AWS News Blog
New AWS Key Management Service (KMS)
Information security is always of paramount importance, whether data is stored on-premises or in the cloud. Since the early days of AWS, we’ve done our best to provide our customers with the information, services, and features that they need to have in order to make informed decisions about what kinds of applications and what kinds of data they can and should store in the cloud.
I think we can all agree that encryption is one of the principal elements of any data protection strategy. To date we have provided our customers with multiple options including client-side and server-side encryption for Amazon Simple Storage Service (Amazon S3), along with server-side encryption for Amazon Elastic Block Store (Amazon EBS), Amazon Redshift, Amazon RDS for Oracle, and Amazon RDS for SQL Server. Up until now, the server-side encryption support provided by these services has made use of “master keys” that are generated, stored, and managed within AWS.
Today we are adding a powerful new option for key management, one that can manage keys for applications and services running in the cloud as well as on-premises!
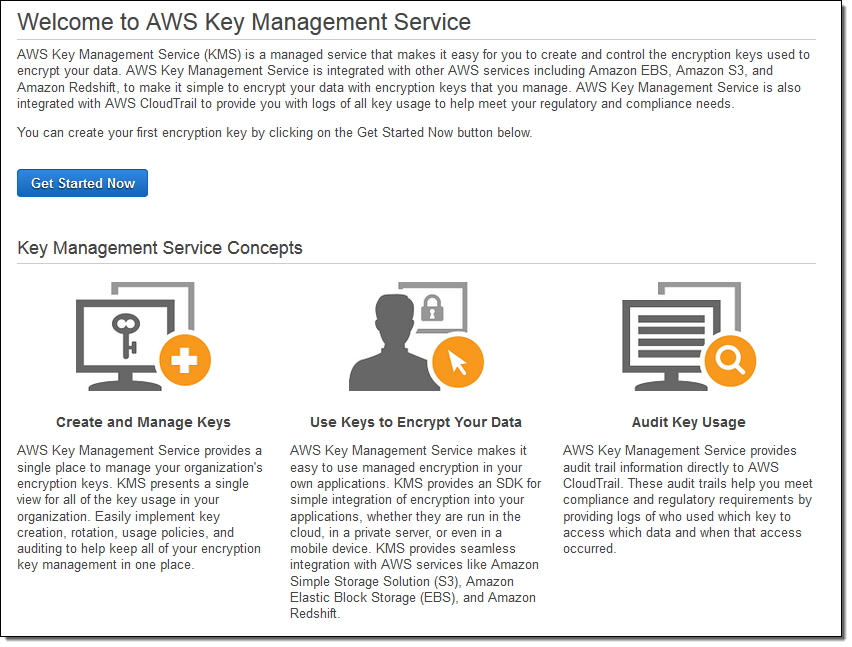
Introducing the AWS Key Management Service (KMS)
The new fully-managed AWS Key Management Service (AWS KMS) provides you with seamless, centralized control over your encryption keys. It gives you a new option for data protection and relieves you of many of the more onerous scalability and availability issues that inevitably surface when you implement key management at enterprise scale. When properly used, AWS Key Management Service can even help to address lingering concerns about moving sensitive data to the cloud.
The service is built on systems that protect your keys with extensive hardening techniques such as never storing keys on disk, not persisting them in memory, and limiting which systems can connect to the device. All access to update software on the service is controlled by a multi-level approval process that is audited and reviewed by an independent group within Amazon. All physical access for maintenance is tightly controlled (multiple, senior-level employees must cooperate) and logged.
S3, EBS, and Redshift can now encrypt data at rest using keys controlled by AWS Key Management Service. You can choose to use the default (master) keys for each service or you can use AWS Key Management Service to create and manage your own keys. You can define keys for each service, application type, or data classification. The service lets you define which master keys protect your data however you choose to organize it. Regardless of the operation that you choose, all of the routine operations on keys (create, rotate, enable, and disable) are accessible from the AWS Management Console and through a set of key management APIs. All operations on keys are logged to AWS CloudTrail. You can use the logs to find out how and when specific keys were used, and which services used them.
In addition to managing keys for AWS services, AWS Key Management Service (AWS KMS) streamlines the process of adding robust, fully-integrated encryption to your AWS and on-premises applications by supplying a rich set of key management and encryption APIs.
