Category: IAM
Additional IAM Support in the AWS Billing Console
AWS Identity and Access Management (IAM) gives you fine-grained control over access to AWS services and resources. You can create and manage AWS users and groups and then use IAM permissions (in the form of policies) to allow and deny access to AWS resources.
The AWS Billing Console lets you see how much you are spending on AWS (in total and by service) and also lets you view and modify account and payment information. You can take a look at my recent blog post on the Updated AWS Billing Console.
Today we are enhancing the AWS Billing Console with finer-grained permissions. You can grant read-only access to IAM users,along with additional options for write access. Your IAM policies can use the following new actions to regulate access to various parts of the console:
ViewBillingandModifyBilling– Control access to the Dashboard, Bills, Cost Explorer, Payment History, Consolidated Billing, and Reports pages.ViewAccountandModifyAccount– Control access to the Account Settings page.ViewPaymentMethodsandModifyPaymentMethods– Control access to the Payment Methods page.
By making judicious use of these verbs, you can implement a clean separation of AWS duties within your organization. Developers can use the AWS SDKs to develop AWS-powered applications, administrators can manage production servers, databases, and networks, and the finance folks can watch over and control payments. If you want, you can give administrators and developers read-only access to billing information so that they can have a better understanding of the financial side of their work.
To learn more about this new feature, read about IAM Enhanced Capabilities for the AWS Billing Consoleon the AWS Security Blog.
— Jeff;
AWS May Webinars – Focus on Security
We have received a lot of great feedback on the partner webinars that we held in April. In conjunction with our partners, we will be holding two more webinars this month. The webinars are free, but space is limited and preregistration is advisable.
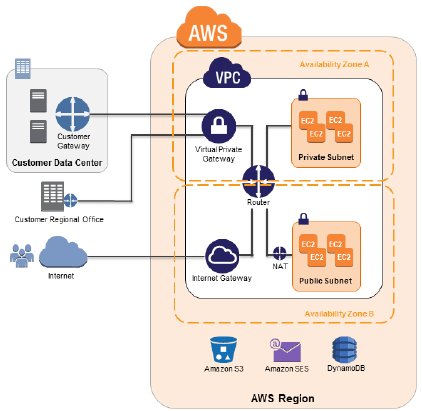 In May we are turning our focus to the all-important topic of security, and what it means in the cloud. When I first started talking about cloud computing, audiences would listen intently, and then ask “But what about security?” This question told me two things. First, it told me that the questioner saw some real potential in the cloud and might be able to use it on some mission-critical applications. Second, that it was very important that we share as much as possible about the security principles and practices within and around AWS. We built and maintain AWS Security Center and have published multiple editions of the Overview of Security Processes.
In May we are turning our focus to the all-important topic of security, and what it means in the cloud. When I first started talking about cloud computing, audiences would listen intently, and then ask “But what about security?” This question told me two things. First, it told me that the questioner saw some real potential in the cloud and might be able to use it on some mission-critical applications. Second, that it was very important that we share as much as possible about the security principles and practices within and around AWS. We built and maintain AWS Security Center and have published multiple editions of the Overview of Security Processes.
In our never-ending quest to keep you as fully informed as possible about this important topic, we have worked with two APN Technology Partners to bring you some new and exciting information.
May 20 – Log Collection and Analysis (Splunk and CloudTrail)
At 10:00 AM PT on May 20, AWS and Splunk will present the Stronger Security and Compliance on AWS with Log Collection and Analysis webinar. In the webinar you will learn how CloudTrail collects and stores your AWS log files so that software from Splunk can be used as a Big Data Security Information and Event Management (SIEM) system. You will hear how AWS log files are made available for many security use cases, including incident investigations, security and compliance reporting, and threat detection/alerting. FINRA (a joint Splunk/AWS customer) will explain how they leverage Splunk on AWS to support their cloud efforts.
May 28 – Federated Single Sign-On (Ping Identity and IAM)
At 10:00 AM PT on May 28, AWS and Ping Identity will present the Get Closer to the Cloud with Federated Single Sign-On webinar.
In the webinar you will learn how the Ping Identity platform offers federated single sign-on (SSO) to quickly and securely manage authentication of partners and customers through seamless integration with the AWS Identity and Access Management service. You will also hear from Ping Identity partner and Amazon Web Services Customer, Geezeo. They will share best practices based on their experience.
Again, these webinars are free but I strongly suggest that you register ahead of time for best results!
— Jeff;
AWS CloudTrail Update – Seven New Services & Support From CloudCheckr
AWS CloudTrail records the API calls made in your AWS account and publishes the resulting log files to an Amazon S3 bucket in JSON format, with optional notification to an Amazon SNS topic each time a file is published.
Our customers use the log files generated CloudTrail in many different ways. Popular use cases include operational troubleshooting, analysis of security incidents, and archival for compliance purposes. If you need to meet the requirements posed by ISO 27001, PCI DSS, or FedRAMP, be sure to read our new white paper, Security at Scale: Logging in AWS, to learn more.
Over the course of the last month or so, we have expanded CloudTrail with support for additional AWS services. I would also like to tell you about the work that AWS partner CloudCheckr has done to support CloudTrail.
