use cases; let’s take a look at a couple of them.
Within a single organization, you can set up peering relationships between VPCs that are run by different departments. One VPC can encompass resources that are shared across an entire organization, with additional, per-department VPCs for resources that are peculiar to the department. Here’s a very simple example:
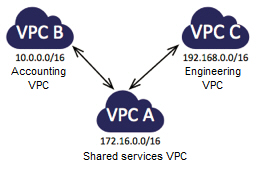
After you set up the peering connections and add entries to the routing tables (to direct packets out of one VPC and into another), the EC2 instances in the Accounting VPC can access the Shared Resources VPC, as can the instances in the Engineering VPC. However, the Accounting instances cannot access the Engineering instances, or vice versa. Peering connections are not transitive; you would need to set up a peering connection between Engineering and Accounting in order to establish connectivity. Think about extending this model with an Operations VPC that is peered with all of the other VPCs in your organization.
As I mentioned earlier, you can also establish VPC peering between a pair of VPCs that are owned by different accounts. Suppose your organization is a member of an industry consortium or a party to a joint venture. You can use VPC peering to share common resources between members of the consortium or other joint venture, all within AWS and with full control of the networking topology:
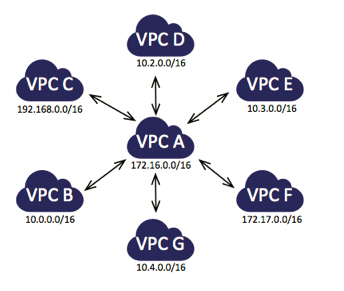
As was the case in the previous scenario, each participant in the consortium will be able to see and access the shared resources, but not those of the other participants. We’ve documented a number of common peering scenarios in our VPC Peering Guide.
Peering Details
I’m going to show you just how easy it is to create a VPC peering connection in just a minute. Before I do that, I’d like to review the rules that govern the use of this very powerful new feature.
You can connect any two VPCs that are in the same AWS Region, regardless of ownership, as long as both parties agree. We plan to extend this feature to support cross-Region peering in the future. Connections are requested by sending an invitation from one VPC to the other. The invitation must be accepted in order to establish the connection. Needless to say, you should only accept invitations from VPCs that you know. You are free to ignore unwanted or incorrect invitations; they’ll expire before too long.
The VPCs to be peered must have non-overlapping CIDR blocks. This is to ensure that all of the private IP addresses are unique, allowing direct access (as allowed by the peering and routing tables) without the need for any form of network address translation.
As you can see from the scenarios that I described above, VPC peering connections do not generate transitive trust. Just because A is peered with B and B is peered with C, it doesn’t mean that A is peered with C.
The connections are implemented within the VPC fabric; this avoids single points of failure and bandwidth bottlenecks.
There is no charge for setting up or running a VPC peering connection. Data transferred across peering connections is charged at $0.01/GB for send and receive, regardless of the Availability Zones involved.
You can set up VPC peering connections from the AWS Management Console, the VPC APIs, or the AWS Command Line Interface (CLI).
VPC Peering Example
I used the AWS Management Console to set up a VPC peering connection between two of my VPCs, which were named corporate-vpc and branch-east-vpc. Here are the IDs and the CIDRs:
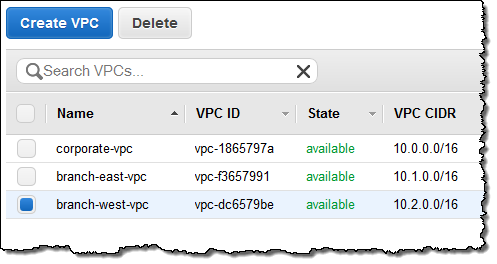
Before I go any further, I should note that these features are available in the “Preview” version of the VPC console. In addition to support for the creation and management of VPC peering connections, the new console includes a multitude of tagging features to simplify and enhance your VPC management operations.
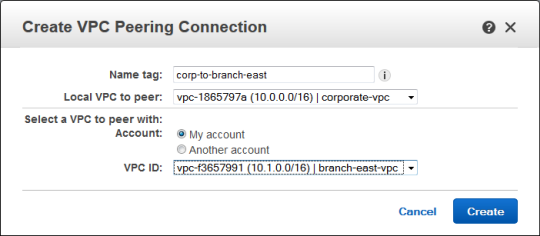
I clicked on Peering Connections in the VPC Dashboard, selected corporate-vpc, and then used the Create VPC Peering Connection button to invite branch-east-vpc to peer:
The invite appeared in the list of connections. I selected it and clicked Accept:
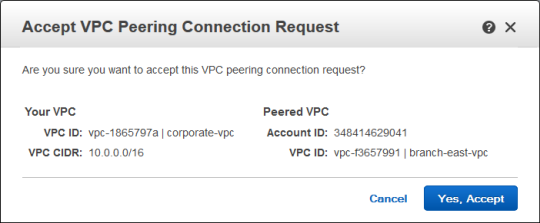
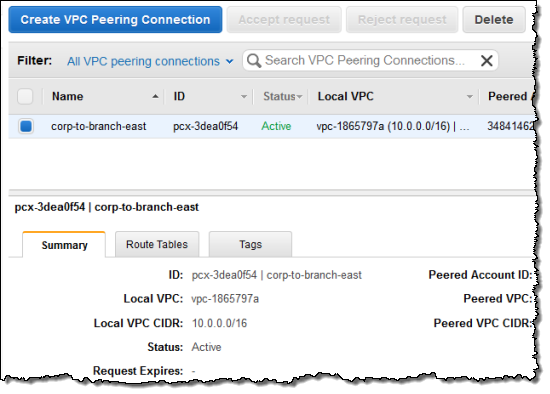
The peering connection was created and became visible immediately:
Then I created an entry in the route table of each VPC. As you can see, the console provided me with a helpful popup when it was time for me to choose the Target for the route:
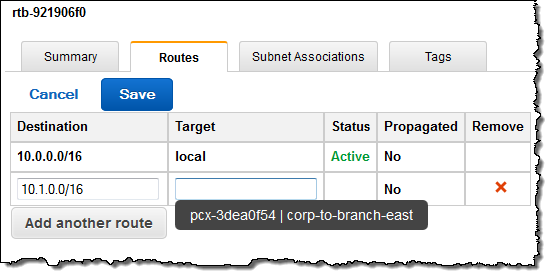
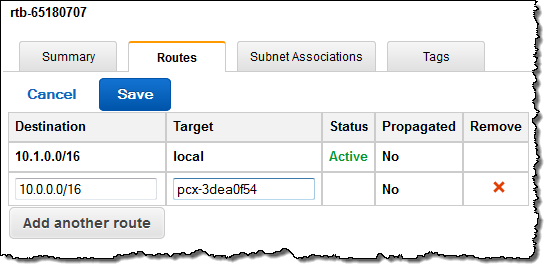
Peer Now
The new VPC peering feature is available now and you can start using it today. I am very interested in seeing how this feature is put to use. Leave me a comment and let me know what you think!
— Jeff;