Creating Keys Using AWS Key Management Service
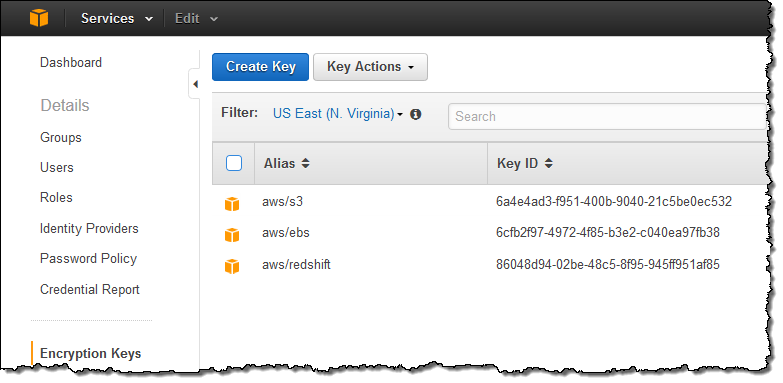
Let’s create a key! I start by opening up the Identity and Access Management Console and clicking on Encryption Keys. At this point I can see my existing keys (KMS created these keys when I opted to encrypt my S3 buckets, EBS volumes, and my Redshift data warehouse):
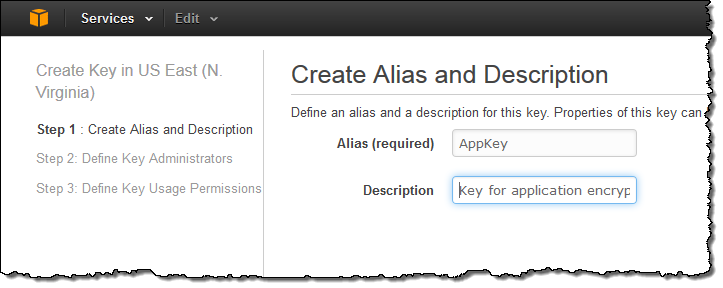
I can click Create Key to start the process of creating a new key. The first step is to define an alias (display name) for the key and to provide a description:
Next, I need to decide who is allowed to administer the new key by choosing one or more IAM users and/or roles:
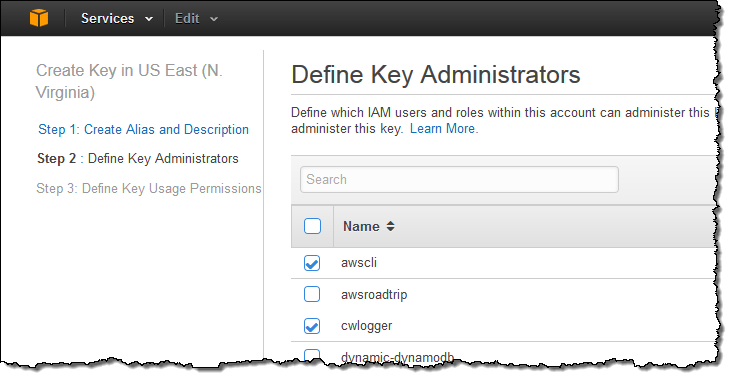
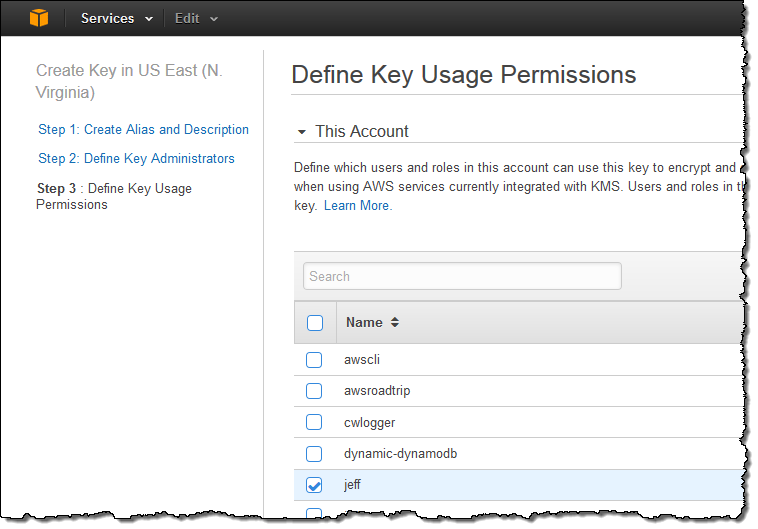
In the third and final step, I decide which users, roles, and other AWS accounts are allowed to use the key to encrypt and decrypt data. The permissions defined in this step apply to direct (API-driven) usage and to usage that originates with an AWS service that is integrated in to KMS:
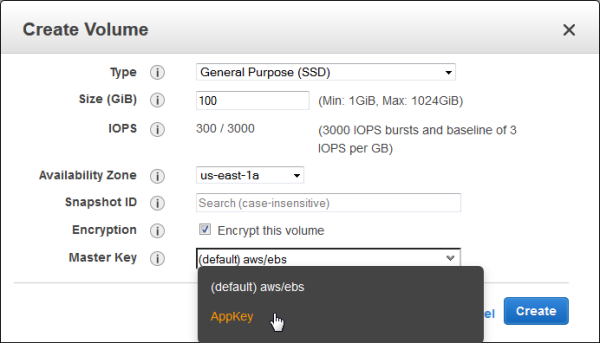
Using Keys with EBS and S3
Now that I have created a key, I can easily use it with any of the AWS services that I mentioned above (and others in the future)! Here’s how I would create an EBS volume that is encrypted with my key:
