AWS News Blog
Elastic Transcoder Update – AES-128 Encryption for HLS Content
Amazon Elastic Transcoder lets you convert media files in to versions that will play on smart phones, tablets, PCs, and smart TVs. As I have mentioned in the past, it takes care of all of the more tedious aspects of the media transcoding process on your behalf. You create a transcoding job and Elastic Transcoder will take care of everything else.
We have made a number of important improvements to Elastic Transcoder in the last couple of months. Here’s a recap:
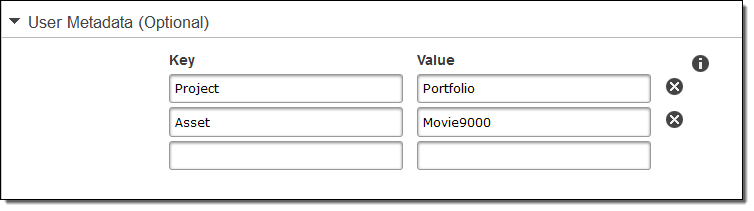
- Custom Metadata Pass-Through – Last December we gave you the ability to attach up to ten key-value pairs to each of your Elastic Transcoder jobs. The metadata is included in job notifications and can be used to map your jobs back to the content in your internal Content Management System (CMS):
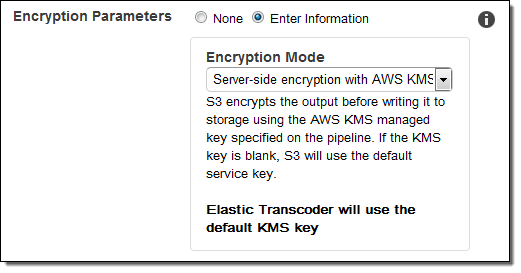
- Media File Encryption – Last November we announced AWS Key Management Service (AWS KMS) support for Elastic Transcoder. This release gave you the power to ensure the confidentiality of media assets (mezzanine files, thumbnails, captions, and watermarks) as they move between your application and the Elastic Transcoder service. This launch let you control who could decrypt your content and also allowed you to use AWS CloudTrail to create an audit report of all encryption and decryption operations:
- CloudTrail Integration – Announced last October, API calls made to Elastic Transcoder are recorded, logged, and then delivered to the Amazon Simple Storage Service (Amazon S3) bucket of your choice.
- Support for HLS v4 – Also announced last October, this feature supports the popular HTTPS Live Streaming (HLS) protocol, commonly used on newer iOS and Android devices.
AES-128 Encryption to Protect HLS Content
Today we are making another improvement to Elastic Transcoder. You can now use AES-128 encryption to protect the transcoded files (which are broken down by HLS into smaller pieces commonly known as media segments), while still making use of generic content delivery mechanisms!
When you enable this feature, each media segment is encrypted using AES-128 and a single encryption key. A URL to the decryption key is written to each playlist (HLS supports multiple encodings known as variants; each one supports an alternate rendering of the same content). When the content is viewed, the player will download the key and decrypt the media segments during the playback process.
In order to make use of this new feature, you need to associate an Elastic Transcoder pipeline with a KMS master key. You have two choices when it comes to keys: you can create your own keys or you can have Elastic Transcoder generate them for you. Regardless of the option that you choose, you need to wait for the job to complete and then store the key in a database that you manage (this information is available to you via the ReadJob API).
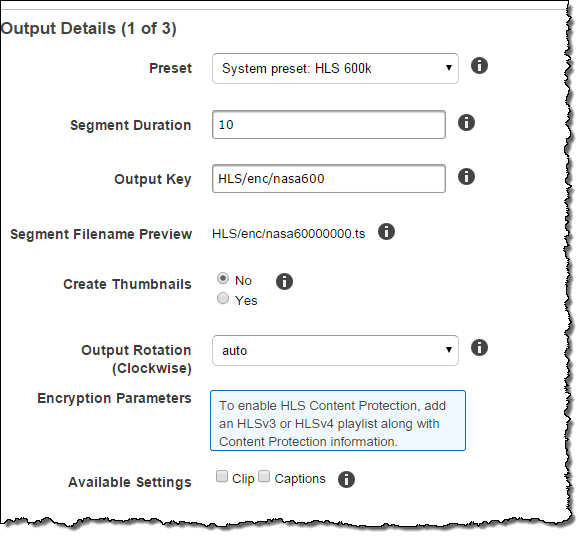
To enable HLS content protection, you simply add an HLS v3 or HLS v4 playlist to your transcoding job, along with the content protection information:
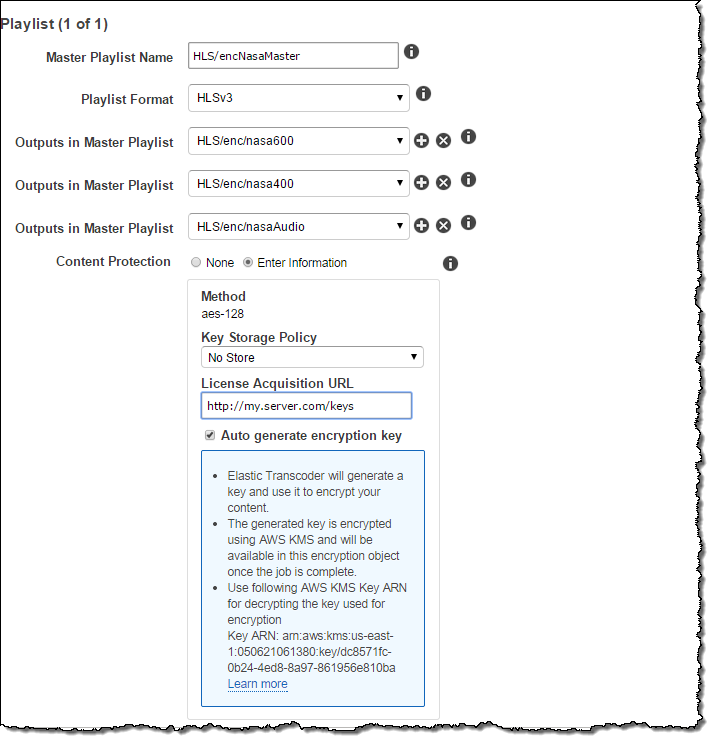
Here’s how you enter the content protection information:
Playing Back Protected Content
Each variant playlist will contain a URL that the media player will use to fetch the content protection key using a standard HTTP request. In order to protect access to the key, the content provider must authenticate and authorize the media player. The authentication should result in a session cookie that identifies the media player. The content provider should mandate that the cookie is present and acceptable before returning the key. This mechanism will prevent unauthorized playback and decryption of the content.
If you choose to use a Content Distribution Network (CDN) such as Amazon CloudFront to distribute your content, you will need to ensure that the encrypted media files are accessible from your CloudFront distribution. However, you must be careful not to store your keys in a publicly accessible location. For safety and simplicity, we recommend that you use the “No Store” key storage policy so that your key is never written to file storage.
Full information on use of AES-128 to protect content is available in the Elastic Transcoder Developer Guide.
Pricing and Availability
This feature is available now and you can start using it today. There’s no extra charge for the use of AES-128 encryption; you pay only for the content that you transcode (see the Elastic Transcoder Pricing page for more information).
— Jeff;