AWS News Blog
New – Amazon Web Services Extends CloudTrail to All AWS Customers
|
|
I have exciting news for all Amazon Web Services customers! I have been waiting patiently to share this great news with all of you and finally, the wait is over. AWS CloudTrail is now enabled by default for ALL CUSTOMERS and will provide visibility into the past seven days of account activity without the need for you to configure a trail in the service to get started. This new ‘always on’ capability provides the ability to view, search, and download the aforementioned account activity through the CloudTrail Event History.
For those of you that haven’t taken advantage of AWS CloudTrail yet, let me explain why I am thrilled to have this essential service for operational troubleshooting and review, compliance, auditing and security, turned by default for all AWS Accounts.
AWS CloudTrail captures account activity and events for supported services made in your AWS account and sends the event log files to Amazon Simple Storage Service (Amazon S3), CloudWatch Logs, and CloudWatch Events. With CloudTrail, you typically create a trail, a configuration enabling logging of account activity and events. CloudTrail, then, fast tracks your ability to analyze operational and security issues by providing visibility into the API activity happening in your AWS account. CloudTrail supports multi-region configurations and when integrated with CloudWatch you can create triggers for events you want to monitor or create a subscription to send activity to AWS Lambda. Taking advantage of the CloudTrail service means that you have a searchable historical record of data of calls made from your account from other AWS services, from the AWS Command Line Interface (AWS CLI), the AWS Management Console, and AWS SDKs.
The key features of AWS CloudTrail are:
- Always On: enabled on all AWS accounts and records your account activity upon account creation without the need to configure CloudTrail
- Event History: view, search, and download your recent AWS account activity
- Management Level Events: get details administrative actions such as creation, deletion, and modification of EC2 instances or S3 buckets
- Data Level Events: record all API actions on Amazon S3 objects and receive detailed information about API actions
- Log File Integrity Validation: validate the integrity of log files stored in your S3 bucket
- Log File Encryption: service encrypts all log files by default delivered to your S3 bucket using S3 server-side encryption (SSE). Option to encrypt log files with AWS Key Management Service (AWS KMS) as well
- Multi-region Configuration: configure service to deliver log files from multiple regions
You can read more about the features of AWS CloudTrail on the product detail page.
As my colleague, Randall Hunt, reminded me: CloudTrail is essential when helping customers to troubleshoot their solutions. What most AWS resources, like those of us on the Technical Evangelist team or the great folks on the Solutions Architect team, will say is “Enable CloudTrail” so we can examine the details of what’s going on. Therefore, it’s no wonder that I am ecstatic to share that with this release, all AWS customers can view account activity by using the AWS console or the AWS CLI/API, including the ability to search and download seven days of account activity for operations of all supported services.
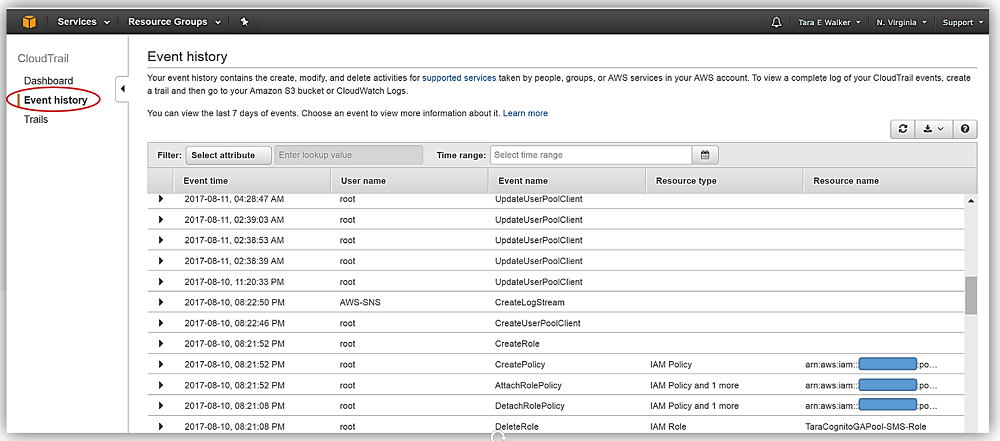
With CloudTrail being enabled by default, all AWS customers can now log into CloudTrail and review their Event History. In this view, not only do you see the last seven days of events, but you can also select an event to view more information about it.
