AWS News Blog
New – VPC Endpoint for Amazon S3
I would like to tell you about a new AWS feature that will allow you to make even better use of Amazon Virtual Private Cloud (Amazon VPC) and Amazon Simple Storage Service (Amazon S3). As you probably know, S3 provides you with secure, durable, and highly scalable object storage. You can use the Amazon VPC to create a logically isolated section of the AWS Cloud, with full control over a virtual network that you define.
When you create a VPC, you use security groups and access control lists (ACLs) to control inbound and outbound traffic. Until now, if you wanted your EC2 instances to be able to access public resources, you had to use an Internet Gateway, and potentially manage some NAT instances.
New VPC Endpoint for S3
Today we are simplifying access to S3 resources from within a VPC by introducing the concept of a VPC Endpoint. These endpoints are easy to configure, highly reliable, and provide a secure connection to S3 that does not require a gateway or NAT instances.
EC2 instances running in private subnets of a VPC can now have controlled access to S3 buckets, objects, and API functions that are in the same region as the VPC. You can use an S3 bucket policy to indicate which VPCs and which VPC Endpoints have access to your S3 buckets.
Creating and Using VPC Endpoints
You can create and configure VPC Endpoints using the AWS Management Console, AWS Command Line Interface (AWS CLI), AWS Tools for Windows PowerShell, and the VPC API. Let’s create one using the console! Start by opening up the VPC Dashboard and selecting the desired region. Locate the Endpoints item in the navigation bar and click on it:
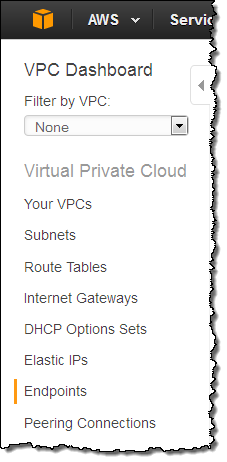
If you have already created some VPC Endpoints, they will appear in the list:
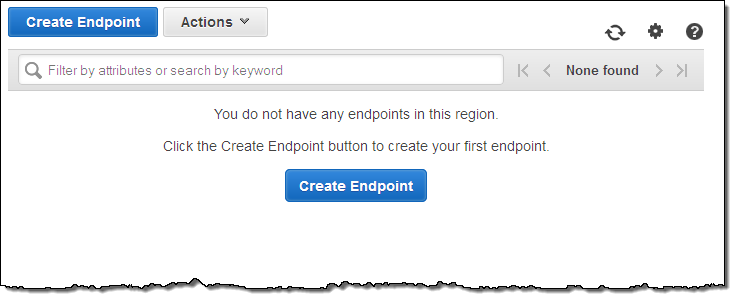 Now click on Create Endpoint, choose the desired VPC, and customize the access policy (if you want):
Now click on Create Endpoint, choose the desired VPC, and customize the access policy (if you want):
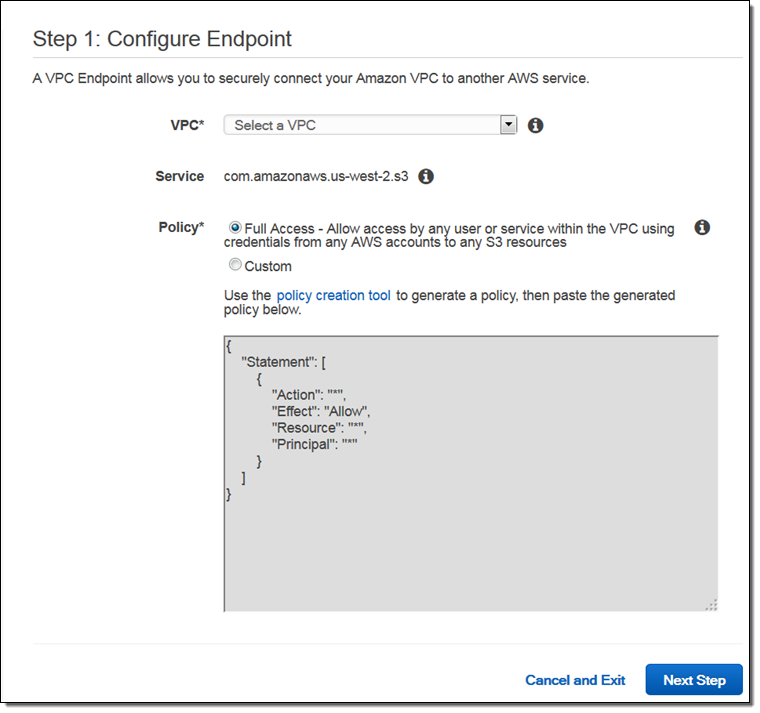
The access policy on the VPC Endpoint allows you disallow requests to untrusted S3 buckets (by default a VPC Endpoint can access any S3 bucket). You can also use access policies on your S3 buckets to control access from a specific VPC or VPC Endpoint. These access policies would use the new aws:SourceVpc and aws:SourceVpce conditions (read the documentation to learn more).
As you might be able to guess from the screen above, you will eventually be able to create VPC Endpoints for other AWS services!
Now choose the VPC subnets that will be allowed to access the endpoint:
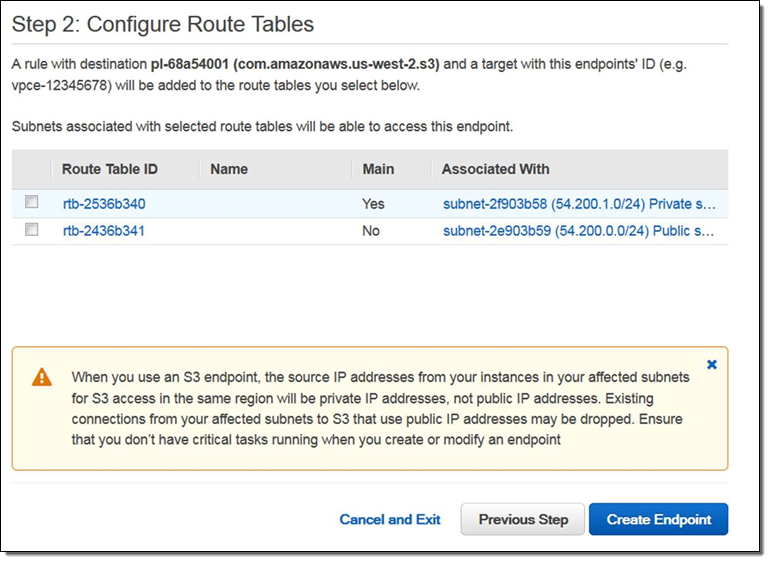
As indicated in the note on the screen above, open connections using an instance’s public IP address in the affected subnets will be dropped when you create the VPC Endpoint.
Once you create the VPC Endpoint, the S3 public endpoints and DNS names will continue to work as expected. The Endpoint simply changes the way in which the requests are routed from EC2 to S3.
Available Now
Amazon VPC Endpoints for Amazon S3 are available now in the US East (N. Virginia) (for access to the US Standard region), US West (Oregon), US West (N. California), Europe (Ireland), Europe (Frankfurt), Asia Pacific (Tokyo), Asia Pacific (Singapore), and Asia Pacific (Sydney) regions. You can start using them today. Read the documentation to learn more.
— Jeff;