AWS Security Blog
How to retrieve short-term credentials for CLI use with AWS IAM Identity Center
May 23, 2022: This blog post is out of date. Please refer here for current info: https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-sso.html
September 12, 2022: This blog post has been updated to reflect the new name of AWS Single Sign-On (SSO) – AWS IAM Identity Center. Read more about the name change here.
Today, AWS made it easier to use the AWS Command Line Interface (CLI) to manage services in your AWS accounts. Now you can sign into the AWS IAM Identity Center user portal using your existing corporate credentials, choose an AWS account and a specific permission set, and get temporary credentials to manage your AWS services through the AWS CLI.
AWS IAM Identity Center is a service that enables you to centrally manage IAM Identity Center access to multiple AWS accounts and business applications. AWS temporary security credentials are an easy way to get short-term credentials to manage your AWS services through the AWS CLI or a programmatic client.
Previously, when you issued commands from the CLI to access resources in each of several AWS accounts, you had to remember the password for each account, sign in to each AWS account individually, and fetch the credentials for each account one at a time. Now, AWS IAM Identity Center eliminates the need to sign in to each AWS account individually to get temporary credentials. Instead, you can sign in to the AWS IAM Identity Center user portal once using your existing corporate credentials and then fetch temporary credentials for any of your authorized AWS accounts to use with the AWS CLI to access the resources in that account, limited by the permissions granted to you.
In this blog post, I’ll show how to fetch temporary credentials from the AWS IAM Identity Center user portal to use with the AWS CLI to access resources in your AWS accounts. First, I’ll show you how to obtain short-term credentials for any account for a permission set for which you are authorized. Next, I’ll show you three ways to use these credentials.
For this scenario, let’s say I am an administrator at “AnyCompany” and I want to list instances in two AWS accounts by using the AWS CLI command, aws ec2 describe-instances. “AnyCompany” has enabled access to AWS accounts through AWS IAM Identity Center.
Prerequisites
You need to install the AWS CLI to use this feature. You also need to configure AWS IAM Identity Center, connect a corporate directory, and grant access to users or groups to access AWS accounts with permission sets. To learn more, see, “Introducing AWS IAM Identity Center“.
How to access resources in your AWS accounts by using AWS IAM Identity Center and the AWS CLI
1. Sign in to the AWS IAM Identity Center user portal using your corporate credentials. If you don’t know the URL of your AWS IAM Identity Center user portal, ask your IT administrator. This URL can be found in AWS IAM Identity Center Console in the Dashboard menu, under “User portal URL” section. In the user portal, you will see the AWS accounts to which you have been granted access.

2. Choose “AWS Account” to expand the list of AWS accounts.

3. Choose the AWS account that you want to access using the AWS CLI. This expands the list of permission sets in the account that you can use to access the account. For this example, I choose “Administrator” permission set which has the necessary permissions to create security groups in accounts. I then choose “Command Line” or “Programmatic Access” associated with the “Administrator” permissions set.

4. AWS IAM Identity Center shows the credentials you requested in the appropriate format for your operating system. If you need credentials for an operating system that is different from the one shown, you can switch between the MacOS and Linux and Windows tabs. AWS IAM Identity Center offers three options to use the temporary security credentials (these credentials are valid for up to 60 minutes; see the following screenshot for examples of each option):
a. To run commands from the AWS CLI against the selected AWS account, copy the commands in the “Setup AWS CLI environment variables” section and paste the commands in the terminal window to set the necessary environment variables. These environment variables will be effective in the current terminal window.
b. To run commands from multiple terminal windows against the same AWS account, copy the profile in the “Setup AWS CLI profile” section to setup a new named profile in your AWS credentials file. To learn more, see: “Configuration and Credential Files“. You then will be able to use the –profile option with your AWS CLI command to use this credential. This will be effective in all terminal windows that use the same credential file.
c. To access AWS resources from an AWS service client, use the credentials under the “Copy individual values” section to initialize your client. For more information, see the “Use the temporary credentials to access AWS resources” section on “Getting Temporary Credentials with AWS STS“.

5. Move your mouse over the option you want to copy credentials. I chose option 1.

6. I have copied, pasted, and run the AWS CLI environment variables commands in my terminal window:
$ export AWS_ACCESS_KEY_ID=“ASIAJWOHLDZASDEXAMPLE"
$ export AWS_SECRET_ACCESS_KEY="feTxcGI2aus2m4RZh+eDASvqw3vOq/jS+EXAMPLE"
$ export AWS_SESSION_TOKEN="FQoDYXdzEFQaDIiq9STHISISEXAMPLE”
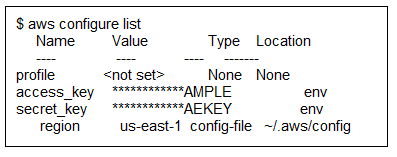
7. Optionally, you can verify that the credentials are set up correctly by running the “aws configure list” command. Verify that the access_key and secret_key have values assigned.
8. Now you can run any applicable AWS CLI commands (based on the permission set granted to you by your administrator). In the following example, I list instances in my AWS account.

9. To run the same (or different) AWS CLI command against a different AWS account, repeat this process, starting with Step 3. By keeping the AWS IAM Identity Center user portal open in a browser window, you can easily switch to another AWS account without needing to sign in again. Every time you want to switch between accounts/permission sets or do additional work in an account after the temporary credentials expire, just copy fresh credentials for that account/permission set from the user portal.
Conclusion
In this post, in order to manage services using the AWS CLI, I’ve showed you how to use your existing corporate username and password to get temporary credentials from AWS IAM Identity Center. If you have questions, please start a new thread in the AWS IAM Identity Center Forum.
– Anand Murugesan