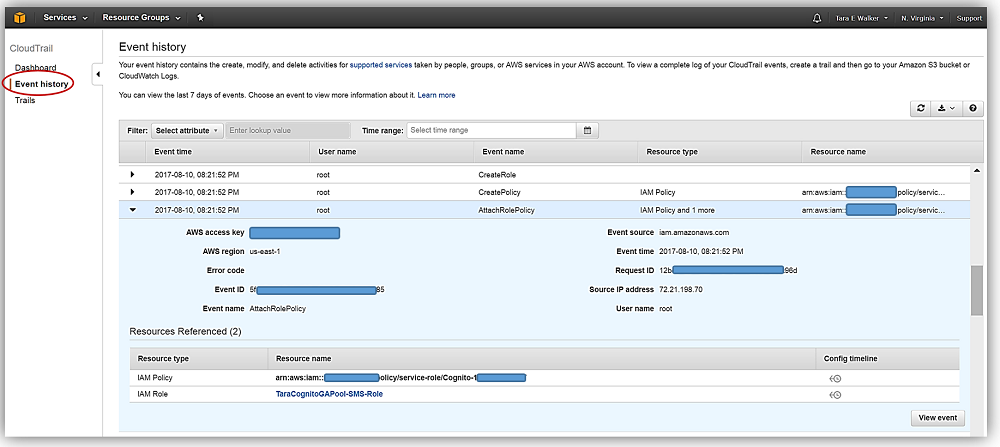
Of course, if you want to access your CloudTrail log files directly or archive your logs for auditing purposes, you can still create a trail and specify the S3 bucket for your log file delivery. Creating a trail also allows you to deliver events to CloudWatch Logs and CloudWatch Events, and is a very easy process.
After logging into the CloudTrail console, you would simply click the Create a trail button.
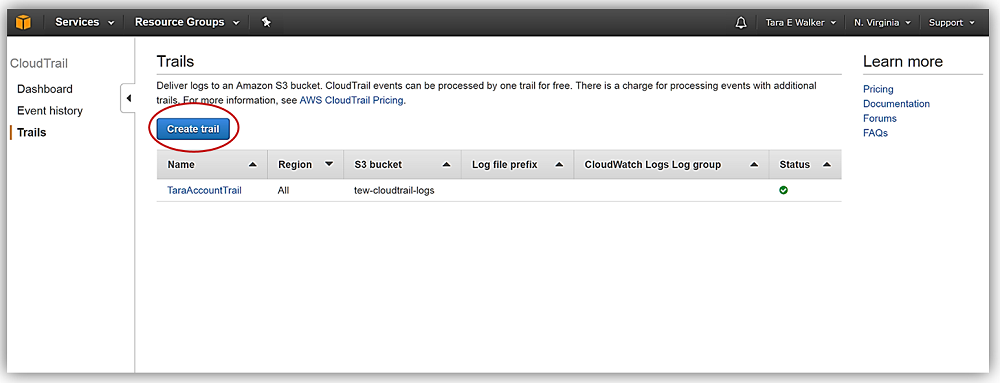
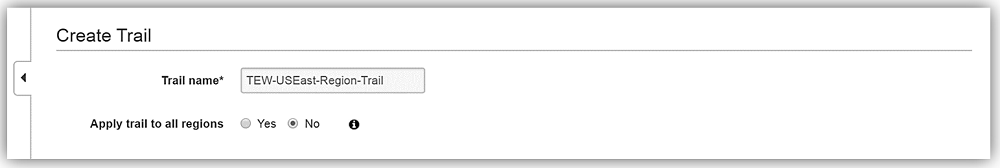
You then would enter a trail name in the Trail name text box and select the radio button for the option of applying your trail configuration to all regions or only for the region you are currently in. For this example, I’ll name my trail, TEW-USEast-Region-Trail, and select No for the Apply trail to all regions, radio button. This means that this trail will only track events and activities in the current region, which right now is US-East (N. Virginia). Please note: A best practice is to select Yes to the Apply trail to all regions option to ensure that you will capture all events related to your AWS account, including global service events.
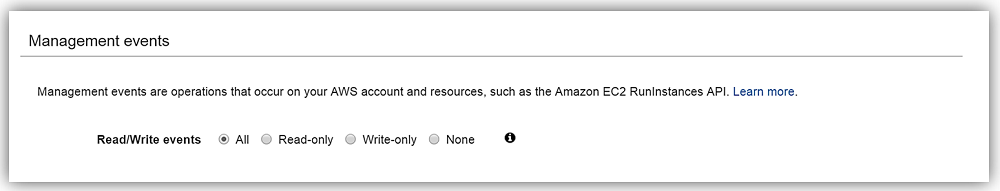
Under Management events, I select the Read/Write events radio button option for which operations I want CloudTrail to track. In this case, I will select the All option.