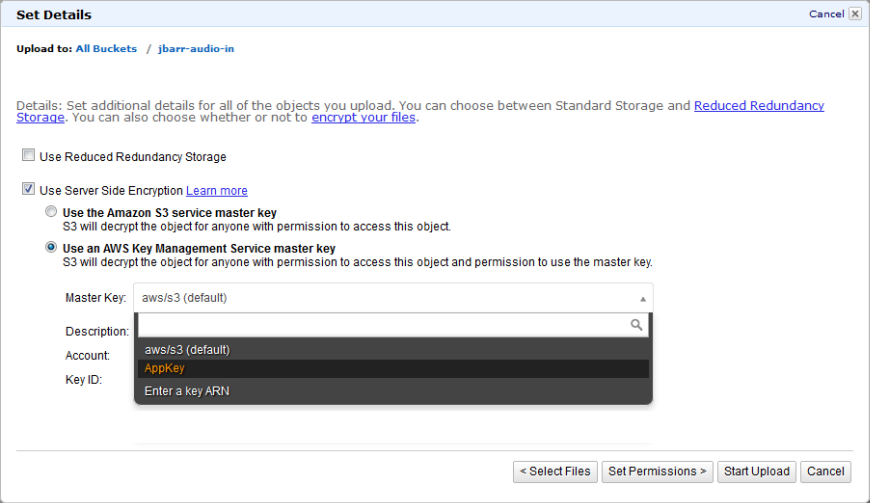
And here’s how I would encrypt an S3 object after it is uploaded:
Managing and Auditing Key Usage
I can also get full information on a key with one click:
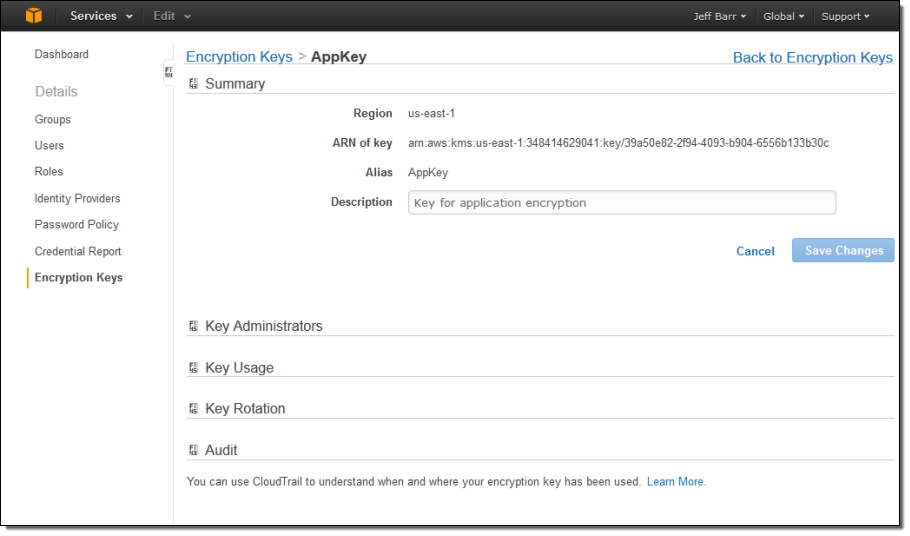
All API requests against a key are logged to AWS CloudTrail so that you can track and understand how, when, and by whom the keys where used.
Key Management APIs
All of the functions that I described above can also be accessed programmatically. You can create, enable, and disable keys. You can use them to encrypt and decrypt your own data and you can enable and disable rotation. Your AWS and on-premises applications can use these APIs for key management and encryption.
New White Paper
If you would like to learn more about the cryptographic operations that are executed within AWS when you use KMS, download and read our new white paper, AWS KMS – Cryptographic Details.
Pricing and Availability
This new service is available now in all public AWS Regions and you can start using it later today (visit the AWS Key Management Service (AWS KMS) page to get started).
You can create, use, and manage keys at $1 per key version per month. API requests to the service cost $0.03 per 10,000 requests. There is a free tier of 20,000 requests per month.
— Jeff;