New Services
At launch time, CloudTrail supported eight AWS services. We have added support for seven additional services over the past month or so. Here’s the full list:
- Amazon EC2
- Elastic Block Store (EBS)
- Virtual Private Cloud (VPC)
- Relational Database Service (RDS)
- Identity and Access Management (IAM)
- Security Token Service (STS)
- Redshift
- CloudTrail
- Elastic Beanstalk – New!
- Direct Connect – New!
- CloudFormation – New!
- Elastic MapReduce – New!
- Elastic Load Balancing – New!
- Kinesis – New!
- CloudWatch – New!
Here’s an updated version of the diagram that I published when we launched CloudTrail:
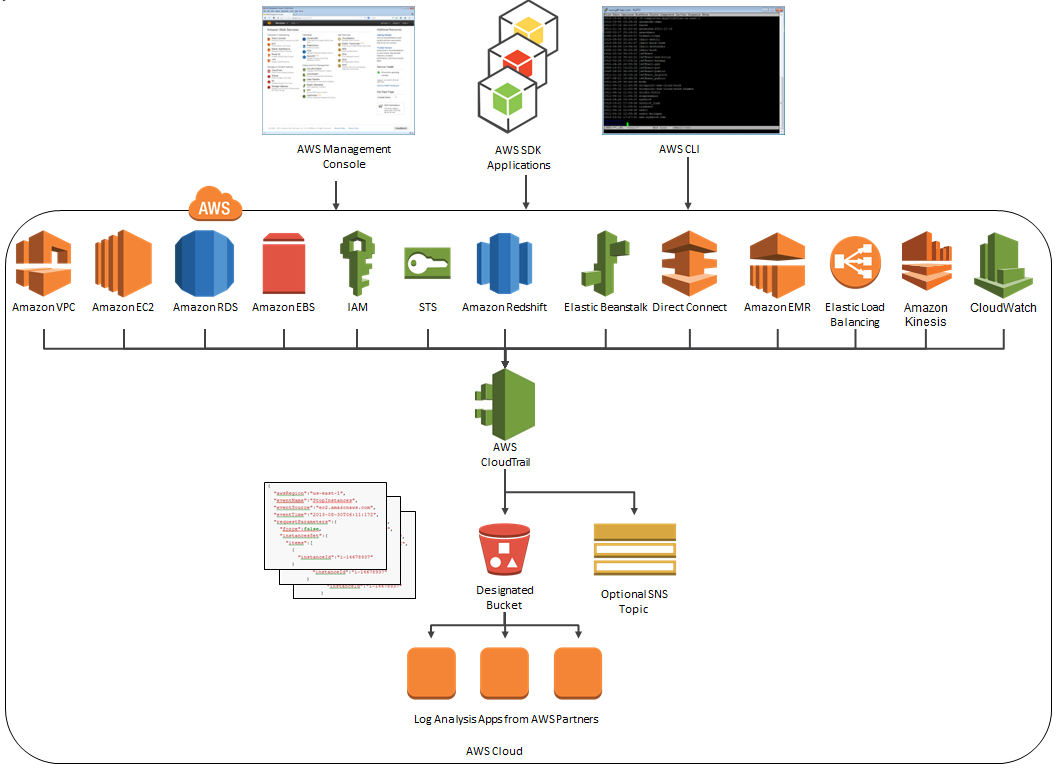
News From CloudCheckr
CloudCheckr (an AWS Partner) integrates with CloudTrail to provide visibility and actionable information for your AWS resources. You can use CloudCheckr to analyze, search, and understand changes to AWS resources and the API activity recorded by CloudTrail.
Let’s say that an AWS administrator needs to verify that a particular AWS account is not being accessed from outside a set of dedicated IP addresses. They can open the CloudTrail Events report, select the month of April, and group the results by IP address. This will display the following report:
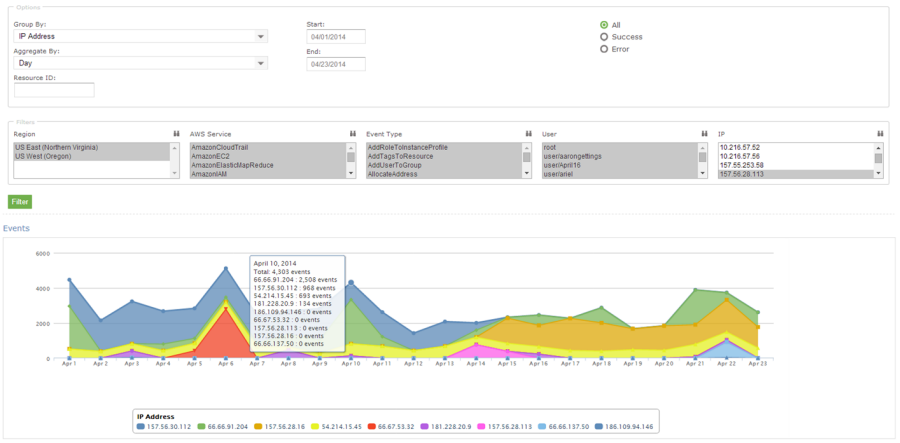
As you can see, the administrator can use the report to identify all the IP addresses that are being used to access the AWS account. If any of the IP addresses were not on the list, the administrator could dig in further to determine the IAM user name being used, the calls being made, and so forth.
CloudCheckr is available in Freemium and Pro versions. You can try CloudCheckr Pro for 14 days at no charge. At the end of the evaluation period you can upgrade to the Pro version or stay with CloudCheckr Freemium.
— Jeff;