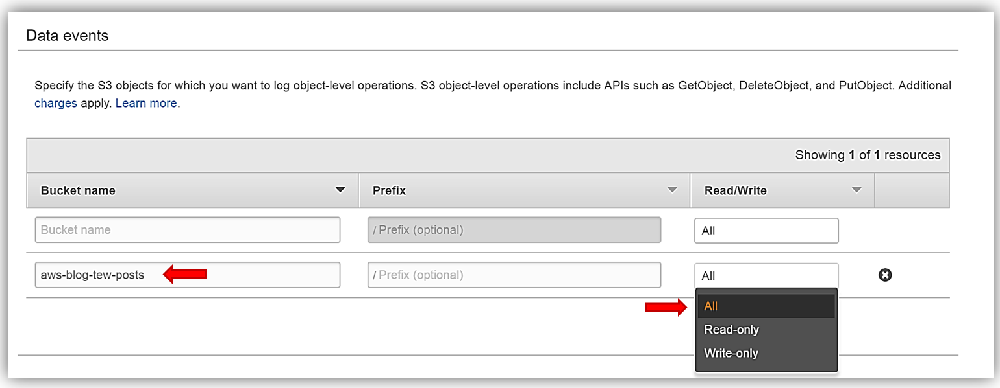
Next step is for me to select the S3 buckets for which I desire to track the S3 object-level operations. This is an optional step, but note that by default trails do not log Data Events. Therefore, if you want to track the S3 object event activity you can configure your trail to track Data Events for objects in the bucket you specify in the Data events section. I’ll select my aws-blog-tew-posts S3 bucket, and keep the default option to track all Read/Write operations.
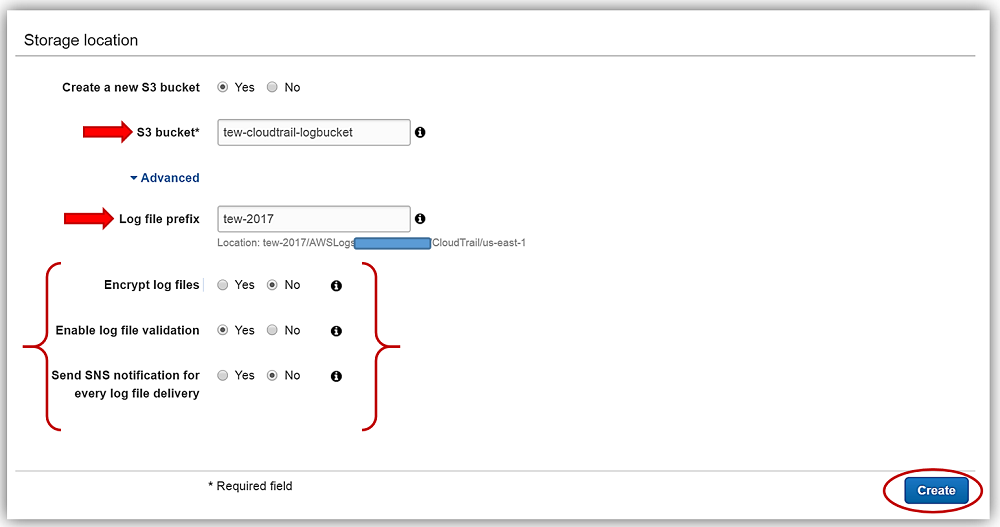
My final step in the creation of my trail is to select a S3 bucket in the Storage Location section of the console for where I wish to house my CloudTrail logs. I can either have CloudTrail create a new bucket on my behalf or select an existing bucket in my account. I will opt to have CloudTrail create a new bucket for me so I will enter a unique bucket name of tew-cloudtrail-logbucket in the text box. I want to make sure that I can find my logs easily so I will expand the Advanced section of the Storage Location and add a prefix. This is most helpful when you want to add search criteria to logs being stored in your bucket. For my prefix, I will just enter tew-2017. I’ll keep the default selections for the other Advanced options shown which include choices for; Encrypt log files, Enable log file validation, and Send SNS notification for every log file delivery.
That’s it! Once I click the Create button, I have successfully created a trail for AWS CloudTrail.
Ready to get started?
You can learn more about AWS CloudTrail by visiting the service product page, the CloudTrail documentation, and/or AWS CloudTrail frequently asked questions. Head over to the CloudTrail service console to view and search your CloudTrail events, with or without a trail configured.
Enjoy the new launch of CloudTrail for All AWS Customers, and all the goodness that you will get from taking advantage of this great service!
– Tara
